How to create a secure password
We’ve all heard the advice that changing your passwords often is the most secure way to go, but this can actually do more harm than good. Instead, create long, unique passwords from the get-go to keep your accounts more secure. Then get Norton 360 Deluxe with its built-in password manager to help keep your passwords safer against hacking.

You might be tempted to make your passwords easier to remember by incorporating cues from your daily life, like birth dates, anniversaries, and pet names. Unfortunately, these tidbits of information make your passwords more predictable and leave them more susceptible to brute force attacks, credential stuffing, and dictionary attacks.
To better protect yourself against cybercrime and account takeovers, create secure passwords by leveraging length, originality, and passphrases.
4 tips for creating secure passwords
When it comes to online security, creating long, strong, and unique passwords is your first line of defense. Here are four key tips to create strong passwords, fortify your accounts, and keep your personal information safer online:
Password mistakes to avoid
Make your passwords more secure by avoiding the following:
- Numerical patterns like “1234”
- Common words like “password” or “guest”
- Repeated characters like “1111”
- Keyboard patterns like “qazwsx” or “asdf”
- Passwords with fewer than 15 characters
- First and last names
- Pet and family member names
- Nicknames
- Important dates
- Cities you’ve lived in
- Schools you’ve attended
- Reversed words like “drowssap”
- Simple character substitutions like “@” in place of “a”
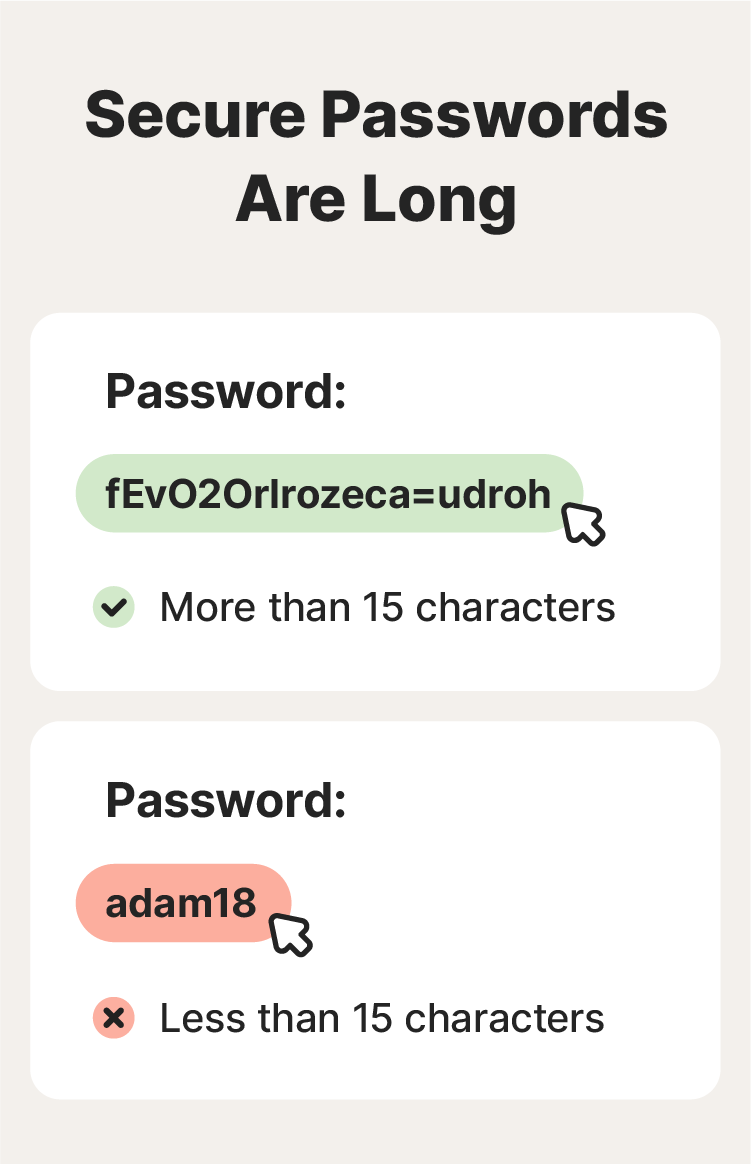
1. Make passwords long
Longer passwords are more secure than short ones, because every additional character increases the number of possible combinations. That means that it’s harder for hackers to guess your password. It also makes the password-cracking process more time-intensive, which could deter brute force attacks. To maximize account security, make your passwords at least 15 characters long.

