Bluetooth security risks to know (and how to avoid them)
Plenty of devices use Bluetooth. But is it safe? To find out, read this Bluetooth security guide to learn more about its risks and how you can safely use it.

Let's be honest — wires can be frustrating.
Whether your headphones are getting in your way on your morning run or you can't find that USB cable, sometimes it's just easier to go wireless.
Luckily, Bluetooth makes that possible.
From streaming music to file sharing, Bluetooth technology allows you to quickly make connections between devices.
But is Bluetooth safe, and are there any Bluetooth security risks to be aware of? To learn more about Bluetooth, its security risks, and how to safely use it, read through our Bluetooth security guide.
But first, what is Bluetooth and how does it work?
Bluetooth is a wireless technology that exchanges data between devices within a short distance. This technology is an open standard, meaning that anybody can use it without a license. Because of this, Bluetooth is very popular and used across many types of devices, from smartphones to kitchen appliances.
Bluetooth devices connect using low-power radio waves with a frequency of around 2.4GHz. When pairing two devices, they connect using one of the 79 available Bluetooth frequencies. Depending on the device and environment, Bluetooth devices can connect anywhere from less than a meter to over a kilometer away.
Bluetooth can be used for a variety of things, including:
- Connecting devices: Bluetooth can help you connect to wireless devices such as speakers, headphones, fitness trackers, keyboards, and smart home devices.
- File sharing: Bluetooth allows you to wirelessly share different types of files, including photos, music, and videos.·
- Hotspot tethering: Using Bluetooth can help you turn your mobile device into a Wi-Fi hotspot, allowing you to share your internet connection with other devices.·
- Security: Certain computers and home security systems may connect to your phone using Bluetooth, allowing you to use it as a key to unlock your house or other security devices.
Like any type of technology, Bluetooth isn’t perfect. To learn more, let’s take a look at its pros and cons.
The pros and cons of using Bluetooth
As with any technology, Bluetooth comes with advantages and drawbacks. Let’s take a deeper look at the pros and cons of Bluetooth.
Pros of using Bluetooth:
- Wireless: Bluetooth technology allows you to connect devices without the annoyance of wires.
- Easy to use: Connecting devices with Bluetooth is quick and easy. Plus, once two devices connect for the first time, they’ll automatically connect in the future.
- Highly compatible: Bluetooth technology allows you to connect devices regardless of their manufacturer or operating system.
- Supports multiple connections: Bluetooth technology allows for devices to maintain multiple connections at once. For example, several devices can connect to a tethered hotspot using Bluetooth.
- Must accept new connections: Whenever connecting to a Bluetooth device for the first time, you’ll have to manually accept the connection. While it’s still possible for somebody to intercept your connection, this helps reduce the risk of unknown users connecting to your device.
Let’s take a look a the cons of using Bluetooth:
- Decreases battery life: Using Bluetooth can drain your battery faster than a wired connection.
- Easy to find: Bluetooth technology makes it easy for users to find other Bluetooth devices in the area, even if you’ve never connected with them before.
- Short range: Most Bluetooth devices tend to lose their connection once the devices are further than 10 meters apart.
- Slow data transfers: Transferring files over Bluetooth can be slower than other technologies such as USB or Wi-Fi.
Now that you know more about Bluetooth, you may be wondering, “Is it secure?” Continue reading to find out.
