Mobile security: What it is and why you need it
You may not know it, but unprotected mobile devices are a prime target for hackers, identity thieves, and other cybercriminals. Mobile security combines practices and software that protect your devices from hackers, malware, and identity theft. Find out why mobile phone security is so important and how a comprehensive mobile security app can help you secure your devices and personal information.

Our tablets, laptops, and smartphones aren’t just for making calls, checking email, and sending text messages—they’re increasingly becoming the primary way we shop online, bank, and even work. It’s easy to forget how much we entrust to these devices, because they play such a large role in our daily lives.
But it’s our reliance on these devices that makes protecting our personal information more important than ever. With the right mobile device security, we can keep enjoying the benefits that come with having the internet at our fingertips.
What is mobile security?
Mobile security is a system of security software and habits that keeps your data out of the hands of hackers, scammers, and identity thieves. While it’s tempting to think that only politicians, financial institutions, and big tech companies need enhanced security, everyone needs protection.
| Elements of Mobile Security | |
| Security Software | Security Practices |
|
|
Why mobile security is crucial
While device manufacturers help you protect your Android and Apple devices and operating systems, it often isn’t enough to fully safeguard your data from attacks by hackers.
Cybercriminals don’t discriminate when they create malware to infect the latest computers, phones, and tablets. If they can design a virus that will make its way into the servers of large banks to steal account numbers and passwords, those scammers will also find a way to deploy it against normal people (or they’ll sell it to someone who will).
Mobile security attacks can:
- Expose your financial information.
- Increase the likelihood of identity theft.
- Corrupt your files and personal data.
Real security means taking extra steps to improve your digital safety habits and using software that recognizes and stops threats before your devices are compromised.
5 examples of mobile security and how they work
Because the threats posed by malware and hacking are so varied, the systems needed to prevent and stop them are varied, too. When mobile security systems work together, they create a much stronger shield against bad actors than any one system could on its own.
Some examples of mobile security include:
- Encryption to keep your online traffic and data secret. Encrypted information can only be read by those with the decryption key.
- Secure boot processes for safer compliance between hardware and firmware. These security standards ensure that hardware can use operating systems and programs. This prevents dangerous hardware, like a flash drive loaded with malware, from being able to access and run amok within a system.
- Application sandboxing to observe and stop the spread of malicious software. Application sandboxing creates a limited environment for code to run. These environments reduce access to resources to observe new programs, recognized threats, and suspicious code. By isolating and observing malware, these systems can learn how it functions and how to protect against it.
- Mobile malware and antivirus software stop known threats and watch over your devices. Using signature detection to stop known threats along with a form of application sandboxing to contain possible threats, mobile antivirus software helps keep devices free from infection.
- Network security protocols, like HTTPS, let your devices know a connection is safe. These protocols, including SSL certificates, create an encrypted channel for traffic to move safely between trusted devices.
When combined, these systems can scan the hard drive in your computer and the attachments in emails, links in text messages and emails, and the apps you’ve downloaded to identify potential threats.
After identifying a threat, they can warn you about a link connected to a phishing site, stop you from downloading an unsafe application from a third-party app store, and even isolate viruses and other forms of malware.
The main threats to mobile security
Malware, viruses, outdated apps and operating systems, phishing, data theft, cryptojacking, and unsecured Wi-Fi are the main threats to mobile security.
These threats present themselves in many different formats, and the people behind them always try to improve their effectiveness. Knowing these dangers, how they impact your mobile data security, and what damage they can do can help you react when these problems arise.
Malware and viruses
Malware means “malicious software” and is a blanket term that covers many different types of malicious programs, including:
- Viruses: requires a host to deploy their attack.
- Trojans: masquerades as a legitimate program.
- Worms: replicates itself on a system, fills drives, and spreads.
- Rootkits: provides hackers with remote access to a device.
- Ransomware: encrypts your data and asks for ransom.
- Spyware: observes your actions on a computer.
- Botnets: gains access by finding vulnerabilities.
- Adware: installs programs that frequently show malicious pop-ups.
While different types of malware work differently, they’re all designed to gain secret access to a device and cause harm.
If your mobile security system isn’t set up to detect and remove malware from your device, somebody could corrupt or steal your data. Cybercriminals can take complete control of your phone, laptop, or tablet, and the performance of your device may degrade or grind to a halt.
Outdated apps and operating systems
Software updates and patches eliminate vulnerabilities that hackers could exploit, strengthen existing security measures, and introduce features that make your devices more efficient and powerful.
But if you don’t update your apps and operating system soon after the patches are released, you’re exposing whatever is on your phone to hackers who’ve created malware to break through any weak points in your mobile device.
Phishing attacks
Phishing is when a scammer pretends to be someone else to extract sensitive information about you. They may send an email pretending to work at a local branch of your bank to get you to reveal your account information and password. You may receive a text message from an unknown number trying to steal your login credentials by using a link to a website designed to look like a real site you actually visit.
