Whaling attack: Definition + tips for prevention
Despite what its name suggests, whaling attacks aren’t larger-than-life beasts that are difficult to understand and defeat. Learn what techniques hackers might use to trick senior leadership and how you can use cybersecurity software like Norton 360 with LifeLock Select to help block cyber threats.

In this guide, we’ll help you understand the different whaling attack techniques hackers are using in 2024, share tips for identifying scams, and instructions for what to do if your organization is ever under attack.
What is a whaling attack?
A whaling attack is a type of phishing scam where hackers deceive high-ranking people (think C-level executives like CEOs and CFOs or key decision-makers) to achieve financial gain, access sensitive data, or coerce the organization into taking a specific action.
You may also hear whaling referred to as executive phishing, CEO fraud, or C-level scams.
What is the difference between phishing, whaling, and spear phishing?
Phishing is a broad term that encompasses whaling and spear phishing. In both scenarios, hackers use similar approaches to trick users into voluntarily handing over private information.
The key to understanding the difference lies in who the cybercriminals are targeting. Here’s how you can tell the difference between phishing, whaling, and spear phishing:
- Phishing attacks target large groups of people without any rhyme or reason.
- Spear phishing attacks target specific groups of people or individuals.
- Whaling attacks target major players at large, profitable businesses.
Whaling attack example
As an example, let’s look at the impact a 2020 whaling attack had on Australian hedge fund, Levitas Capital:
How do whaling attacks work?
A whaling attack is a type of social engineering attack where a hacker steals the identity of a respected individual or business to gain the trust of their target—usually a high-ranking employee or business owner. Once they “earn” their targets' trust using someone else’s social capital, they can convince them to hand over valuable information. Ultimately, this can result in devastating consequences such as lost revenue, heightened customer distrust, and corrupt business records.
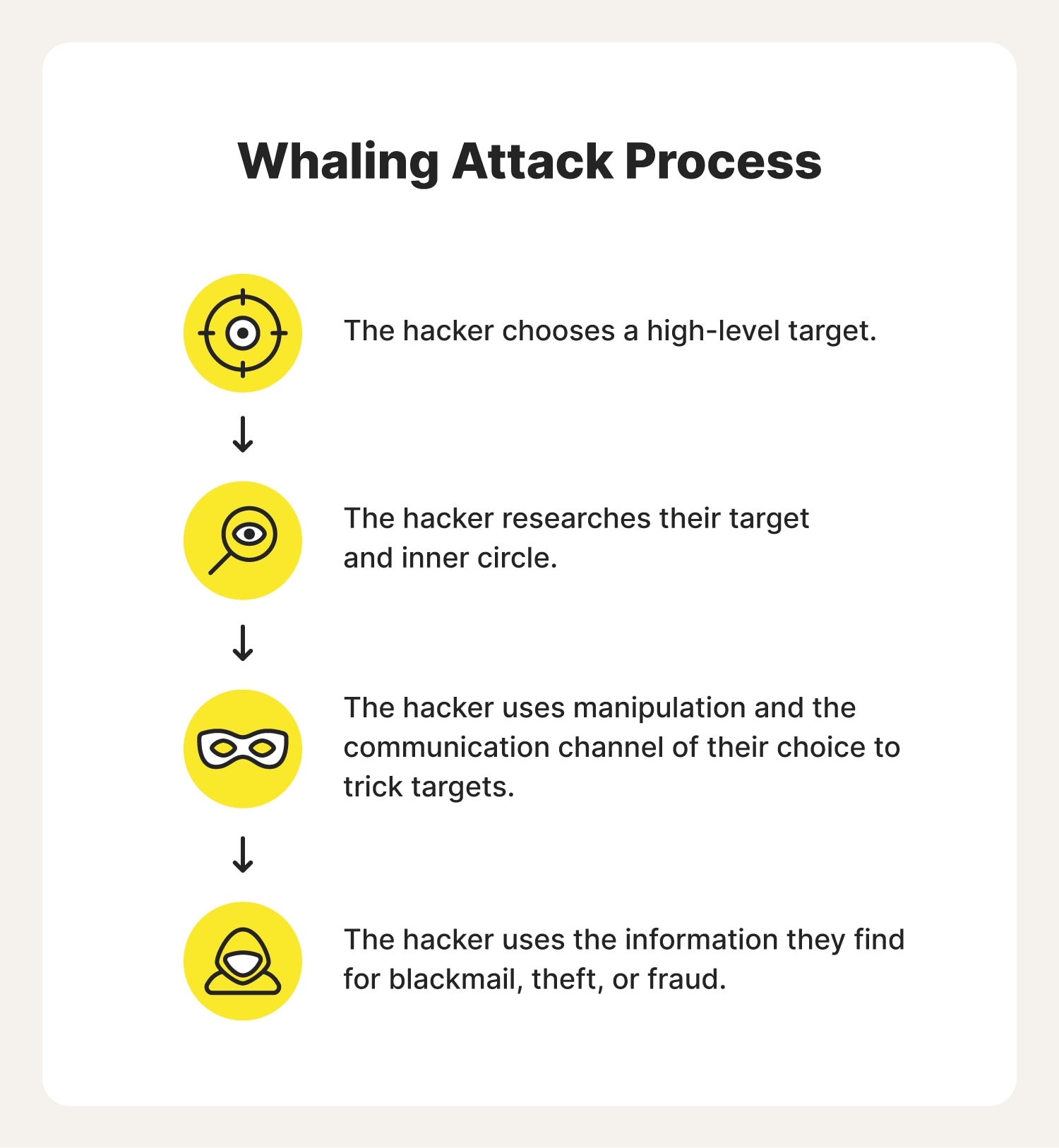
Here’s a breakdown of how whaling attacks work:
1. Hackers identify a high-profile target: A hacker identifies a top executive who is likely to have the information or money they want.
