What is an advanced persistent threat (APT)?
APTs can quietly steal sensitive data for years. Learn how these stealthy attacks work — and how to defend yourself if cybercriminals breach a network you use. Then get a powerful privacy tool like Norton VPN to encrypt your traffic, shield your data, and keep your personal info safer.

What is an advanced persistent threat?
An advanced persistent threat (APT) is a stealthy, sophisticated, and sustained cyberattack that aims to steal sensitive data or disrupt essential government, financial, or power grid operations. These attacks can go undetected for long periods of time, with hackers leveraging tools and methods like rootkits and steganography to conceal their presence and carry out malicious activities.
Common APT targets typically include government agencies, businesses, and researchers. Here’s a closer look at organizations that are often targeted and why:
- Governments may have classified information, military secrets, or political intelligence that attackers can use to gain a strategic advantage or influence.
- Critical infrastructure like energy, water, transit, and telecommunications can be disrupted to gain bargaining power or simply wreak havoc.
- Large corporations may possess intellectual property or proprietary data that attackers can use to gain a competitive edge or hold for ransom.
- Financial institutions store account holder data and records that hackers can leverage to commit financial fraud or identity theft.
- Research groups create cutting-edge technology and make scientific advancements that APT attackers may steal for their — or their nation’s — benefit.
Advanced persistent threats don’t usually target individuals. However, you could still be affected if the disruptions lead to widespread service outages, economic instability, or personal data exposure.
Who is usually behind an APT attack?
Typically, governments, state-sponsored groups, hacktivists, or other well-funded crime organizations are behind APTs. These attacks require extensive resources, specialized expertise, and persistent effort, so it’s usually unrealistic for individual hackers or small-time cybercriminals to carry them out.
Advanced persistent threat lifecycle
The advanced persistent threat lifecycle involves an attacker gaining access to an organization’s network (infiltration), moving laterally on the network to infect other connected devices and systems (expansion), and routing stolen data to a location they control (exfiltration).
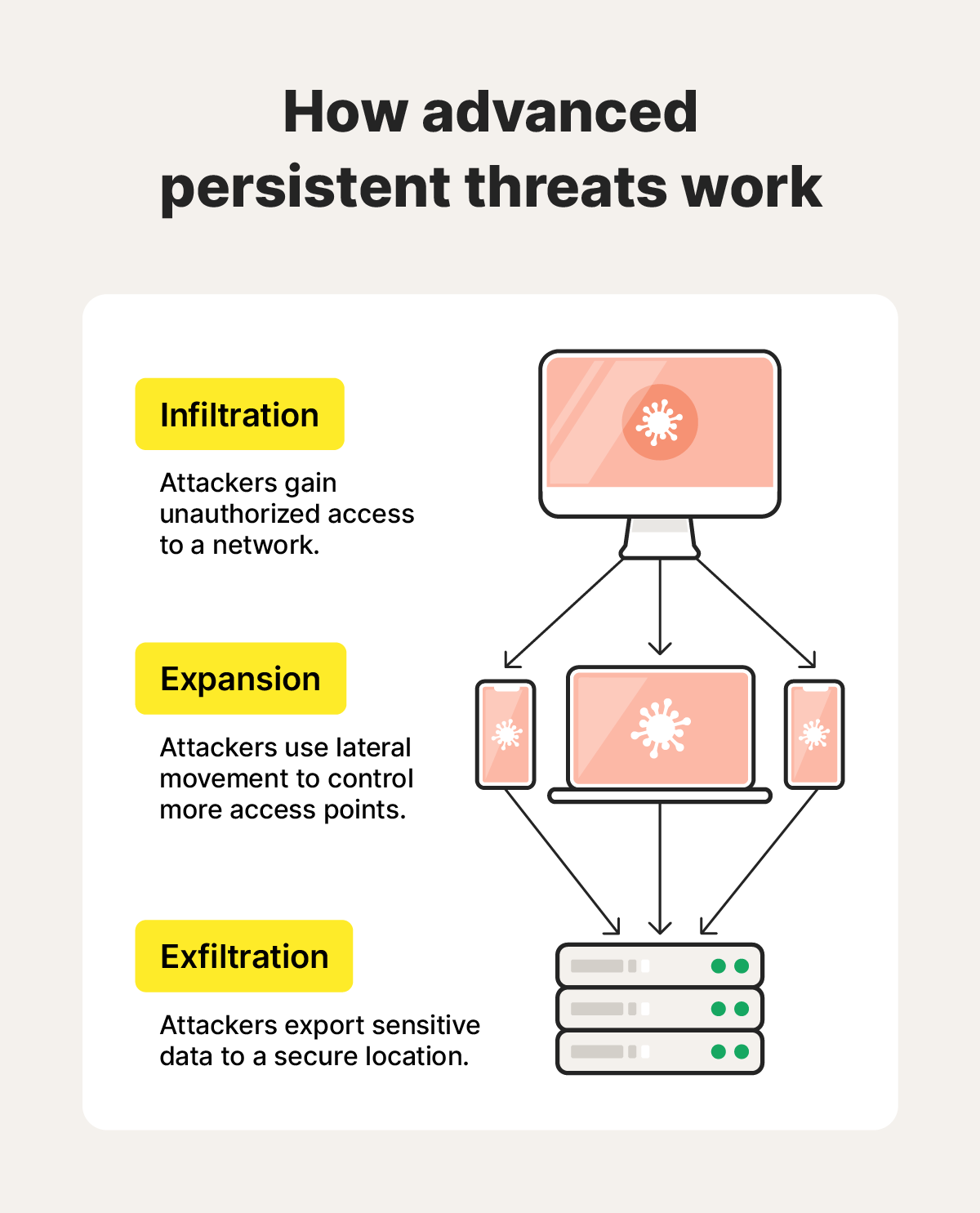

Here are some more details about different steps in the APT lifecycle.
1. Infiltration