Phishing goes beyond your devices, though. If a scammer can extract enough information from someone, they could attempt to steal your identity.
Data theft
Data theft occurs when somebody steals your data from your device or during a data breach of a company or organization that holds identifying information. Breaches of medical providers and retailers can lead to the exposure of your name, address, passwords, and even your medical records on the dark web.
Cryptojacking
Cryptojacking uses malware to infect internet-connected devices with a program to mine cryptocurrency using the device’s resources. Even if you don’t trade in or mine cryptocurrency, a hacker could use the power of your computer, smartphone, or tablet to line their pockets while your device’s performance suffers.
Unsecured Wi-Fi
Being able to get onto the internet when you’re running errands or enjoying a meal at a restaurant is one of the many benefits of public Wi-Fi. But unsecured private and public Wi-Fi can leave you exposed.
Because many routers don’t encrypt traffic by default, hackers can connect to devices on these networks and eavesdrop on your online activity. These man-in-the-middle attacks can show a hacker everything you’ve been doing while connected to these routers, including logging into bank accounts, shop accounts, and more.
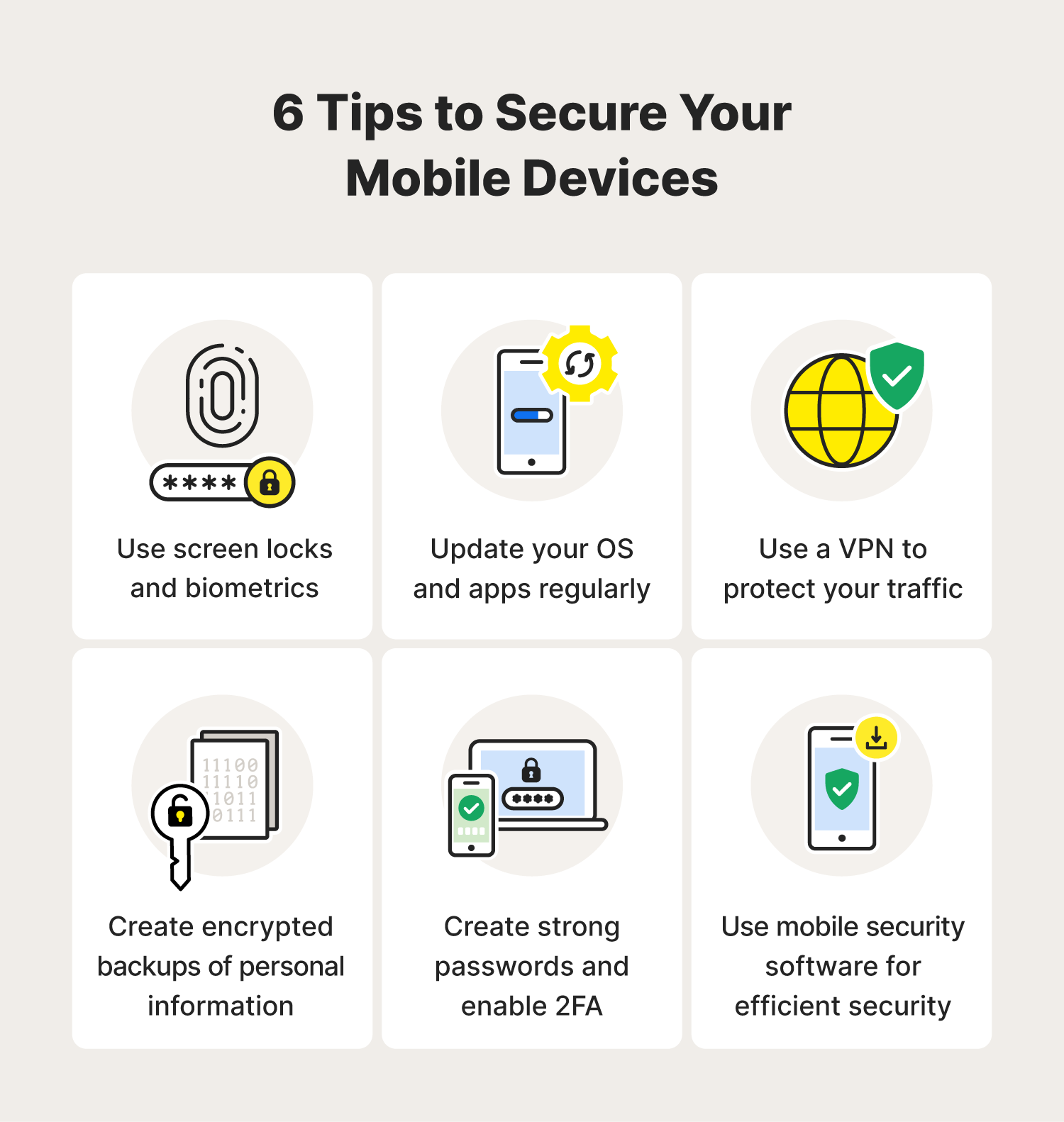
How to secure mobile devices
Just as there are many different kinds of threats, there are many ways to reduce the likelihood of your device being impacted by one of them. With a few small changes, you can better secure your digital life and help keep different types of hackers and malware at bay.
