Phishing protection: 11 tips to protect yourself from phishing
A phishing attack is a type of cybercrime that tries to trick you into giving away sensitive personal information or unknowingly installing malware on your device. Learn more about the best phishing protection, from recognizing the signs of a phishing message to using Norton 360 Deluxe, which features a built-in scam-detection engine to help detect phishing attacks.

Phishing attacks are usually launched via email, private messages on social media, text, or any other type of digital communication. It may be a message from a stranger, or from a sender disguised as a business or institution you trust. According to the FBI’s IC3 Crime Report, there were nearly 300,000 reports of phishing in 2023, making it the most commonly reported scam type that year.
What is the best protection against phishing?
The best protection against phishing is a multi-layered approach, including knowing how to spot phishing, not clicking unknown links, using robust security software, and securing your accounts with two-factor authentication (2FA).
Take a look at our 11 phishing protection tips to learn more.
1. Learn the signs of phishing
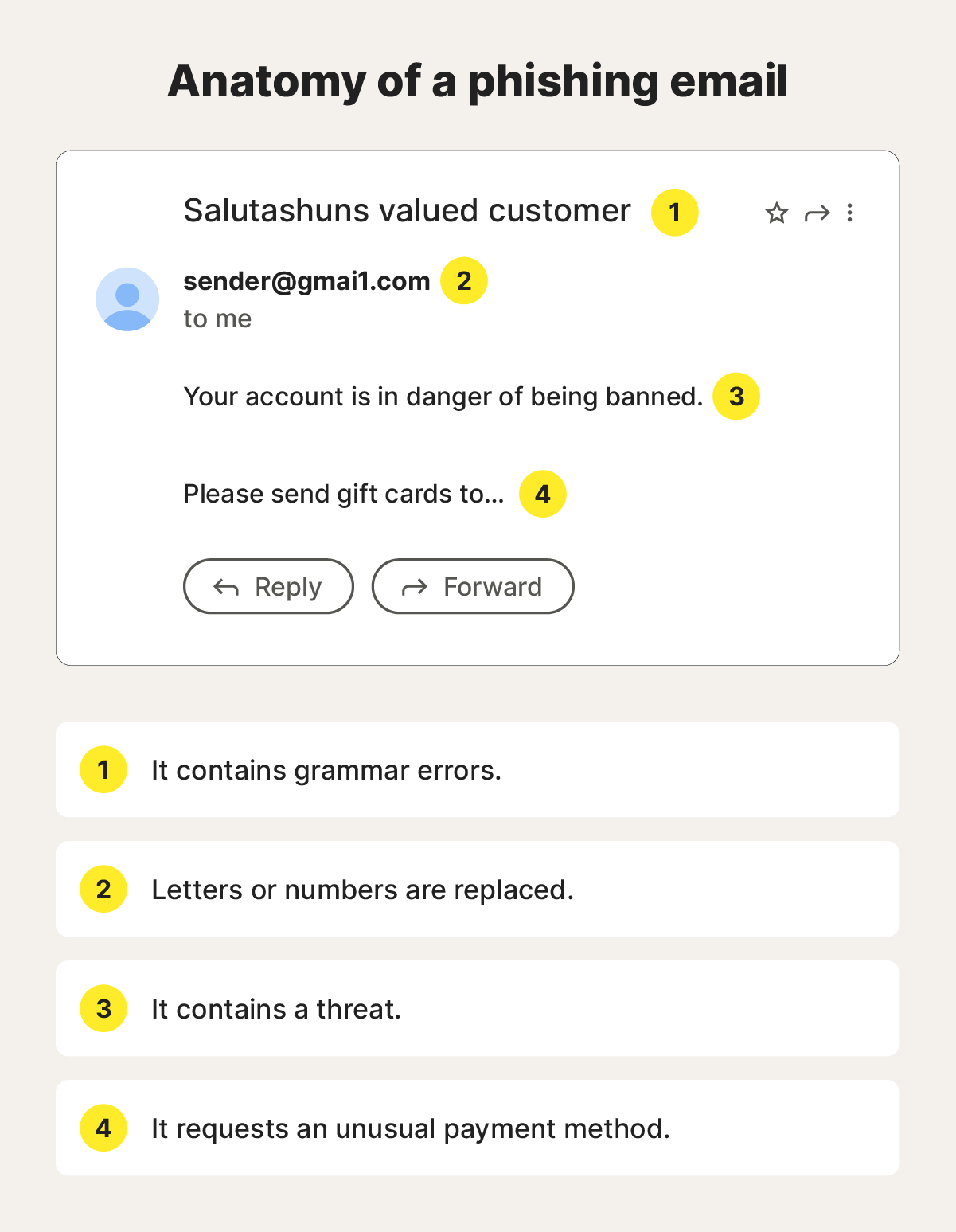
Common phishing email red flags to look for include generic greetings, unusual links to URLs, unknown sender addresses, and unexpected errors throughout the communication.