Infiltration is the initial stage of an APT attack. A specialized team of attackers selects a target, completes in-depth research to determine the most effective tools and tactics for infiltration, and gains unauthorized access to the target’s network. Often, this involves spyware, social engineering, drive-by downloads, SQL injections, or spear phishing.
Once they’re in, they can establish a foothold, which paves the way for expansion.
2. Expansion
After infiltration, the hackers expand their attack and burrow deeper into the compromised network through lateral movement. During this process, attackers compromise other network devices, systems, and servers, often creating “backdoors” — or hidden access points — as they go.
With control over multiple network connection points, attackers can establish “persistence” by installing hidden mechanisms to maintain access and re-enter at will, making it harder for security teams to detect and eradicate them.
They may steal administrator credentials through keyloggers or pass the hash attacks to gain access to restricted data and resources without creating abnormal network activity.
3. Exfiltration
During exfiltration, attackers transfer encrypted data to a location under their control.
Often, they take a “low and slow” approach to exfiltrate small amounts of data over time. This avoids alerting detection systems that search for large, sudden spikes in outbound traffic. They may also mask their illicit activity by establishing covert channels — encrypted network pathways that obscure in-transit data.
To maintain their foothold and avoid detection during exfiltration, attackers sometimes employ techniques like steganography (to hide stolen data within seemingly innocuous files), schedule transfers during off-peak hours, or launch a Denial of Service (DoS) or Distributed Denial of Service (DDoS) attack as a smokescreen to overwhelm networks and security teams.
Advanced persistent threat characteristics
APTs rely on stealth and evasion techniques, lateral movement, cutting-edge malware, and a low-and-slow approach to exfiltrate data without detection.
However, this isn’t what you’ll see on the receiving end of an attack. Instead, you’ll likely notice warning signs such as:
- Unusual account activity: You might notice unusual account activity, like logins from unfamiliar locations or at odd hours.
- New admin accounts: APT attackers may also create entirely new administrator accounts to gain more access with less monitoring.
- Network slowdowns: If the attackers are hasty and transfer large amounts of stolen data, they could consume significant bandwidth and slow down the internet.
