DDoS: What is a Distributed Denial of Service attack?
DDoS attacks that paralyze host servers are every website admin’s worst nightmare. This article will explain what DDoS attacks are, how they work, and what the common warning signs are. And get Norton 360 Deluxe for powerful online security to help block hacking and protect against DDoS attacks.

What is a DDoS attack?
A DDoS attack is a type of hacking attack that aims to disrupt the normal operations of a targeted server, service, or network by flooding it with internet traffic. Overwhelmed with traffic, the server or network can no longer handle normal requests, which causes it to significantly slow down or crash altogether.
How does a DDoS attack work?
DDoS attacks simultaneously flood a targeted server, network, or website with a vast amount of traffic from multiple sources to overwhelm the target's capacity to handle requests. That causes the network or website to crash or become inaccessible to legitimate users.
The devices that DDoS attacks compromise are often referred to as "bots,” “botnets,” or "zombies," which the attacker controls. These attacks typically leverage multiple attack vectors at once.
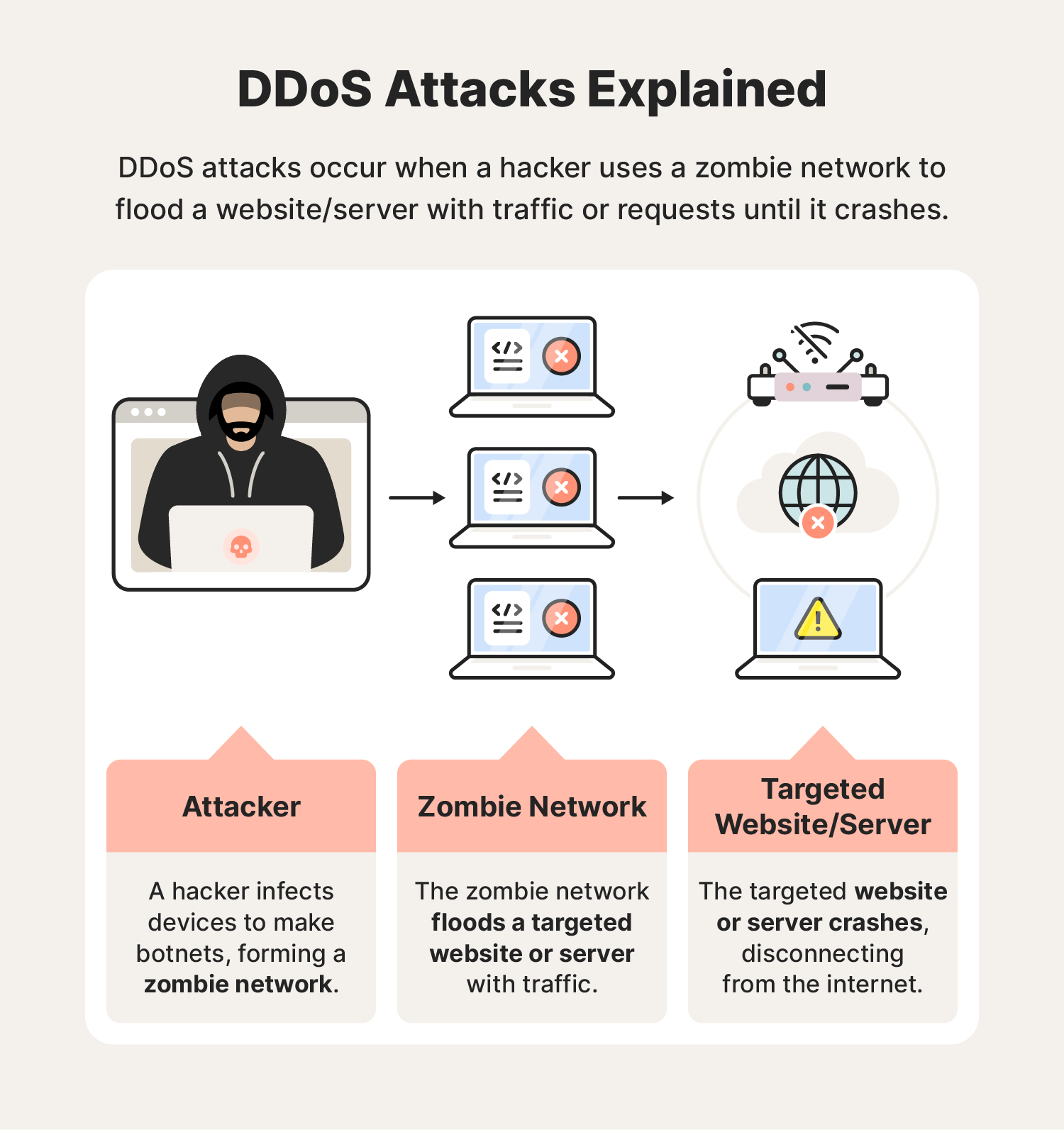
By harnessing the combined computational power of many compromised devices, DDoS attackers can amplify the impact of their assaults, causing widespread disruption and downtime.