Here are additional red flags to look for in phishing emails:
- Unusual message content: Poor grammar, unexpected or seemingly random prizes, and requests for personal information.
- Suspicious links: Overcomplicated URLs, unusual attachments, and links that almost match legitimate URLs (for example, small changes like “m” to “rn” that may go unnoticed if you’re skim reading).
- False urgency: Threats of account suspension or arbitrary time constraints.
- Odd payment requests: Requests for payments via non-standard methods, like gift cards or P2P payment apps.
- Bad design: Poorly formatted emails, broken links, multiple fonts or colors, colors or logos that don’t match the company’s official branding.

If you’re ever suspicious about a message in your inbox, don’t click any links in the message or send a response. By responding, you’re confirming that you have an active email address, which can prompt phishers to continue targeting you in future attacks.
To help detect a phishing message, use Norton 360 Deluxe with its inbuilt, AI-powered scam detection capabilities. Just take a screenshot of the communication and pop it in the tool. Within seconds, you’ll get a notification warning you if you’re looking at a potential phishing attack.
2. Never click unknown links or attachments
Avoid clicking links or attachments in suspicious emails or texts. Ask yourself why you’re receiving the link, and consider it suspicious if you weren’t expecting the communication.
Before clicking a link in any email — even ones you trust — hover your mouse over it to preview the true URL and check for misspellings in domain names.
Any attachment from unknown individuals could be suspicious, but you should especially avoid clicking attachments labeled with “.exe,” “.zip,” or “.scr” file types from unknown sources. These file extensions can deliver malicious files to your device.
If you’ve accidentally clicked on a phishing link or downloaded something suspicious, disconnect from the internet and run a full system scan using your antivirus software.
3. Filter unwanted emails
Many email providers filter malicious emails into spam or junk folders before they ever reach your inbox, then delete them automatically after a specific period. However, they might not catch all of them — that’s when you report emails as spam to filter them out going forward.
How to filter phishing emails in Gmail
- Open your Gmail via a web browser, and click the checkbox next to the spam email you want to filter.
- Click the three dots icon at the top of your inbox and choose Filter messages like these.
- Determine which sender(s), subject, words, and sizes to filter, based on the emails you want to remove from your inbox, then click Create filter.
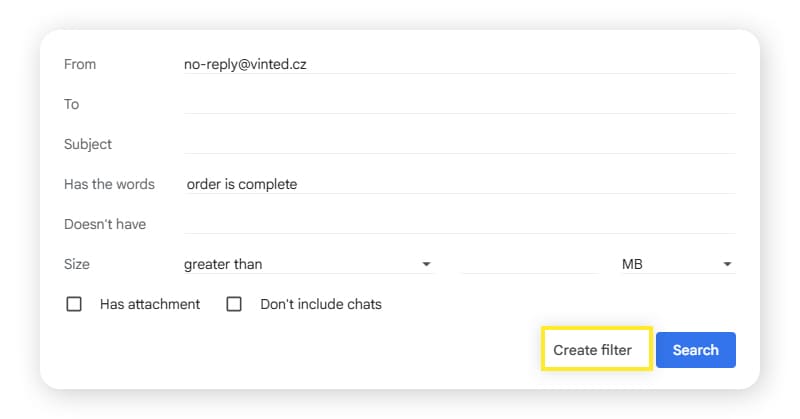

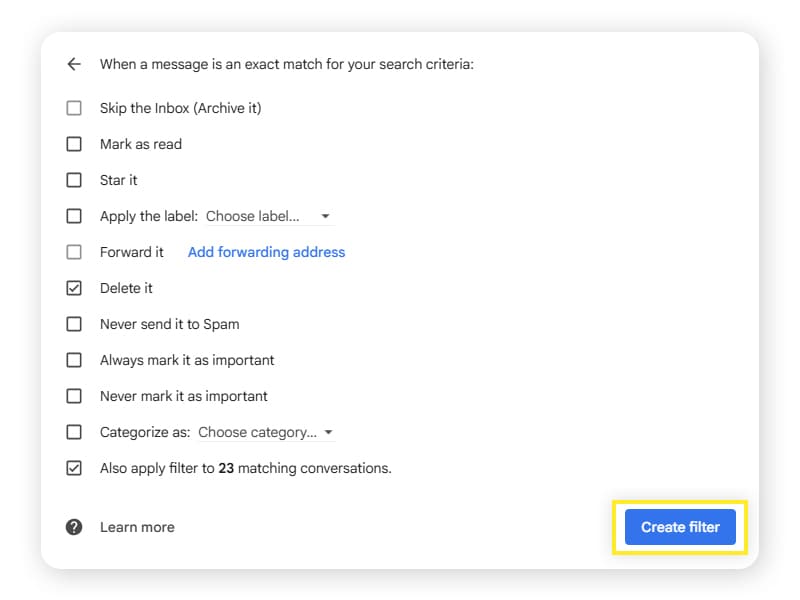
4. Choose what you want to do with the email. The safest option for spam emails is Delete it. Then, click Create filter to confirm.