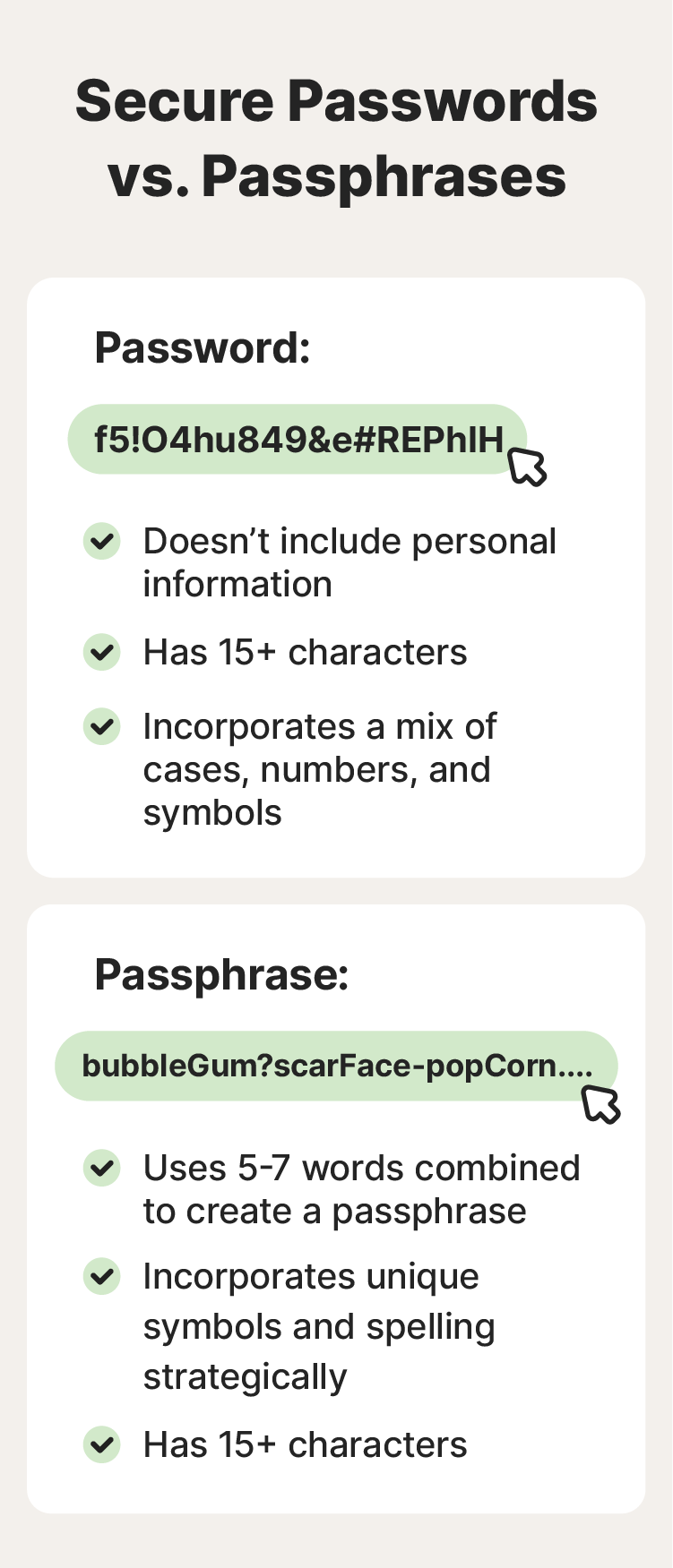
2. Opt for long passphrases
Passphrases are strings of words that can help protect your accounts in the event of password attacks. They should be long, around 5 to 7 words, and unpredictable. As a bonus, passphrases are easier to remember, which can also make them useful for securing your home computer or other devices you use most often.