DoS vs. DDoS
While DoS and DDoS attacks are both types of cyberattacks that seek to overwhelm and crash servers and websites by flooding them with traffic, the difference is the source of the attack.
There’s more differentiating DDoS attacks from DoS (denial of service) attacks besides the absence of an extra letter — but the word “distributed” does get to the crux of the issue. Here are the key distinguishing factors:
DoS attacks
- Use a single corrupt device to flood a targeted website.
- Typically target one specific victim, server, or network.
DDoS attacks
- Use zombie networks or botnets to flood a targeted website.
- Target businesses or larger networks to affect more users and cause widespread damage.
Reasons for launching a DDoS attacks
The motivations behind DDoS attacks are diverse, ranging from political activism to personal vendettas and economic competition. Here are the main reasons that DDoS attacks are launched:
- Hacktivism: DDoS attacks may be a form of digital protest against perceived injustices or political agendas.
- Cyber vandalism: Some individuals engage in DDoS attacks purely for the sake of causing disruption and damage to online services or infrastructure.
- Extortion: Cybercriminals may launch DDoS attacks to extort money from businesses or individuals by threatening further attacks if they don’t meet ransom demands.
- Business competition: Competing businesses may resort to DDoS attacks to gain a competitive edge by disrupting their rivals' online presence and operations.
- Cyber warfare: Nation-states and state-sponsored actors may use DDoS attacks as a tactic in cyber warfare campaigns to destabilize adversaries and disrupt critical infrastructure.
- Personal rivalry: Individuals with personal grievances or vendettas may use DDoS attacks to target specific individuals, organizations, or online communities.
Whether driven by ideology, profit, or personal vendettas, the prevalence of DDoS attacks underscores the diverse and complex motivations behind threats to cybersecurity in today's interconnected world.
DDoS botnets
Hackers accomplish DDoS attacks primarily through a network of remotely controlled, hacked computers called botnets. These infected devices form so-called “zombie networks” that flood targeted websites, servers, and networks with more data than they can handle.
Botnets can range from thousands to millions of computers controlled by cybercriminals. And they use them for a variety of purposes, including sending spam and different forms of malware or types of ransomware.
DDoS botnets are networks of compromised devices—such as computers, servers, IoT devices, or even smartphones—that have been infected with malware and are under the control of a malicious actor.
Types of DDoS attacks
Beyond the basics of what they are and how they work, knowing about some of the different types of DDoS attacks can help you enhance your personal cybersecurity.
