11 warning signs your phone is hacked and what to do if it is
If you suddenly see a surge of pop-up ads, unfamiliar apps on your phone, or a rapidly draining battery, you might be justified in thinking that your phone has been hacked. Learn to recognize the warning signs of phone hacking, and get rock-solid protection with Norton 360 Deluxe.

We bank, search, shop, learn, and share our lives through our phones. Needless to say, there’s a lot of sensitive information stored on these pocket-sized devices, including passwords and credit card numbers. And as AI functionality becomes a standard feature on newer mobile operating systems, phones are storing even more personal data, queries, and user behavior.
A successful mobile phone hacking attempt can enable attackers to see saved data in real time. And with this kind of access, they can potentially commit identity theft, financial fraud, blackmail, and other crimes.
In this post, we’ll walk you through common warning signs of a hacked phone, how to confirm it, what steps to take next, and how to protect yourself from future attacks.
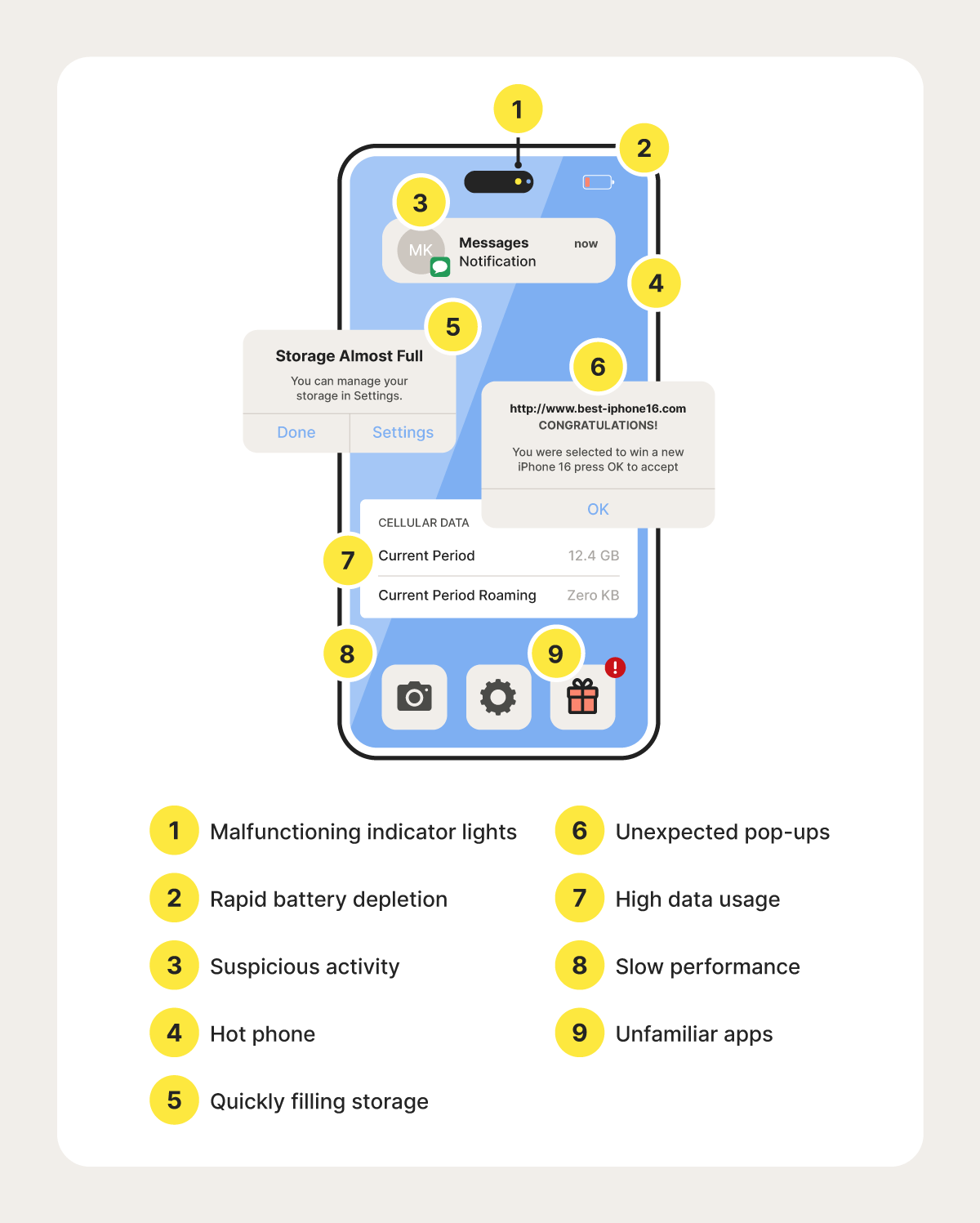
11 signs my phone is hacked
If your phone loses battery, runs slowly, eats up your data, or otherwise starts performing poorly, it could be a sign that someone has unauthorized access to it.