Enable screen locks and biometrics for better in-person security
Built-in security features should be your first line of defense against physical device tampering and theft. Choose as difficult a passcode as you can easily remember, and don’t reuse any of your codes. Biometrics, like FaceID or fingerprint scanners, create an extra layer of security that is more difficult to hack than a password.
Keep your devices and apps up to date to limit vulnerabilities
An updated device is more secure than one running an older operating system or application. Turn on automatic updates to minimize the time your phone is vulnerable to known threats.
Use secure networks and VPNs for safer browsing, shopping, and downloading
A VPN creates an encrypted path for you to use the internet by anonymizing your device and masking your IP address. Always protect your browsing when on public Wi-Fi by using a VPN.
Back up and encrypt data to protect your personal information
Backing up an encrypted copy of your data protects you in the event of malware disabling your mobile device. Encrypted cloud backups mean you can access your data anywhere and be nearly as safe as with encrypted physical backups.
Employ strong, unique passwords and 2FA to keep your accounts safer
Using a password manager will make securely storing and accessing passwords simple. Follow good password security practices by choosing unique passwords that you don’t reuse. Turn on two-factor authentication to put another roadblock between hackers and your personal information.
Use mobile security software for faster, more efficient mobile security
Mobile security software like Norton Mobile Security for Android and iOS devices combines many of these security features into an easy-to-use package. It scans your messages for phishing attempts, warns you when suspicious networks are nearby, and protects your devices from malware.
The biggest challenges of mobile security
Even with the most advanced security software and good digital security habits, there are still some significant challenges to tablet, laptop, and cell phone security. All of these challenges are manageable, but they can complicate or force changes to your security best practices.
Rapid technological advancements create new vulnerabilities and new tools for hackers
Changes in technology mean criminals and hackers have more tools than ever—but so do the engineers patching apps, operating systems, and security software. This is a struggle that likely will never end, but it’s a good example of why having extra layers of protection can keep your devices safer.
- Potential solution: Use cutting-edge antimalware tools that are created to counter hackers and scammers.
User behavior and awareness is never perfect and can lead to mistakes
Nobody’s perfect, and everyone will eventually make a mistake regarding their mobile security practice. Unfortunately, these mistakes can have real consequences for the safety of your data and devices.
- Potential solution: Use strong security software and take advantage of password managers to help overcome some human oversights.
Balancing security and the usability of mobile security measures takes time and effort
One of the best ways to overcome human error is to make protective measures as easy as possible while offering the most advanced and powerful features.
- Potential solution: Use a VPN or private browser to balance usability with security.
Operating system and app updates can render mobile security software less effective
Introducing new features, protocols, and code via patches and updates can limit the efficacy of security software (at least until it has been updated to work alongside the new version of the operating system).
- Potential solution: Use security software that updates frequently to remain effective.
Start protecting your mobile devices today
Norton 360 for Mobile helps safeguard your Apple or Android devices against the threats posed by malware, hackers, and dangerous websites. Plus, it features a built-in VPN to keep your online activity secure and a dark web monitoring component to help alert you if your personal information is found on the dark web.
FAQs about mobile security
Have more questions about mobile security? We have answers.
What is the best security you can put on a mobile device?
The best mobile security depends on a variety of factors, including:
- Device type
- How frequently you use your device
- What you use your device for
Regardless of these factors, it’s a good idea to take advantage of the security features in your devices. That means screen lock passcodes, biometrics, and remote wiping if you lose your device. Installing cybersecurity software will give you an extra level of protection from threats.
How can I make my phone more secure?
To make your phone more secure, you should use security software, use a VPN when you browse the internet with public Wi-Fi, keep your operating system and applications updated, and avoid clicking on links and downloading files from people you don’t know.
What's the most secure way to lock your smartphone?
The most secure way to lock your smartphone or tablet is to set a passcode and use any biometric security features (like a fingerprint scan or facial recognition) available on your device. It’s also vital that you choose a unique passcode and that you don’t share your passcode with anyone.
Do I really need a password lock on my phone?
If you care about the security of your phone and the personal information on it, yes. Not only will it stop people around you from accessing your device without your permission, but it may also prevent your information from falling into the hands of a thief if your phone is stolen.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.







Want more?
Follow us for all the latest news, tips, and updates.