Is Bluetooth secure? 5 Bluetooth security risks
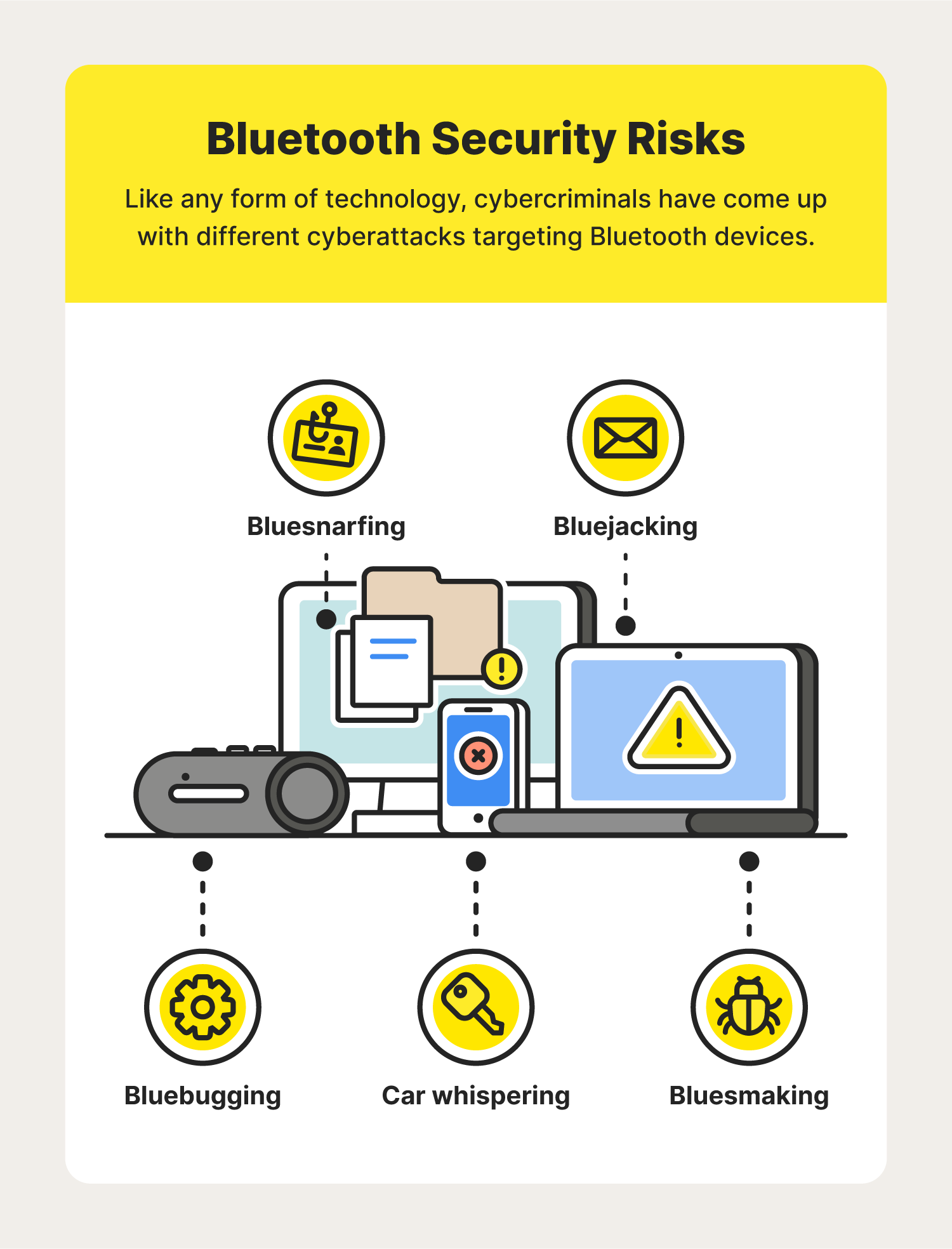
While Bluetooth is widely used due to its convenience, it doesn’t come without its risks. In fact, cybercriminals found clever ways to take advantage of this technology for their own benefit. Here are some of the most common Bluetooth security vulnerabilities today.
Bluesnarfing
Bluesnarfing is a vicious cyberattack that steals information from your device using a Bluetooth connection. In a successful bluesnarfing attack, a hacker can gain access to your photos, text messages, emails, and more. Once the attacker gains this information, they can use it for criminal activities such as identity theft.
Bluejacking
Bluejacking is when a Bluetooth device sends unsolicited spam and phishing messages to another Bluetooth device. In addition to being annoying, these messages may also contain malicious links and attachments that might include malware.
Bluebugging
Bluebugging is a type of attack in which a cybercriminal gains backdoor access to your device using a secret Bluetooth connection. Once your device is bluebugged, a hacker can spy on you and access your private data. In some cases, a cybercriminal may use this information to impersonate you.
Bluesmacking
Bluesmacking is a denial of service (DoS) attack designed to overwhelm your device and force a shutdown. Cybercriminals attack your device by sending oversized packets of data. Hackers will use bluesmacking as a gateway for more severe attacks once your device is shut down. In many cases, your device will return to normal once rebooted.
Car whispering
Car whispering is a Bluetooth security vulnerability that targets car radios with Bluetooth capabilities. Hackers use this attack to eavesdrop on conversations and phone calls that take place inside the car. In other cases, the hackers may use the connection to inject audio into the car, oftentimes with malicious intent.