On mobile, open Gmail and select the email you want to report as spam. Tap the three dots icon in the top-right corner of the screen and select Report spam.
How to filter phishing emails in Outlook
- Open the email.
- Select the three dots icon to the right of the sender.
- From the drop-down menu, select Advanced actions > Create rule.
- Click More options and fill in the conditions to automatically filter emails from that sender to the location of your choice.
4. Report suspicious messages to your email provider
After noticing a suspicious message in your inbox, it’s best to report it immediately. This can help providers stay on top of potential phishing threats and keep you and your inbox safer.
Here’s how to report phishing emails in Gmail via your computer:
- Go to the phishing email.
- Click the three dots icon next to the Reply button.
- Select Report phishing.
If the scammer sends the phishing message to your work email, click the Report phishing icon, and inform your company’s IT department. You can also forward the message to the Anti-Phishing Working Group or report it to the Federal Trade Commission. By doing so, you could help limit phishing attacks on other people.
5. Avoid sharing personal information
When using email, avoid sending any sensitive information. Cybercriminals can use your data for fraudulent purposes, like identity theft. These emails will also be stored in your Sent history or Archive, putting you at risk if a hacker takes over your email account.
Here are some examples of personal information that you should never share over email:
- Social Security numbers
- Banking information
- Credit card numbers
- Account passwords
- Birth dates
- ID numbers
- Health insurance information
6. Use strong passwords and two-factor authentication
Robust account security involves strong password security and activating two-factor authentication (2FA).
2FA requires you to use something you have (like your phone) or a biometric trait (like your fingerprint) to sign into an account. This means the hacker needs physical access to your device (or to you) to gain access. Together, a strong password and a 2FA verification method can successfully protect an account from attacks 99.9% of the time, according to Microsoft.
Follow these best practices when creating passwords:
- Make your passwords long (at least 15 characters).
- Avoid personal information (birthdays, names, addresses, etc.).
- Make each account’s password unique.
If you need help creating strong passwords, Norton 360 Deluxe includes a built-in password manager that helps you create unique, strong passwords for each account — and save them securely all in one place.
7. Keep your software up to date
Operating system updates often include essential security patches to keep your device safer. These can help protect you from security threats that may target your device through phishing attacks, like malware slipping through unpatched vulnerabilities.
Follow these best practices to make system updates easier:
- Enable automatic updates in your settings.
- Schedule updates during times you’re not using your device, for minimal disruption.
- Do not postpone security updates.
- Back up your files before installing major updates.
Your update checklist should start with your operating system and extend to web browsers, security software, and all installed applications. To make this easier, rely on your device’s built-in updating tools and automatic update settings.
8. Monitor your financial accounts
Many phishing attacks aim to gain control of your financial accounts or collect your sensitive financial information, so it’s key to monitor your statements. If you notice unfamiliar charges or suspicious activity, it could be a sign that a phishing attack compromised your accounts.
Here are some additional signs you’re the target of a financial account takeover:
- Debt collectors: You’re getting calls from debt collectors about money you’ve never owed. Cybercriminals use social engineering to launch phishing attacks and fool users into thinking they’re legitimate.
- Missing bills: Bills you expect via email or mail suddenly stop showing up. Cybercriminals can change your account addresses to gather information about you.