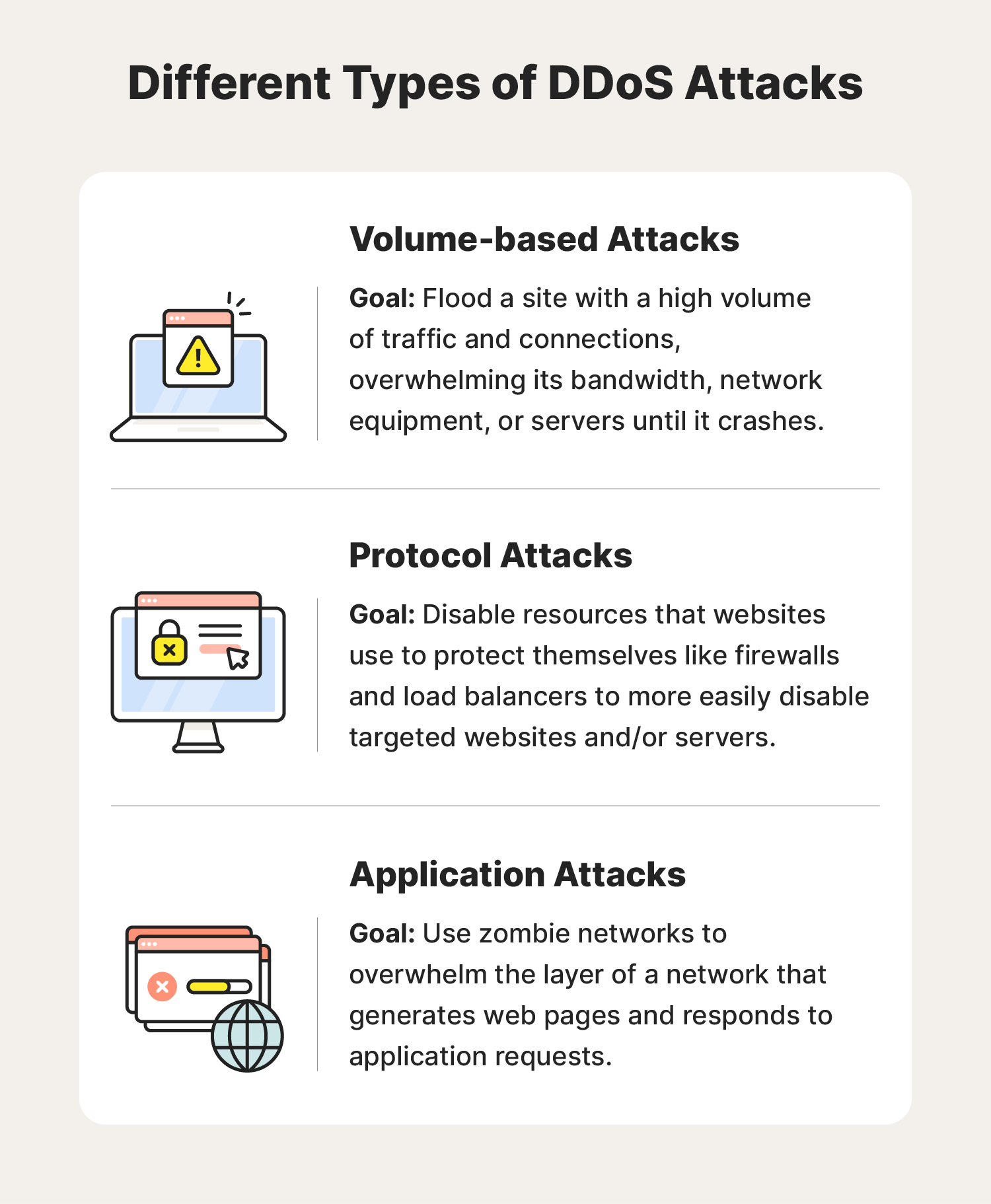
Application layer attack
Application layer attacks—sometimes called Layer 7 DDoS Attacks—regularly target popular applications. A popular attack technique includes HTTP floods, which work by:
- Sending requests: The attacker uses a large number of devices or bots to send HTTP requests to a target server.
- Overwhelming a server: These requests flood the server, overwhelming its capacity to handle incoming connections and process requests.
- Denying service: The server can no longer respond to legitimate user requests due to the flood of malicious traffic.
- Disrupting service: The targeted website or service experiences downtime or becomes extremely slow, disrupting its normal functioning.