How to safely use Bluetooth: 7 Bluetooth security tips
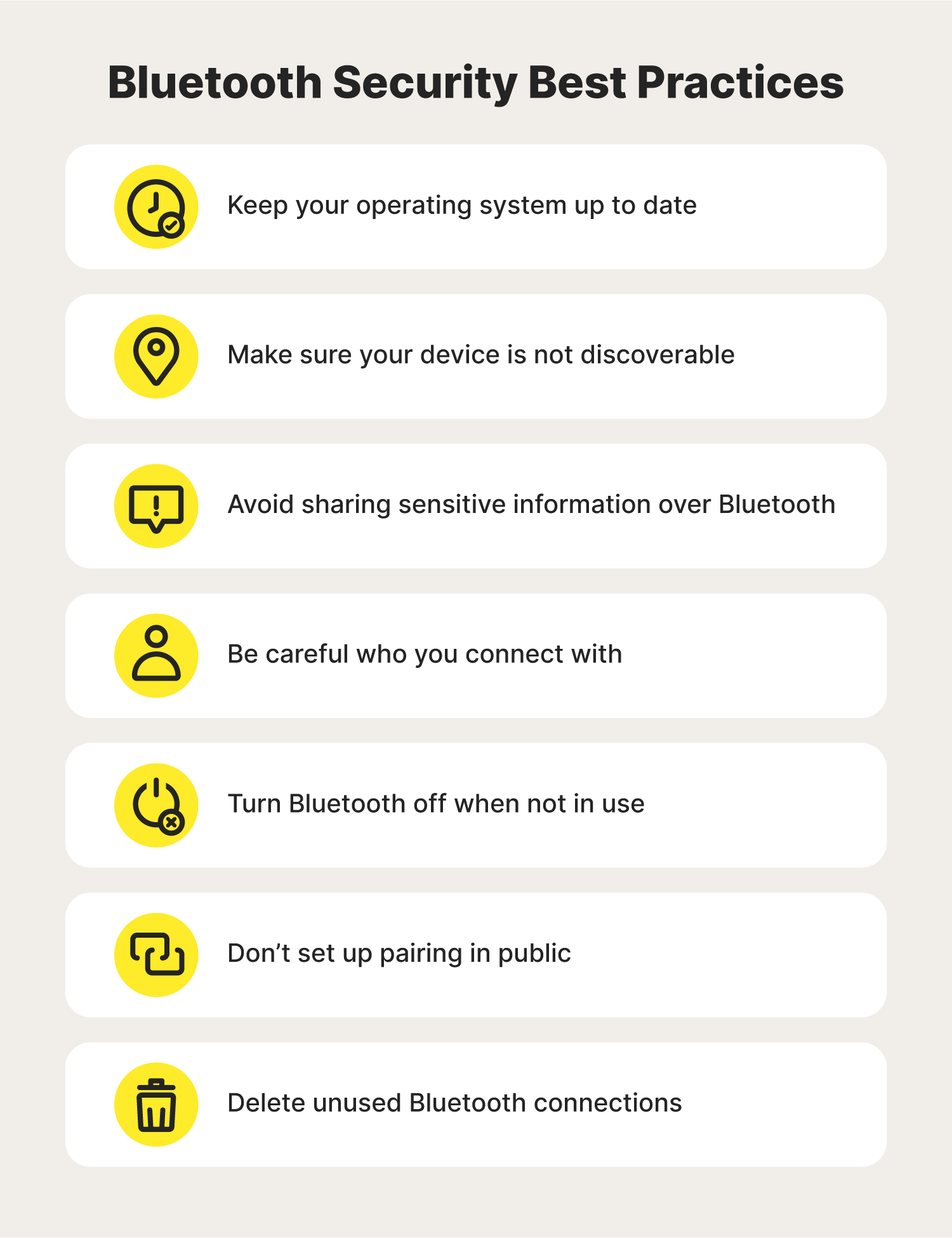
With an understanding of the potential Bluetooth security threats one can face, you may be wondering how you can use it safely. To find out how to use Bluetooth as safely as possible, follow these Bluetooth security best practices.
1. Keep your operating system up to date
A lot of the time, a device with an outdated operating system is an easy target for a Bluetooth hacker. Whether it’s a laptop or a smartphone, keeping your device’s operating system up to date is a great way to ensure you have the best defense against Bluetooth security threats.