2. Cybercriminals do research: The scammer gathers information about their target using social media and other public platforms. During this process, they learn more about the target and their inner circle and determine the most effective way to trick them.
3. Attackers craft a convincing message: The hacker usually spoofs the email account of a trusted sender so their target won’t think twice about opening the email or any attachments. However, they may also communicate through phone calls, social media DMs, and text messages.
4. Cybercriminal tricks their target: Once the hacker tricks their target and obtains money or information, they can commit fraud, distribute trade secrets, blackmail the company, and more.
3 common whaling attack techniques
A lot of people think of whaling as an attack that mostly happens over email because of its similarity to phishing. However, hackers can actually use whaling attack techniques via:
- Social media
- Phone calls
Here’s what you need to know about whaling attacks on each of these platforms to keep scammers from pulling a fast one on you:
1. Whaling via email
Millions of phishing emails are sent each year and many are used as a part of whaling attacks. In 2022, this resulted in over half a million in losses throughout the U.S.
After making a thoughtfully crafted fake email layout; hackers use the credibility of other businesses to trick high-level employees into sending over confidential data or completing unauthorized wire transfers.
- Whaling prevention tip: Confirm urgent requests by contacting the sender via alternate communication channels.
2. Whaling via social media
Social media can be great for those looking for information—but not so great for people looking to hide it. When executives create Instagram or Facebook accounts, they should be aware of the information they make public. Hackers often use professional profiles to find work emails they can repurpose for their whaling efforts.
- Whaling prevention tip: Secure your social media accounts and avoid listing your work email, full name, or personal information online to stop hackers from tricking you or stealing your identity to dupe others.
3. Whaling via phone calls
This is a newer technique where hackers follow up on whaling emails with a phone call. If they answer, the hacker attempts to verify that the targeted employee received their email and emphasizes the importance of the request made in their message.
- Whaling prevention tip: Verify urgent requests with a colleague who is familiar with the project.
