What is a keylogger? A total protection guide
Imagine if someone had access to everything you type? While it can sometimes be done legally, keylogging is a form of data monitoring used to surreptitiously acquire people’s personal information. Learn what a keylogger is, how to spot one, and how strong cybersecurity software can help protect you from keylogging.

Keylogger definition
A keylogger (or keystroke logger) is a type of spyware that monitors and records what you type on your computer or mobile phone. Keylogging software or hardware can be used to monitor activity for legal or illegal purposes.
How keyloggers work
Keyloggers work by recording the interactions a user has with their keyboard, allowing someone to access a log of every email, instant message, search query, password, username, or other keyed sequences that a user types.

Keyloggers record your keystrokes and send the data they capture back to hackers.
Keylogging malware can infect your computer through many of the same mechanisms as other common viruses, but keyloggers can also be intentionally purchased and downloaded.
Keystroke malware can be delivered in a number of ways:
- Phishing emails: By clicking a link or downloading an attachment in a phishing email, text message, instant message, or social media post, you could accidentally download malware designed to track keystrokes.
- Trojan viruses: Named after the giant wooden horse that Greeks used to infiltrate Troy during the Trojan War, hackers trick users into downloading a Trojan virus by disguising it as a legitimate file or application.
- Zero-day exploit: A zero-day exploit happens when hackers discover an existing software security flaw and exploit it. Once developers learn of the vulnerability, it’s too late to protect users. These are particularly dangerous because once the systems are infected, they’re more susceptible to further attacks.
- Infected systems: Keyloggers can take advantage of an already-infected device or system and install other malicious software into that system.
Keystroke loggers are readily available, and there may even be one installed on the device you’re using right now. Keylogging software by itself isn’t necessarily problematic if you signed an agreement to use the device it’s installed on or if it was packaged in your device’s software suite.
What makes these tools problematic are issues of actor intent and victim consent. In short, keyloggers can either be tools or weapons, depending on who’s installing them and how they’re using the acquired information.
It’s important to know the difference, because malicious actors can use keylogging to capture your personal and financial information, PIN codes and account numbers, credit card numbers, usernames, passwords, and other sensitive data — all of which can be used to commit fraud or identity theft.
Types of keyloggers
For the general public, keyloggers are most commonly spread online via phishing scams, Trojan viruses, and fake websites. The hacker’s main goal is usually to obtain victims’ passwords, personal information, usernames, or banking information.
Malicious keylogging mechanisms fall into two broad categories: software and hardware.
Software-based keyloggers
Many software-based keyloggers have rootkit functionality, meaning hackers can easily hide in your system to track your activity, save the data, and forward it to other cybercriminals. Some can even track your clipboard activity, location data, or your microphone and camera.
Keylogging programs can reach you at a few different levels:
- Kernel level: These are complex and difficult to write, so they aren’t especially common. Once installed, keyloggers affecting your device at the core of its operating system are especially difficult to diagnose and eradicate, as they’ve essentially been handed the “keys” to your device.
- Application programming interface (API) level: The most common form of keylogger software intercepts signals sent from your keyboard to the program you’re using. It’s like a recording device between your physical keyboard and a program on your screen, like your word processor.
- Screen level: Known as “screen scrapers,” these types of keyloggers take regular screenshots, recording what appears on your screen.
- Browser level: This is the least complex and least deeply rooted of the four types, but it can still be quite dangerous. This “form-grabbing” ploy records what you type into web forms, which may include everything from your Social Security number to login credentials.
Keylogging software programs are much more common than keylogger hardware because they’re discrete, can be packaged as malware, and are more readily available. However, keylogger hardware is still used for a variety of reasons and should not be ignored.
Hardware-based keyloggers
Hardware-based keystroke loggers have a physical component to their implementation, either in the wiring or hardware of a device or in the settings around it.
A common example of a hardware-based keylogger is the keyboard overlay that a hacker uses in an ATM skimming attack. Every time a bank customer presses the buttons on the criminal’s fake keypad — thinking it’s a legitimate ATM keypad — the keylogger records the keystrokes and sends the information to the cybercriminal.