- Impacting businesses or services: Users may encounter difficulties accessing the website or service, leading to potential loss of revenue for businesses or inconvenience for users.
An application layer attack may initially appear as legitimate requests from users until it is too late, leaving the victim unable to operate their device.
Examples: HTTP floods and Slowloris attacks
Protocol attacks
Hackers created protocol attacks like the ping of death to target the resources websites use to protect themselves, such as firewalls and load balancers. By disabling these tools, hackers can have a straight shot into the server or website they’re trying to disable.
Examples: SYN floods and ICMP floods
Volumetric attacks
Volume-based attacks, like UDP (User Datagram Protocol) floods, typically come to mind when people bring up DDoS attacks. These common DDoS attacks flood a site with a high volume of connections, overwhelming its bandwidth, network equipment, or servers until it can’t process the traffic and crashes.
Example: UDP floods and DNS amplification attacks
DDoS attack examples
Statistics show DDoS attacks aren't going away anytime soon. In fact, the volume of DDoS attacks hit an all-time high in 2023. Here are some examples of previous DDoS attacks:
- Mafiaboy, 2000: A 15-year-old hacker carried out a DDoS attack on university servers, allowing him to compromise their network and crash major sites, such as CNN, Amazon, Yahoo, and eBay.
- ProtonMail, 2015: A Swiss encrypted email provider paid over $6,000 in Bitcoin to hackers after its site crashed due to hackers using a combination of different DDoS attacks.
- Dyn, 2016: Hackers used malware to create a zombie network from smart TVs, printers, baby monitors, cameras, and other IoT devices. They then carried out DDoS attacks to compromise sites like Twitter, the Guardian, Netflix, Reddit, and CNN.
- Amazon, 2020: Hackers carried out a DDoS attack over three days to try and crash Amazon Web Services operating systems. Their attempt was unsuccessful.