Tips for recognizing a whaling attack
Identifying a whaling attack can be challenging because scammers usually spend a lot of time getting to know their targets, which allows them to perfect their ruse. However, hackers are human, too, and they aren’t infallible. Here are a few red flags you can keep an eye out for if you receive a suspicious message:
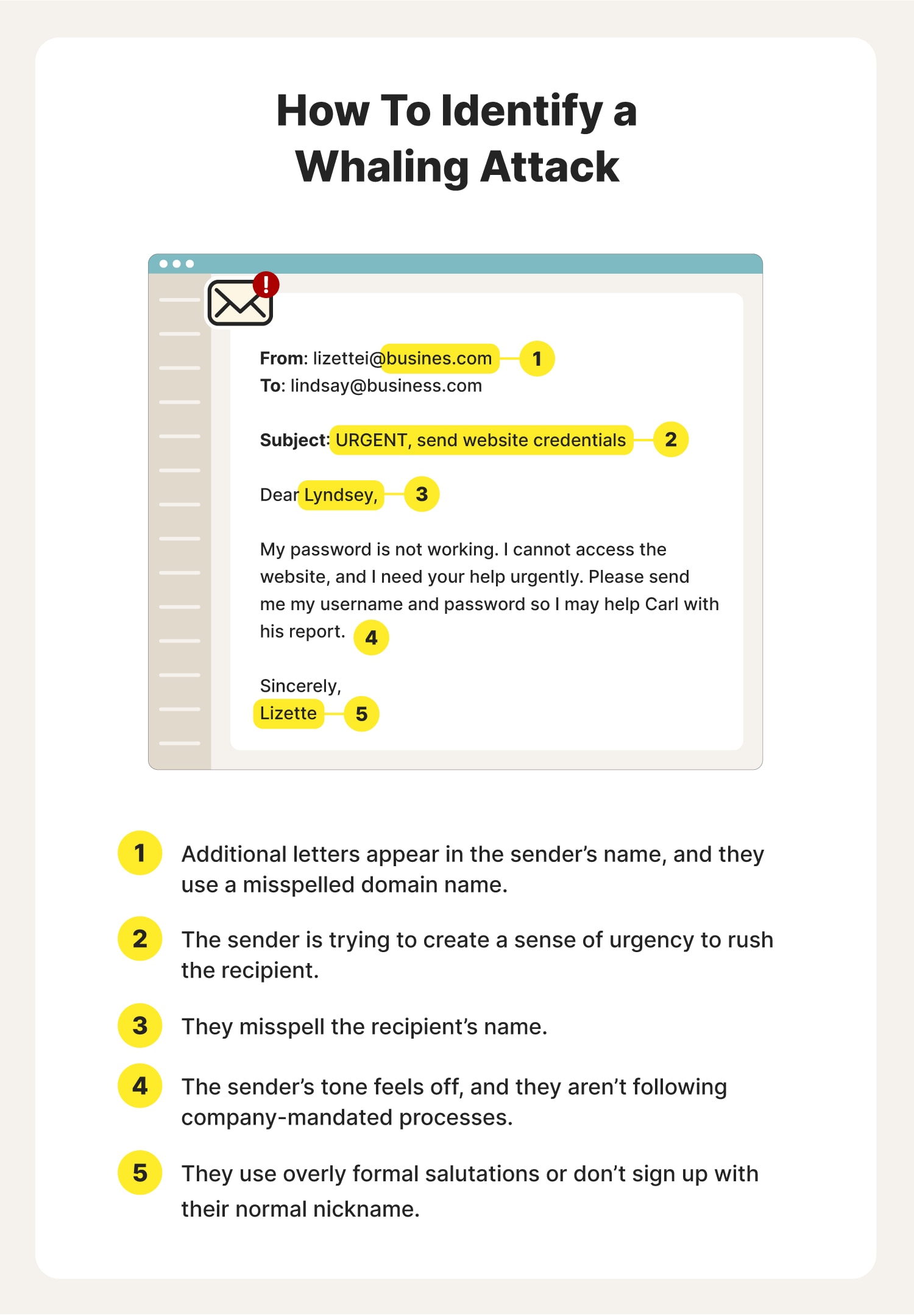
- Check for a correct email address: One of the easiest ways to identify a whaling attempt is to closely examine the sender’s email address. If it’s a scam, the sender’s name is often misspelled, or you may see an unfamiliar domain.