These keyloggers can’t be detected by antivirus software because they aren’t installed on the computer, and they use their own internal memory to store and encrypt data.
There are several general types of hardware-based keystroke loggers that range in their level of sophistication:
- Keyboard: These keyloggers are installed either in the wiring connecting a keyboard to a computer or directly in the keyboard itself.
- Physical drive: Keylogger Trojans in this category are typically delivered via a USB drive or Mini PCI card.
- Third-party recording: The least sophisticated form of keylogger attack is an external recording device like a camera, which can be strategically placed to monitor public keypads or computer keyboards.
- Acoustic: This rarely used method of keystroke monitoring records the almost imperceptibly distinct sounds made when the different keys of a keyboard are struck.
While keylogging hardware may not be as common as its software-based counterpart, it can still be highly dangerous and can compromise vital data.
What are keyloggers used for?
In some form or another, keyloggers have been in use for decades. These days, keyloggers are one the most common forms of malware, but they are also often packaged with other types of malware as part of a suite of Trojan viruses.
But is a keylogger illegal in and of itself? Not necessarily. Let’s look at legal versus illegal usage examples.
Keylogging examples
The legal use of keyloggers depends on user consent, whether they’re used to steal personal information, who owns the device they’re installed on, and whether the use of the keylogger breaks another applicable law. In general, illegal keylogging is when its use leads to stolen confidential data or when a keylogger is installed on someone else’s device.
Let’s look at some examples of legal vs illegal keylogging:
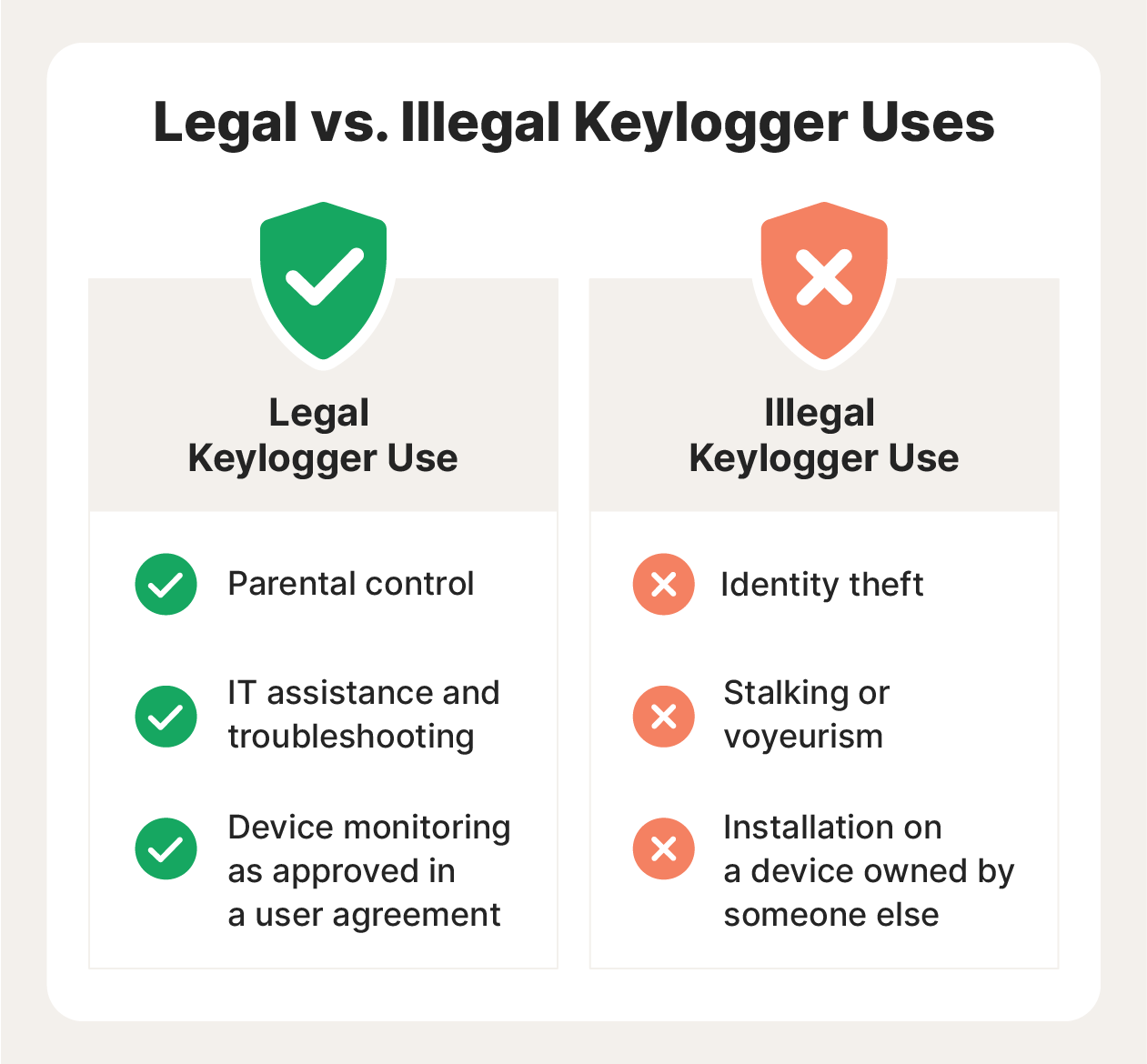
| Legal keylogging uses | Illegal keylogging uses |
| User experience data monitoring | Account information theft |
| Parental control to monitor and protect children’s online activity | Collecting sensitive information |