- Ukraine, 2022: Ukrainian officials reported multiple DDoS attacks by Russian hackers targeting Ukrainian government resources and websites.
- Google, Cloudflare, Amazon, 2023: Three of the world's biggest internet companies reported the largest DDoS attacks in their history, warning of a new vulnerability in the HTTP network protocol that hackers were exploiting.
Now that you know how dangerous DDoS attacks can be and how far they can reach, let’s take a look at how to help prevent DDoS hackers from making their way onto your network.
DDoS attack warning signs
DDoS attack warning signs often mimic other potential issues with your computer, ranging from a slow internet connection to a website appearing down. That can make it hard to determine whether you’re experiencing a DDoS attack without a professional diagnosis.
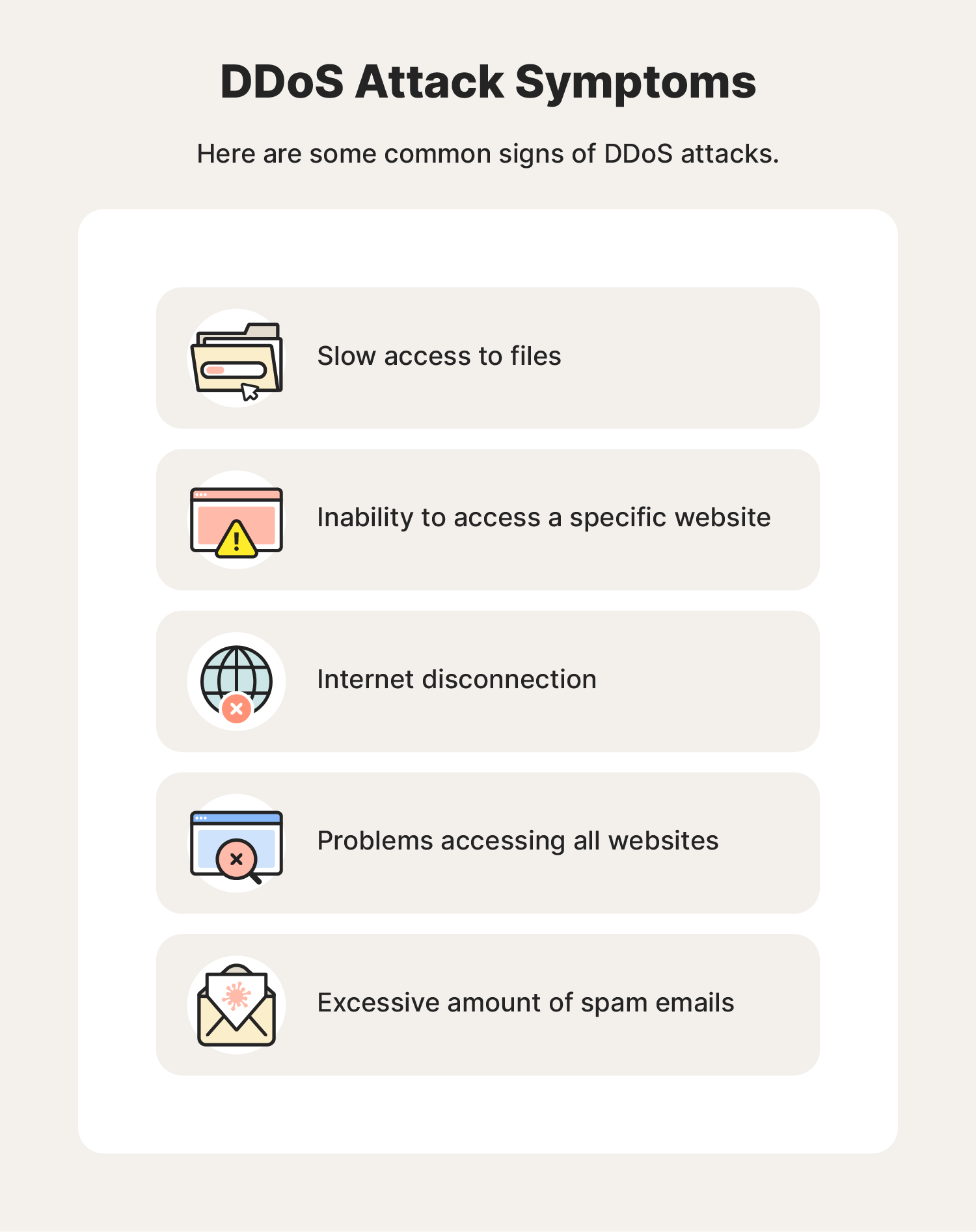
Some of these warning signs of a DDoS attack include:
- Slow file access: Significant file loading or downloading delays may signal a DDoS attack overwhelming your resources.
- Persistent website inaccessibility: If you can't access a specific website for an extended period, it might be under a DDoS attack.
- Internet disconnections: Repeated and sudden internet disconnections could indicate a DDoS attack disrupting your connection.
- Difficulty accessing websites: Widespread internet slowdowns or difficulty accessing multiple sites may suggest a DDoS attack.
- Surge in spam emails: An influx of spam emails could accompany a DDoS attack, aiming to overwhelm your email server.
Again, most of the symptoms above could be the result of one of a wide range of problems. Even so, if two or more occur over a long period, you might be a victim of a DDoS attack.
DDoS mitigation
DDoS mitigation encompasses a range of proactive measures to safeguard networks, servers, and online services from sensitive data exposure and the disruptive effects of these types of attacks.