- Don’t fall for a sense of urgency in the subject line or body: Don’t get swept away by a sender’s urgent tone. Some attackers use this language to get recipients to act quickly and without thinking.
- Inspect the email for oddities and poor grammar: Be wary of emails that address you by the wrong name or title. Also, scammers often use generic greetings like "Dear User" or "Hello." Meanwhile, someone you work with often is more likely to speak casually or use nicknames. Poor grammar, unusual language, or a lack of familiarity with industry-specific terms are signs that you are talking to a scammer.
- Be aware of suspicious requests: Make sure the request makes sense. If the sender asks for information above their pay grade or they’re not following protocol, slow down and verify that they are who they claim to be.
- Verify requests carefully: If you receive a request for personal, financial, or login information—don’t provide it via email. In most cases, there is a more secure way to share those details with legitimate employees, customers, and stakeholders.
- Inspect (don’t click) links and attachments: Avoid clicking on links or downloading attachments from suspicious emails. Hover over links to preview the URL before clicking to make sure attachments are safe.
- Review the sender's signature and background: Legitimate business emails often include a professional signature with the sender's name, title, and contact information. This is one sign that the sender is credible because you can look them up on professional networking sites to assess their reputation. While a lack of a signature isn’t a warning sign on its own, you should consider its legitimacy when combined with the warning signs mentioned above.
9 ways to protect yourself from whaling attacks
If you are a victim of a whaling attack, there are things you can do to resolve the situation. However, it’s best to take a proactive approach to preventing phishing scams altogether. Here are a few things you can do to lower your chances of getting caught up in a whaling scam.

1. Vet requests carefully
Carefully evaluate the contact information of anyone who contacts you requesting payment, confidential information, or access to files. Even if the person appears to work at the same company as you, you should take the time to assess their name, email, and their request to confirm that you aren’t dealing with a sophisticated phishing scheme. This is the best way to protect yourself and the company you work for from whaling attacks.
2. Require employees to attend cybersecurity training
Provide comprehensive and ongoing employee training in data security and cyber safety to ensure whaling and phishing attacks don’t slip through the cracks. When your entire workforce is informed about cybercriminals' various tactics to compromise data and systems, it’s harder for scammers to successfully trick employees, especially high-level ones, into sharing confidential information.
3. Install antivirus software
Antivirus and security software can help keep business networks safe by detecting and blocking malicious emails, monitoring devices for unusual behavior, and offering security features like multi-factor authentication. When combined, these features can reduce the risk of high-ranking executives falling for whaling scams and protect the organization from potential financial loss and data breaches.
Use Norton AntiVirus Plus to help block malware and account takeover attempts.
4. Create data protection policies
Your company should create well-defined policies for handling, sharing, and sending sensitive data. It should also specify who can access what data and under what circumstances. Policies should also instruct employees to avoid sending files to personal email accounts and require them to use a mobile VPN when accessing sensitive data on public Wi-Fi networks. This will make it more difficult for attackers to deceive high-ranking executives or employees into disclosing confidential information.
5. Don’t create unnecessary accounts
You may surprise yourself when you realize how much of your information is online. Every time you post on social media or fill out a personality quiz on the internet, more of your personal information gets put on the web. And before you know it, hackers know enough about you to compile your information to sell on the dark web for profit.
Avoid this by only signing up for social media platforms, apps, and other online accounts that you intend to use regularly.
6. Protect personal information
Keeping your personal information safe is key to avoiding whaling attacks and other phishing scams. By not oversharing on social media—and even company online bios—you can make it more difficult for phishers to access your data.