Just don’t use personal information or choose a passphrase directly linked to something you’ve shared publicly. If you’re a die-hard "Friends" fan and you post about it often, don’t create a passphrase using a well-known phrase from the show, for example, “WeWereOnABreak123!” — it’s too easy to guess, especially if you’re a public fan of the show.

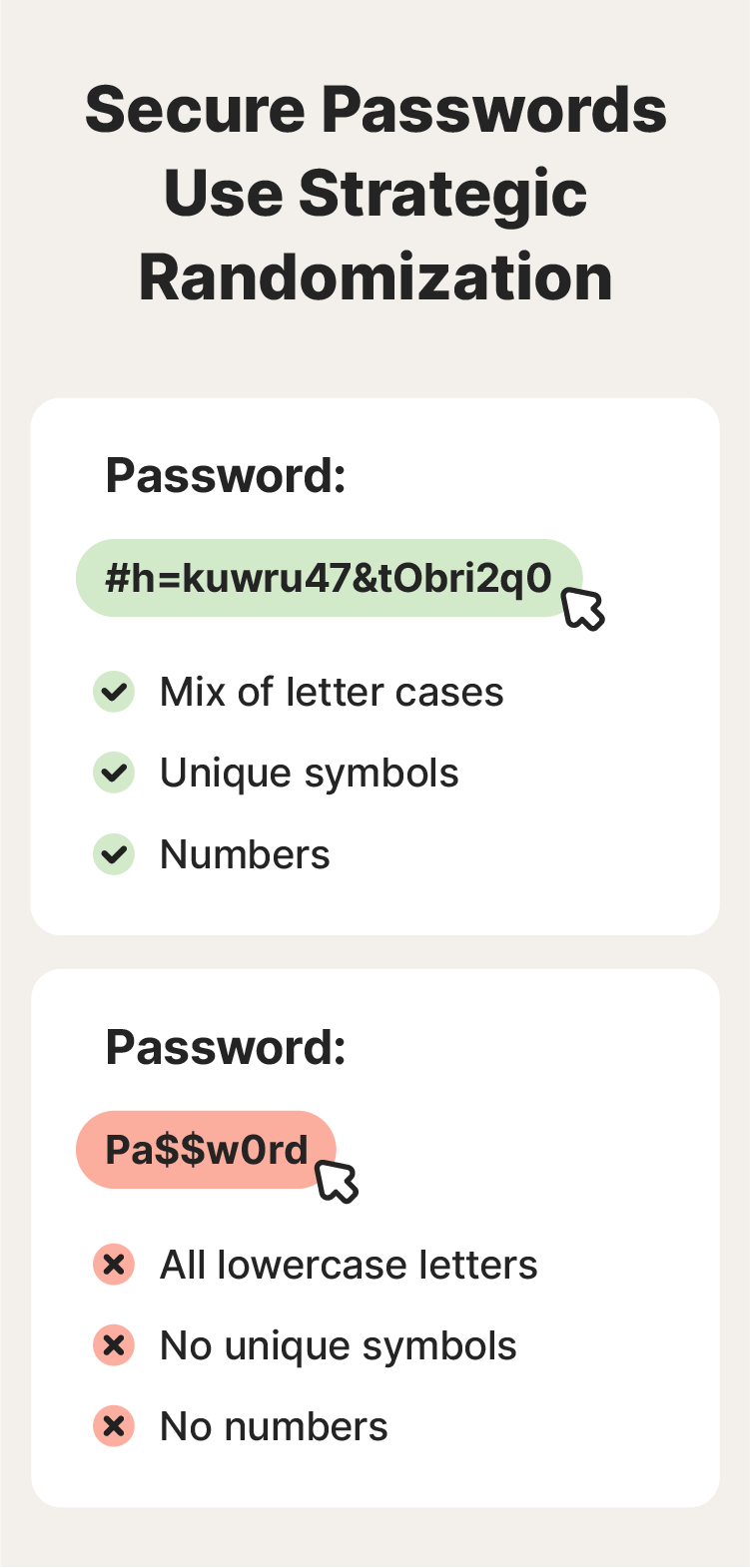
3. Use strategic randomization
Randomized passwords have been the gold standard in password guidance for years in an attempt to thwart hackers’ brute force and dictionary attacks. Since randomized passwords lack predictable patterns, it increases “password entropy,” making them harder for hackers to guess using common numerical patterns like “123.” Using randomization strategically is still very secure, especially to protect highly sensitive accounts like your crypto wallet, but it’s best to leave the randomization to a password manager.