| Recording usage on a personal device owned by the keylogger user | Monitoring when consent was explicitly denied via a legally binding contract |
| Network, software, or hardware troubleshooting | Capturing credit card information and PIN details |
| Company data exchange and search query monitoring | Installing software or hardware on someone else’s device |
| Devise-use monitoring by a company or public entity, such as a library | Keystroke monitoring of a public device |
| Any legal usage consented to via a user agreement or contract | Unlawful stalking or voyeurism |
The threats of keyloggers
No matter how secure you believe your devices are, a keylogger attack represents a major threat, because hackers can weaponize some of your common virtual activities without your knowledge.
With a keylogger, cybercriminals may be able to record everything you type. A lot of information can be gathered through the emails and texts you send, the login credentials you enter, and how you search and browse the web.
And while cybercriminals may use keylogging malware for more overtly dangerous data like bank account numbers, PINs, or Social Security numbers, they can also steal sensitive content like browsing data, private conversations, and even video or audio recordings.
After cybercriminals access this information, you could be susceptible to the following threats:
- Identity theft
- Data ransom
- Virtual or physical stalking
- Voyeurism and eavesdropping
- Credit card and other banking or financial fraud
- The exposure of sensitive personal information
This is in no way an exhaustive list of the ways in which keylogging can be used against you. It’s vital to protect your methods of accessing, transferring, and recording your data so you can mitigate these and other keystroke-monitoring threats.
How to protect yourself from keyloggers
To help protect yourself from keylogger malware attacks, follow online safety best practices and maintain a healthy sense of skepticism when engaging in online activities.
Malicious keylogger protection is similar to most forms of virus protection, but no solution is perfect, not least because new malware is written all the time.