You also can change your privacy settings on your devices and online accounts to ensure only specific people can view your information. In case some executives are unaware of how to protect themselves online, companies should guide employees on how to protect their identity and personal information on social media to limit exposure to prying eyes.
7. Update software regularly
Ensure the devices you use daily are up to date on the latest security patches that help prevent hackers from using whaling to compromise your devices and information. A good trick is to enable automatic updates to take the work out of remembering to check regularly.
8. Implement email authentication
Use email authentication protocols like DMARC (Domain-based Message Authentication, Reporting, and Conformance) to help verify senders and identify spoofed emails. Protocols like this help ensure the messages that reach high-ranking executives are legitimate, reducing the risk of deception and protecting against financial loss, data breaches, and reputational damage.
9. Use multi-factor authentication
Multi-factor authentication (MFA) adds an extra layer of security to the authentication process. It requires users to provide at least two forms of verification, such as something they know (like their password) and something they have (like their cell phone). This makes it harder for scammers to break into your business’s network, even if they successfully dupe a high-ranking exec and obtain their login credentials.
What can happen if a hacker targets me in a whaling attack?
Since whaling attacks target high-profile people like executives, the information they steal tends to be extremely sensitive which can lead to more serious consequences like:
- Financial loss
- Data breaches
- Identity theft
- Reputational damage
- Legal action
- Business disruption
- Extortion
- Loss of intellectual property
- Corporate espionage

What to do if you click a suspicious link
Clicking on a link that turns out to be a whaling attack can create a lot of problems. If you do click a malicious link, here are some things you can do to limit the damage:
- Disconnect from Wi-Fi: Shutting off your Wi-Fi or disconnecting your Ethernet cable can help stop the spread of infectious malware.
- Reset your passwords: If a hacker can gain access to one of your accounts, they may find their way into others. If you believe a hacker has compromised one of your online accounts, reset all your passwords immediately. Use long and unique passwords and consider enabling multi-factor authentication if you haven’t already.
- Scan device hardware: Use cybersecurity software to scan, identify, and destroy dangerous malware hiding in your system. If it’s unable to remove the malware from your device, you can still share the security report with your IT person to save time on troubleshooting.
- Restore your data: In the best-case scenario, you can restore your data if you saved it in the cloud or on an external hard drive. However, if that isn’t the case for you, you can talk to an IT specialist about your recovery options.
- Make a report: If your IT expert could not remove the malware, or you need to file a report, contact local law enforcement. Chances are they will be able to escalate your case, find a solution, and possibly track down the scammer.
Cybersecurity tools that can withstand any whaler’s harpoon
Using the information and tips provided here can make noticing a whaling attack easier than spotting a humpback in the Pacific. After all, preventing whaling attacks starts with securing your company’s network and your team’s devices.
But that’s not all you can do—invest in cybersecurity software that can alert you to phishing attacks early and help block malicious threats. Norton 360 with LifeLock Select can help protect your devices, block hackers, and stop account takeovers—helping to keep your digital life safe.
FAQs about whale phishing attacks
Here are answers to some of the most frequently asked questions about whaling attacks.
Who do hackers target in whaling attacks?
Whaling attacks target high-profile company executives, such as CEOs and CFOs. However, hackers sometimes leverage a tactic called “lateral phishing,” where they use their true target’s colleagues or lower-ranking employees as a stepping stone to reach the final boss.
How do hackers choose their targets for whaling attacks?
Hackers choose whaling attack targets based on roles, authority, and available information, often focusing on high-ranking individuals in specific industries. To lower your chances of being targeted, educate employees about cybersecurity, enable multi-factor authentication, and implement strong password practices while minimizing public information about high-ranking individuals. You should also have crystal-clear processes for approving access to sensitive data or platforms.
What is the purpose of a whaling phishing attack?
A whaling phishing attack aims to deceive high-ranking executives or individuals of authority within an organization to achieve financial gain, access sensitive information, leverage their authority, or exploit their trust and influence for malicious purposes.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.







Want more?
Follow us for all the latest news, tips, and updates.