Check out this video for the 5 most common warning signs your phone is hacked, then jump down below to see even more signs.
Here’s a detailed look at 11 potential red flags that indicate your phone could be hacked:
- Indicator lights turn on: Most phones have indicator lights that show when the camera or microphone is in use. If these lights activate when you're not using those features, it could be a sign that a hacker is accessing them to spy on you. But beware that some advanced spyware can access your camera or mic without triggering the indicator lights.
- Battery drains quickly: If your phone use habits haven’t changed but your battery is draining faster than usual, hidden malware may be running in the background and consuming system resources. Confirm if the cause of your battery’s rapid depletion is malware or a hardware problem by checking your battery health in the settings.
- Unusual calls and texts: An accidental dial happens occasionally, but if your outgoing call history is full of calls you don’t remember making, that could be a phone hacking red flag. Similarly, if you suddenly stop receiving calls or text messages, or your contacts claim to have received strange messages, your phone or phone number may be compromised.
- Unwanted verification codes: If you start receiving SMS or email verification codes for accounts you didn't try to access, it could mean someone is attempting to break into your online accounts using your phone number or email address through a technique called spoofing.
- Suspicious account activity or lockouts: You might be dealing with a phone hacker if you get locked out of your accounts unexpectedly or see odd activity, such as password reset requests you didn’t make, or new social media posts.
- Phone overheats: While phones can get warm with heavy use or due to external factors, a phone overheating while idle could be a sign of hacking, since background processes can strain the device’s resources.
- Storage space runs out: Malware can take up significant space on your phone as it installs new files or duplicates existing ones, leading to you running out of storage space faster than expected. Regularly check your storage usage to identify any unexplained increases.
- Unexpected pop-ups: Aggressive and persistent pop-up ads, especially those appearing outside of your web browser, can be a sign of adware installed on your phone without your consent. These pop-ups can be disruptive and sometimes lead to further malicious downloads or websites, so be cautious if you start seeing them frequently.
- High data usage: If you discover an unfamiliar app is consuming a large amount of your cellular data, it could be an undercover type of malware. Often, malware secretly communicates with remote servers, downloads additional malware, or adds your phone to a botnet, all of which are activities that use a lot of data.
- Phone runs slowly: Hacked phones often run slowly because malicious software consumes processing power and memory in the background. On Android devices, you can usually review CPU usage in the settings to identify resource-heavy apps. On iPhones, while CPU load isn’t visible, you can review battery usage to spot apps that may be draining resources unusually fast.
- Unfamiliar apps: While some unfamiliar apps come pre-installed on your device, others could signal a potential hack. Malware often disguises itself as legitimate software to avoid detection. To identify suspicious apps, scroll through your full list of installed applications in your device settings and look for anything you don’t recognize or remember downloading.

How to confirm if your phone is hacked
If warning signs indicate that somebody hacked your phone, you should confirm if malware is present before beginning the recovery process. The simplest way to confirm is to run a reliable malware scan with a trusted anti-malware tool. For a more thorough investigation, you can consult a cybersecurity specialist who can analyze system logs, monitor network traffic, and pinpoint the source of the threat.
Or, you can take the matter into your own hands with Norton 360 Deluxe, which includes a powerful malware scanner built to uncover malicious software hiding in your installed apps, files, and system processes.