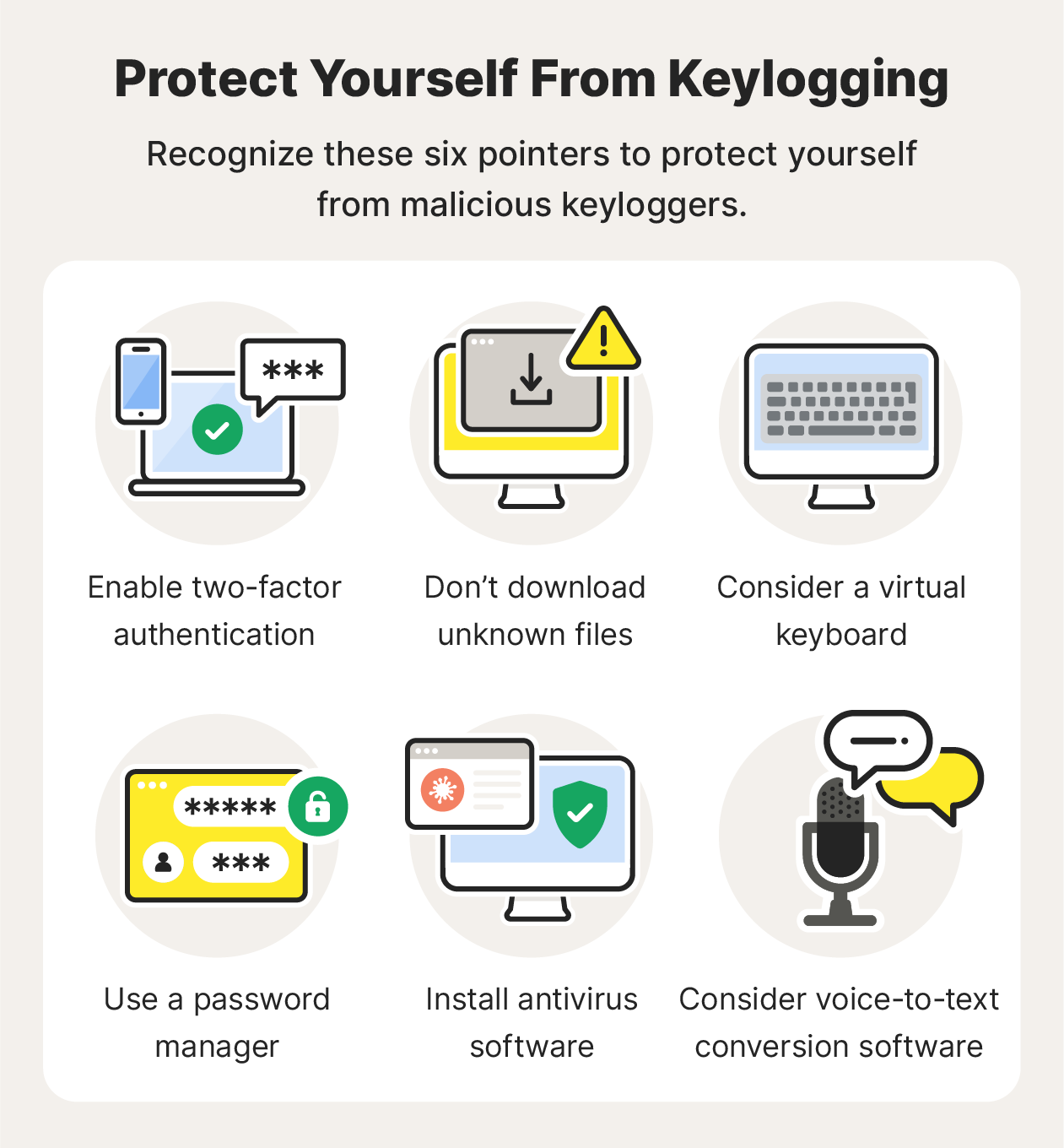
Here’s how you can help prevent keylogging attacks and reduce the risk of a malware infection:
- Enable two-factor authentication: Enabling two-factor authentication (2FA) is one of the most effective forms of virus, malware, and keylogger prevention. 2FA adds an extra log-in step such as a fingerprint or temporary PIN sent to your phone, which helps to authenticate your identity and make sure unauthorized people can't access your account.
- Don’t download unknown files: Another important way to protect yourself from different types of malware is to avoid downloading unknown files or clicking on suspicious links. Phishing attacks are widely used scams that can lead to malware or keylogger infections.