The National Institute of Standards and Technology (NIST) now defines a length of 15+ characters as the priority for creating a secure password — especially for human-chosen ones. Because people often use predictable patterns for passwords that require random characters, such as tacking “123!” on the end, their chosen passwords end up being less secure than if they’d used a long passphrase instead.
In other words, if your chosen password manager creates and stores a randomized password, it’s an excellent, highly secure choice. But if you’re creating your own password, use randomization carefully, or just opt for a passphrase instead.
And even if you develop a completely original password, simply substituting letters with symbols or numbers isn’t enough, as most cybercriminals are well aware of this password trick. For example, if you’re a loud and proud Swiftie, “Wi$hLi$t” works fine as a song title, but it’s a terrible password choice, for all the reasons we’ve mentioned so far.

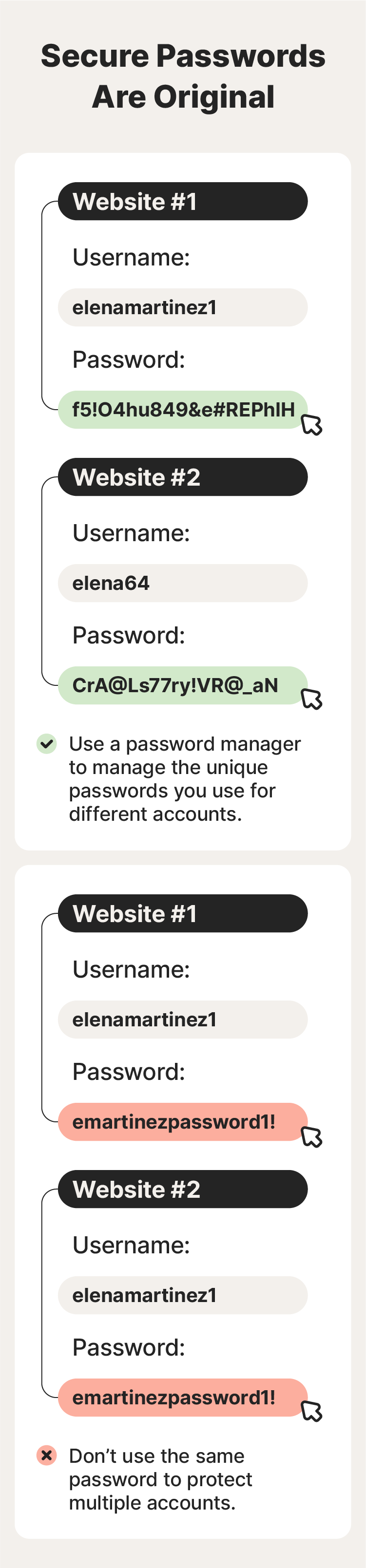
4. Avoid password recycling
Recycling the same password across accounts makes your passwords, accounts, and associated data less secure. If an attacker compromises one password, all your accounts with the same password are at risk. To boost your password security, create a strong and unique password for every account.
The easiest way to avoid password recycling is to use a secure password generator to create them and a password manager to store them.

How to remember strong passwords
While strong passwords are vital, remembering them can be tough, especially when you’re supposed to have a long, strong, and unique iteration for each account. Consider using a mnemonic device, or a password manager like the one built into Norton 360 Deluxe, to stay on top of your passwords.
Password managers
A password manager is a secure digital vault that stores all your passwords. You just need to remember one master password to access it. Then, you can securely and conveniently auto-fill your credentials when you visit a website’s login page.
Mnemonic devices
A mnemonic device is a memory trick that helps you recall information by associating it with something more memorable, such as a phrase or rhyme. You can use these to remember secure and complex passwords — just come up with a memorable phrase or acronym.
For example, you know you shouldn’t use your name in a password. But you can use your name as a mnemonic device for a passphrase. So, instead of making your password “AdamC” (your first name and surname initial), you could use the mnemonic device, “AstronautDrivesArmorMiracleCorduroy,” to remember each word of your passphrase.