What to do if your phone is hacked?
If you suspect somebody hacked your phone, take immediate steps to limit the attacker’s access. To protect your information, accounts, and self, you should:
- Avoid entering personal data like banking passwords or verification codes on the hacked phone until it’s secured.
- Cover your camera, especially if the indicator light is on, to ensure the hacker can’t see you.
- Put your phone on airplane mode to disconnect it from the internet and stop the malware from transferring data or communicating with external servers.
- Use another device to change passwords and set up 2FA on important accounts.
- Back up essential data to a cloud backup service or other trusted source — but only after scanning for malware to avoid transferring infected content to other devices.
How to remove a hacker from my phone
Once you’ve confirmed your phone is hacked and taken the necessary precautions, it’s time to recover your device. Here are some steps you can take to remove malware from your phone:
- Use antivirus software: Run an antivirus scan to detect and remove any viruses, other malware, or dangerous files.
- Remove suspicious apps: Delete any apps you don’t recognize, especially those draining battery, hogging data, or requesting excessive permissions.
- Clear your browsing history: Wipe your browser’s history and cache to remove malicious scripts and tracking cookies that could compromise your privacy.
- Delete unfamiliar devices: Review connected devices in your Google, Apple, and social media accounts. Remove any unknown devices immediately to prevent unauthorized access.
- Reset your phone: If all else fails, perform a factory reset to wipe your device. Back up important files first, but don’t restore from your most recent backup, as it may contain malware and reinfect your phone.
How to protect your phone from hackers
As zero-click attacks become more common, it’s more important than ever to keep phone apps and operating systems updated. This helps keep attackers from exploiting device vulnerabilities and hacking your phone.
You can also take several other safety measures to protect your phone from hackers who are still relying on older attacks, too:
- Don’t click suspicious links: Avoid tapping on unknown links in texts, emails, or pop-up ads. They could trigger malware downloads or direct you to phishing sites.
- Use a password manager: A password manager helps you generate strong, unique passwords for every account, so even if one is compromised, the rest stay secure.
- Update passwords: To keep your accounts secure, change your passwords immediately after a data breach or suspicious activity is detected.
- Protect your data with a VPN: A VPN encrypts your internet traffic and shields you from hackers, especially on public Wi-Fi networks.
- Add security measures: Enable two-factor authentication (2FA) and use biometric features like fingerprint or facial recognition for added account protection whenever possible.
- Turn off Bluetooth: When not in use, disable Bluetooth to prevent hackers from exploiting open connections to your phone.
- Don’t jailbreak your phone: While jailbreaking might give you more control, it also removes built-in protections, making it easier for hackers to access your device.
Maximize your mobile protection
While the idea of a hacked phone is scary, you can take steps to prevent it by being smart about what you click, download, and store on your phone.
For stronger protection, use Norton 360 Deluxe. Its award-winning threat-detection engine helps block malware and hackers, while the built-in VPN encrypts your internet connection against unwanted intrusions, even on public Wi-Fi. Take control of your mobile security today.
FAQs
What is the number to check if your phone is hacked?
There’s no single number to dial that confirms a hack. However, there are several Unstructured Supplementary Service Data (USSD) codes that can reveal suspicious activity, like call forwarding, SMS redirection, or unexpected network settings. These short codes won’t detect malware, but they can help uncover signs that your phone is being tampered with.
Can someone hack my phone and see everything?
Yes, if your phone is compromised, a hacker could gain access to everything — photos, texts, GPS location, microphone, camera, and even saved passwords. This typically requires powerful spyware, such as Pegasus, or a highly targeted phishing or other social engineering attack.
Does turning off your phone stop hackers?
Temporarily, yes. Shutting off your phone disables active connections and running processes, halting most hacking attempts. But once it’s powered back on, any hidden malware or backdoors may resume functioning, so it’s not a permanent fix.
Editorial note: Our articles are designed to provide educational information for you. They may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review the complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc. For more details about how we create, review, and update content, please see our Editorial Policy.










Want more?
Follow us for all the latest news, tips, and updates.