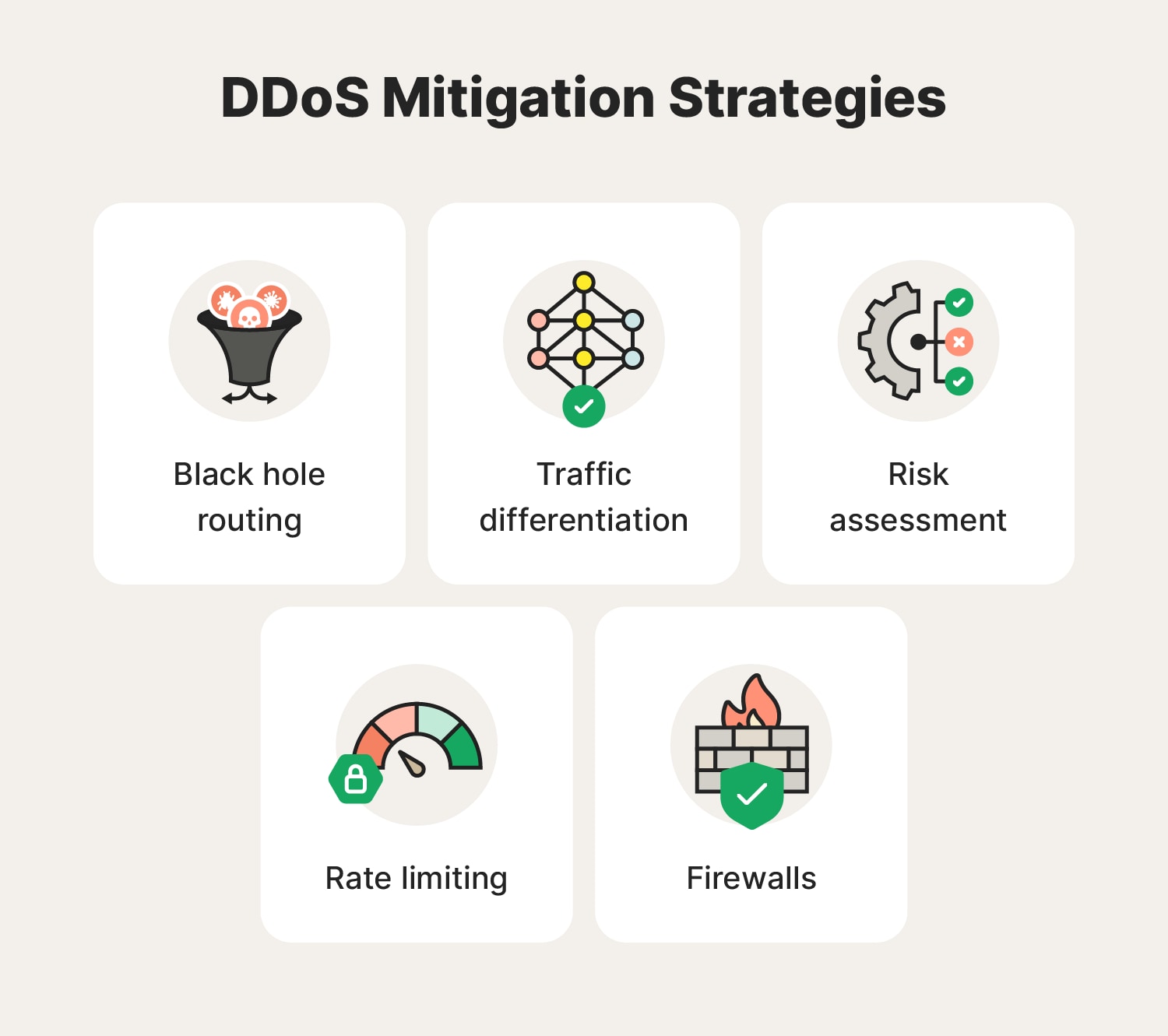
Black hole routing
Black hole routing directs DDoS traffic to a null route, effectively creating a "black hole" where it discards malicious traffic. While this strategy prevents harmful traffic from reaching the target, it may inadvertently affect other network traffic if not executed with precision.
Traffic differentiation
Traffic differentiation leverages traffic analysis to separate legitimate and malicious traffic. By distinguishing between the two, targeted filtering or prioritization can be applied by network administrators, enabling the mitigation of DDoS attacks while minimizing disruption to genuine users.