While guidance from the NIST no longer imposes composition rules regarding randomized and special characters in passwords, you can still mix up the cases and add numbers and symbols for higher password entropy, as long as it’s easy for you to remember.
Why is password security important?
If passwords aren’t strong and kept secure, cybercriminals could gain access to your accounts. This can lead to scams, financial repercussions, or even identity theft. And then there’s the added stress of recovering hacked accounts or a stolen identity.
- Financial loss: Whether it’s via a drained bank account, blackmail, or transferred money from a payment app, the end goal for password thieves is typically financial.
- Identity theft: If an identity thief has enough information about you, a password could be the final piece of the puzzle they need to achieve their objective. That could be anything from taking out a loan in your name to ordering a new credit card and intercepting it.
- Scams: If a cybercriminal can access your social media accounts or email with your password, they could also scam your contacts or use your own information against you in a social engineering attack.
Scan the dark web for your passwords
Once they steal your passwords, hackers and phishers may sell them on the dark web – potentially exposing your personal data to a nefarious cohort of scammers, cyber thieves, and other unsavory characters. This puts you at a higher risk of identity theft.
For an added layer of protection, install Norton 360 Deluxe. Its advanced Dark Web Monitoring feature scans the murkiest corners of the internet and alerts you if your personal data is found, so you can take steps to protect yourself.
How are passwords stolen?
Cybercriminals steal passwords through various scams and hacking techniques. Here are a few of them:
- Data breaches: If your password is exposed in a data breach, hackers can use it to access the associated account.
- Password-guessing attacks: Dictionary attacks involve hackers trying common words and phrases at scale to guess passwords.
- Malware: Some types of malware can steal your passwords or record your keystrokes as you type.
- Phishing: A phishing attack can be designed to trick you into revealing your password. An attack via email or text could also urge you to click a link that takes you to an unsafe website, where you enter your password and unknowingly expose it.
- Social engineering: Phishing is a common type of social engineering attack but there are other examples, like a scareware attack that could lead to a hacker stealing your password.
How to keep your passwords safe
Password security requires a comprehensive approach. And, despite popular belief and former standards, the NIST no longer recommends regularly updating your passwords unless they’ve been part of a data leak or breach. This is to prevent you from relying on easy-to-remember (and, therefore, easier-to-hack) patterns that make for unsecure passwords.
To keep your passwords safe, follow these tips:
- Create long passwords or passphrases of at least 15 characters
- Use unique passwords for every account
- Use a reputable password manager
- Enable two-factor authentication (2FA)
- Consider passphrases with strategic misspellings or randomized characters
- Subscribe to data breach alerts
- Avoid clicking suspicious links
- Don’t share your passwords with anyone
- Use a reputable security app like Norton 360 Deluxe
Help keep hackers out of your accounts
Strong passwords alone aren’t a foolproof defense against all cyberattacks. However, a strong password coupled with a security tool like Norton 360 Deluxe can go a long way toward safeguarding your accounts and devices.
Norton 360 Deluxe includes a built-in password manager to help you create, store, and secure your passwords. Plus, it offers powerful protection against hackers, malware, scams, and other online threats.
FAQs
What is an example of a good vs. bad password?
An example of a good password is “AstronautDrivesArmorMiracleCorduroy” (but we don’t recommend using this exact one). It’s a good password option because it’s longer than 15 characters and uses between 5 and 7 unpredictable words. Also, it doesn’t include any personal information.
An example of a bad password is adam1234 because it’s short, and includes a name and predictable numerical pattern.
How long should my password be?
A strong password should be at least 15 characters long or between 5 and 7 words for a passphrase.
How do I know if my password is no longer secure?
If your password is short, predictable, has been shared with others, is used for multiple accounts, or has been compromised in a data breach, it is not secure.
What is the best password manager?
One of the best password managers is Norton Password Manager. It offers many benefits, including:
- Spotting weaknesses in your logins
- Helping you create complex passwords
- Protecting login information in a secure online vault
- Using biometrics to verify mobile logins
- Syncing logins across devices
Editorial note: Our articles are designed to provide educational information for you. They may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review the complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc. For more details about how we create, review, and update content, please see our Editorial Policy.









Want more?
Follow us for all the latest news, tips, and updates.