- Credit notifications: You’re getting unusual notifications about credit you didn’t apply for. Cybercriminals who acquire your information in a data leak can use it to open credit cards and loans.
- Inaccurate credit reports: Your credit report shows debts you never applied for. Credit reporting apps can notify you of major financial changes, notifying you of potential identity theft moments.
If you believe you’re the victim of a financial account takeover, start by freezing your credit report and contacting your financial institutions to lock your accounts. You should then report the fraud to the Federal Trade Commission and local authorities. Getting over being scammed can take time, so it’s important not to blame yourself.
9. Use anti-phishing software
Using anti-phishing software is a great way to protect yourself from many types of phishing and other scams. If you accidentally click a suspicious link, your phishing protection software can step in before viruses or other types of malware can infect your device and leave you and your personal information unprotected.
What the experts say
"Attackers are moving away from broad, indiscriminate campaigns to highly personalized, AI-enhanced deception." - Gen 2025 Threat Report
Siggi Stefnisson, Cyber Safety Chief Technology Officer
Phishing scams can trick you into giving away personal information or installing malware, and that’s where a robust cybersecurity suite like Norton 360 Deluxe can help. With features like AI-powered scam detection, Norton helps you determine if the messages you receive are phishing scams.
10. Regularly back up your data
Routinely backing up your data is a good way to increase your peace of mind and help protect against the damage of phishing attacks. That way, if something goes wrong with your device, you’ll still have access to all your important files and data.
Here are some ways to back up your data:
- Automatic cloud backup: Cloud backup systems automatically store the files on your computers on the internet. This is an easy way to prevent ransomware attacks from holding your files hostage.
- USB drive: A USB drive is a convenient way to back up and carry around important data. By leaving your files off the internet, you also help prevent cybercriminals from accessing them.
- External hard drive: An external hard drive stored securely is an alternative physical storage option. They’re harder to lose than smaller USB drives, and typically hold much more data.
Regular data backups help keep you safe when you’re the target of ransomware attacks. These attacks encrypt your files and data, demanding payment if you want them back. By backing up your data, you already have a copy in your possession, preventing total losses.
11. Avoid jailbroken devices
Jailbreaking (also called “rooting” on Android devices) is the act of removing software restrictions on your device. This practice is done on smartphones to unlock additional features, further customize settings, or install third-party applications.
While the idea of removing certain restrictions might seem enticing, it leaves your device more vulnerable to mobile security threats that may come along in phishing attacks.
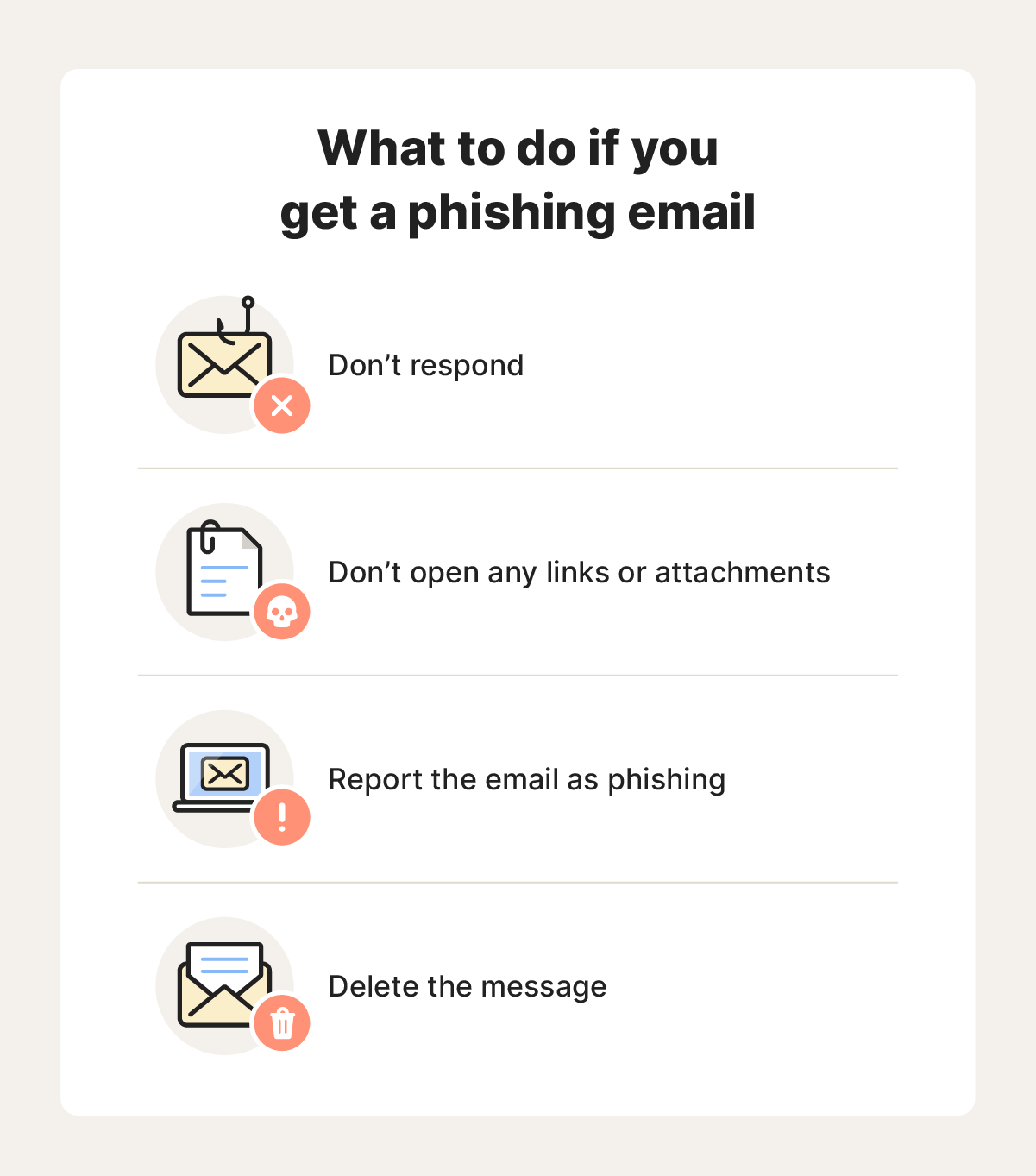