- Consider a virtual keyboard: This displays an interactive keyboard on your screen, so you don’t have to physically type on an analog one. Virtual keyboards circumvent keylogging hardware and any keylogging software specifically designed to record interactions with your physical keyboard. But some software can still monitor your on-screen interactions, so it’s not a complete solution.
- Use a password manager: A password manager isn’t just a convenient way to store passwords. It’s also an effective tool against keylogging, because you don’t display your passwords or physically type them into your keyboard or keypad, meaning that keystroke monitors can’t capture them.
- Consider voice-to-text conversion software: Like a virtual keyboard, voice-to-text conversion software can circumvent forms of keylogging that specifically target your physical keyboard.
- Use antivirus software: Look for antivirus protection that includes anti-spyware and anti-keylogger protection. As with all forms of viruses, new, more sophisticated keystroke malware is being written all the time, so keep your software updated to stay more secure.
Norton 360 Deluxe provides strong protection to help prevent keyloggers and other forms of malware from compromising your device and spying on your activity. Plus, it includes a range of other security and privacy features, like a built-in VPN, to strengthen your online privacy.
How to detect and remove keyloggers
Keylogging spyware thrives on stealth, but can a keylogger be detected? While hardware may be relatively easy to find — like a USB drive or a peripheral connected to your keyboard — software can often go undetected until it’s too late.
Keylogging malware can show many common virus warning signs, including slower computer performance when browsing or starting up programs, abnormal delays in activity, pop-ups, new icons on your desktop or system tray, or excessive hard drive or network activity.
If you detect any of these symptoms and think your device may be infected, here’s how to scan for keyloggers and remove keylogging malware.
- Check your software inventory.
Successful keystroke logger detection starts with taking stock of the programs and processes running on your computer. While many of these apps may have unfamiliar or even suspicious-looking names, some may blend in with the names of other software and be harder to spot. - Check your browser extensions.
Some keylogging malware is designed specifically to monitor your web usage and may show up as a browser extension. Check your browser menu and the list of active extensions. If there are any you don’t recognize or didn’t download, deactivate and remove them. - Remove keyloggers.
Keyloggers can be removed in much the same way as you would remove other forms of malware. Always exercise caution when handling computer programs — even if one seems suspicious, it could be a necessary tool, and disabling it could cause problems. If you’re certain a program is a keylogger, disable it, uninstall it, and delete it from your device. - What to do if you don’t find a keylogger.
If you fail to identify any malicious keyloggers, you could reinstall your device’s operating system or perform a factory reset, which will effectively wipe all the data and programs from your device that were installed over the factory default settings.
In a perfect world, you would never need to know what keylogging is. But today there are many cybercriminals out there trying to trick as many people as possible into downloading malware like keylogging programs. That’s why it’s so important to practice safe internet use and protect your sensitive information.
Using reliable anti-malware software like Norton 360 Deluxe is an essential part of your cybersecurity arsenal. Not only will it help protect you from keyloggers, but it will also help keep ransomware, viruses, and other malware off your device. Plus, it features a built-in VPN to encrypt your internet connection and help keep your online activity private.
What is a keylogger FAQs
Below are answers to some of the most commonly asked questions regarding keyloggers.
Is a keylogger illegal?
While keylogging tools are not necessarily illegal, they are often used illegally by cybercriminals, identity thieves, or other malicious actors to surreptitiously steal information or track activity without someone’s consent.
What is the history of keyloggers?
Early cases of keylogging in the 1970s involved government surveillance of electronic typing machines. Today, keystroke monitoring software is widely available for commercial and personal use.
Do mobile devices get keyloggers?
Mobile devices can be monitored using keylogging applications that monitor mobile phone keypads. Some of these spyware programs may also be able to monitor screen interactions, downloads, location data, and even conversations.
Editorial note: Our articles are designed to provide educational information for you. They may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review the complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc. For more details about how we create, review, and update content, please see our Editorial Policy.






Want more?
Follow us for all the latest news, tips, and updates.