2. Make sure your device is not discoverable
One simple way to reduce your risk of being targeted in a Bluetooth attack is to make your device not discoverable. By doing so, it will be much harder for a hacker to ever find your device.
Depending on your device, the steps to do this may vary. Follow along to learn how you can reduce the risk of your device being found by hackers.
How to turn off Bluetooth discoverability on Apple devices:
- Go to “Settings”
- Select “Bluetooth”
- Toggle the switch to turn it off
How to turn off Bluetooth discoverability on Mac devices:
- Go to “System Preferences”
- Click on “Sharing”
- Uncheck the “Bluetooth Sharing” box located on the left-hand menu
How to turn off Bluetooth discoverability on Android devices:
- Go to “Settings”
- Select “Bluetooth”
- Tap “My device”
- Toggle the visibility setting to “Not visible”
How to turn off Bluetooth discoverability on Windows 10 devices:
- Click “Start”
- Go to “Settings”
- Select “Devices”
- Click on “Bluetooth & Other Devices”
- Turn “Bluetooth” on
- Choose “More Bluetooth Options”
- Uncheck the “Allow Bluetooth devices to find this PC” box
3. Avoid sharing sensitive information over Bluetooth
Because Bluetooth communications can be vulnerable to attacks, avoid sharing any personal information over Bluetooth. That way, if you encounter a Bluetooth hacker, your chances of them intercepting your private information are lessened.
4. Be careful who you connect with
Another helpful Bluetooth security tip is to refuse any and all unknown connection requests. In some instances, these requests could be a hacker posing as someone else in hopes to access your Bluetooth device. To play it safe, only accept Bluetooth connections if you are sure you know the device.
5. Turn Bluetooth off when not in use
To help minimize your chances of encountering a Bluetooth attack, always shut your Bluetooth off whenever you aren’t using it. Think of it like locking your door once you leave the house. By having Bluetooth shut off, you aren’t giving hackers the chance to target your device. Not only that, but disabling Bluetooth may also increase your device’s battery life.
6. Don’t set up pairing in public
If you’re pairing two devices for the first time, be sure to do so from a secure location. Pairing devices in public can allow hackers to hijack the pairing process and connect to your device. Instead, pair your devices in a private location so you can minimize the risk of a stranger connecting to your device.
7. Delete unused Bluetooth connections
As a Bluetooth security best practice, get in the habit of deleting any old Bluetooth pairings from your device. While the chances of an old connection being dangerous are slim, it still doesn’t hurt to remove it from your device. That way, if any old Bluetooth devices become compromised, your device won’t automatically connect to it.
By following these Bluetooth security tips, you can use your Bluetooth devices knowing that you’ve done everything you can to help protect yourself from mobile threats. Not only will these tips help secure your device, but they will also enhance your personal cybersecurity.
FAQs about Bluetooth security
Interested in learning more about Bluetooth security? Read through these commonly asked questions for more information.
Will a VPN make Bluetooth secure?
No, using a VPN will not protect you against Bluetooth dangers. But using a VPN is a great way to protect yourself online, especially when using public Wi-Fi networks.
Should I keep Bluetooth on or off?
As a Bluetooth security best practice, it’s best to always turn off your Bluetooth whenever it’s not in use. This can help reduce the chances of a hacker finding your device.
Is Bluetooth safe from hackers?
Like any technology, using Bluetooth has its security risks, making it vulnerable to cybercrime.
How do you know if someone is connected to your Bluetooth?
You can see if anyone is connected to your Bluetooth by going to your Bluetooth settings. From there, you’ll be able to see your current and past Bluetooth connections.
Does Bluetooth use your data?
No, Bluetooth does not use your cellular data. Because of this, it won’t affect your device’s data usage.
How to tell if your Bluetooth is hacked?
Bluetooth attacks are designed to be discrete, so they can be difficult to identify. Some common warning signs that your phone has been hacked include:
- Bluetooth connections to an unknown device
- Unauthorized login attempts to your online accounts
- Increased data usage
- Apps you don’t recognize
- Slow performance
Editorial note: Our articles are designed to provide educational information for you. They may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review the complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc. For more details about how we create, review, and update content, please see our Editorial Policy.





Want more?
Follow us for all the latest news, tips, and updates.