What to do if you get a phishing email
If you receive a phishing email, it’s best to delete the message and be done with it. If you open the email, never click any links or attachments, and never respond. You can also report the email as a phishing email, depending on your email client.

What is the most common type of phishing email?
The most common type of phishing email is business email compromises, according to 2022 IC3 data. Cybercriminals are eager to make a quick buck, and an easy way to do that is to send a fake bill that looks legitimate.
How is email used to execute a phishing attack?
A criminal can use an email to execute a phishing attack by tricking their victim into downloading a malicious file or providing sensitive personal information.
What to do if you respond to a phishing email
If you’ve accidentally responded to a phishing email or fallen for an email scam and shared personal information, change your passwords immediately for any accounts that may be in danger of getting hacked.
Then, follow these tips for further protection:
- Add two-factor authentication to your online accounts.
- Place a fraud alert or credit freeze on your credit file if you shared personal financial information.
- Contact your bank or credit card issuer if you’ve paid a scammer or provided card or account details.
- Report the message to your email provider and authorities.
Following the attack, monitor all your online accounts and banking statements closely. This can help you determine whether the scammer successfully accessed any of your account.
In addition to the phishing email protection steps listed above, practicing good email security is an excellent way to ensure that you and your device stay safe. By prioritizing your cybersecurity, you can send, surf, and scroll while knowing you’ve taken the proper steps to stay more secure online.
How do you know if you’ve been phished?
You know you’ve been phished when you accidentally download a fake file or provide information to a false email. Signs of successful phishing attempts include attempted account logins and multiple 2FA requests you didn’t make.
Stay safer against phishing attempts
Scammers have become increasingly sophisticated in their phishing attempts, making them harder to spot. Use Norton’s built-in scam detection feature — Genie — to help identify whether a message might be phishing. Just upload a screenshot of the suspicious message and Genie can help you detect if it’s a scam or not. Get powerful phishing protection today.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.
- What is the best protection against phishing?
- 1. Learn the signs of phishing
- 2. Never click unknown links or attachments
- 3. Filter unwanted emails
- 4. Report suspicious messages to your email provider
- 5. Avoid sharing personal information
- 6. Use strong passwords and two-factor authentication
- 7. Keep your software up to date
- 8. Monitor your financial accounts
- 9. Use anti-phishing software
- 10. Regularly back up your data
- 11. Avoid jailbroken devices
- What to do if you get a phishing email
- What to do if you respond to a phishing email
- Stay safer against phishing attempts









Want more?
Follow us for all the latest news, tips, and updates.