Risk assessment
Conducting risk assessment helps identify vulnerabilities within a network’s infrastructure. This proactive approach aids in prioritizing mitigation efforts and allocating resources effectively, thereby reducing the likelihood and impact of DDoS attacks.
Rate limiting
Rate limiting restricts the volume of requests or connections from a single source. By limiting traffic, this measure prevents the target from being overwhelmed by excessive requests. However, it necessitates careful calibration to avoid inadvertently obstructing legitimate users' access.
Firewalls
Firewalls act as gatekeepers with predefined rules for filtering incoming and outgoing traffic. While they can block known malicious IP addresses or patterns, they may struggle against large-scale DDoS attacks due to their finite capacity. Nonetheless, they remain a fundamental element of network security infrastructure.
How to avoid DDoS attacks
Take proactive cybersecurity measures to help keep your devices protected and avoid being targeted by DDoS attacks. Here are some of the most effective tips to help protect against DDoS attacks and other hacking threats.
Use a VPN
Using a VPN—whether gaming with friends or shopping online— is a powerful way to ensure online privacy. VPNs work by masking and encrypting your IP address and other identifiable network signatures to help block disruptions to your web activity.
Update apps and security software
Application attacks are when cybercriminals use outdated apps and security flaws to carry out DDoS attacks. To help avoid this cyberthreat, keep your security systems and apps up to date. Software updates often include patches that fix system vulnerabilities that DDoS hacking attacks could expose.
Beware of phishing
Besides being one of the most prominent cyberattacks today, phishing is also a common precursor or symptom of DDoS attacks. If you notice potential phishing scams in your inbox, report them. The FTC reviews reports sent to reportphishing@apwg.org. And if you receive a smishing text message, you can send it to SPAM (7726).
Protect your IP address
Some would say an IP address is just as sensitive as a Social Security number, because it’s a combination of numbers that can specifically identify you—or, in this case, your computer. DDoS hackers may try to track your IP address to find the best way to expose your computer to malware and add you to their zombie network.
Like SSNs, it's best not to share your IP with others. And if you think it fell into the wrong hands, some internet providers will let you change it. Simply log into your service provider and follow their instructions.
Install antivirus software
Since hackers typically use different types of malware to first build zombie networks during a DDoS attack, having antivirus software installed on your devices is essential. Strong cybersecurity software will help protect you against the kinds of malware attacks that DDoS hackers can use.
DDoS attacks may not be one of the newer cyberthreats around, but that hasn’t stopped them from causing widespread disruption. Practice good digital hygiene to elevate your DDoS hacking protection and ensure the Cyber Safety of your devices and online privacy.
Prevent DDoS attacks with enhanced cybersecurity
Investing in comprehensive cybersecurity solutions like Norton 360 Deluxe can help safeguard against DDoS attacks and other cyber threats. With real-time anti-malware protection and a Smart Firewall that blocks suspicious network traffic, you can help minimize the risk of DDoS attacks and maintain the resilience of your digital services.
FAQs about DDoS
Round out your knowledge of DDoS attacks by looking through frequently asked questions.
What causes a DDoS attack?
A DDoS attack occurs when a hacker uses a network of infected devices (called botnets) to flood a specific server or website with requests until it crashes.
How long do DDoS attacks last?
DDoS attacks can vary significantly in duration, ranging from a few minutes to several days—or even longer. In rare cases, DDoS assaults may span multiple days, severely impacting the targeted organization's operations.
Who invented DDoS?
Michael Calce invented and performed the first DDoS attack at the age of 15, hacking into several university websites and crashing major sites, including Amazon, CNN, eBay, and Yahoo.
What is DDoS in gaming?
DDoS attacks can affect online gamers by preventing them from accessing online video games and streaming platforms. They can also hinder a player’s performance, causing increased lag time that benefits their opponents.
Are DDoS attacks illegal?
Yes, malicious DDoS attacks are cybercrimes punishable by law in the U.S., the U.K., and elsewhere. A hacker could receive jail time, fines, or both.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.







Want more?
Follow us for all the latest news, tips, and updates.