- Data usage spikes: Sudden or recurring spikes in outbound network traffic, especially during off-peak hours, can indicate that someone is exfiltrating large volumes of information.
- Unfamiliar files: Attackers often install malware on compromised devices, so you may find unfamiliar files or applications on your device. You might also encounter device performance issues, a side effect of an infection.
- Disabled security tools: To fly under the radar, attackers sometimes disable antivirus software, firewalls, or intrusion detection systems to operate unnoticed.
Advanced persistent threat examples
There are several common threads between well-known APT attacks — they’re often state-sponsored, utilize custom malware or phishing, and aim to steal information or disrupt critical infrastructure for political gain. Here are some examples:
1. Goblin Panda
Goblin Panda is a China-based cyber espionage group that mostly targets Southeast Asian countries, especially Vietnam. Activity increased amid territory disputes in 2014 and has primarily affected the Vietnamese government, defense, and energy sectors.
2. Fancy Bear
Fancy Bear is a Russia-based group widely believed to be associated with Russian military intelligence (GRU). It is known for creating spoofed sites, launching credential-harvesting campaigns, and deploying malware to collect sensitive information. To date, it has primarily targeted government, aerospace, defense, and energy sectors in the U.S. and Western Europe.
3. Cozy Bear
Cozy Bear is another state-sponsored Russian hacking group, allegedly associated with the Russian Foreign Intelligence Service (SVR). Like Fancy Bear, this APT closely aligns with Russian interests. However, Cozy Bear has evolved to target governments, critical infrastructure, corporations, and supply chains, often by exploiting zero-day vulnerabilities to maintain stealthy access.
In 2015, Cozy Bear breached the Democratic National Convention, maintaining undetected access for months. Fancy Bear followed with a more overt intrusion in 2016. According to senior justice department officials, these operations were authorized at the highest levels of the Russian government.
4. OceanLotus
OceanLotus, also known as Ocean Buffalo, is an advanced persistent threat group from Vietnam. They’re known to target consumer goods companies, manufacturing firms, hospitality organizations, and political dissidents, journalists, and activists — especially in Southeast Asia. OceanLotus typically relies on social engineering, watering hole attacks, and custom malware to invade private networks.
In 2020, cybersecurity researchers uncovered evidence that Ocean Buffalo was infiltrating China’s Ministry of Emergency Management and the Wuhan provincial government to collect intelligence about COVID-19.
5. Elfin Team
The Elfin Team is an Iranian APT group that attacks governments, corporations, and groups involved in engineering, manufacturing, aerospace, and energy research. Their exploits have affected Saudi Arabia, the U.S., and other countries. It’s believed that some targets were selected to prepare for future supply chain attacks.
In 2019, the Elfin Team attempted to infiltrate Saudi Arabia’s chemical sector through a WinRAR vulnerability. This would have enabled them to execute malicious programs, potentially compromising the organization’s critical systems.
6. Titan Rain
Titan Rain was a series of Chinese state-sponsored attacks on U.S. and U.K. government agencies in the early 2000s. Reliable specifics about Titan Rain’s exploits are few and far between. However, it is known that the attackers, active since at least 2003, successfully breached the U.S. State Department, Department of Homeland Security, and the U.K.’s Ministry of Defense and Foreign Office.
7. Helix Kitten
Helix Kitten is thought to be an Iran-based advanced persistent threat group that targets the aerospace, government, energy, financial, telecommunications, and business sectors of countries including Bahrain and Kuwait. This group is known for carefully researching its targets to execute spear phishing attacks to support Iranian state intelligence operations.
In 2018, a cybersecurity company found that Helix Kitten was targeting a telecommunications company to collect large amounts of data for intelligence purposes. The attackers aimed to intercept sensitive communications, exfiltrate information, and potentially deploy additional malware to extend their access.
8. Equation Group
The Equation Group is an advanced persistent threat group believed to be linked to the U.S. National Security Agency (NSA). Active since at least the early 2000s, they have targeted governments, militaries, and critical infrastructure organizations across Africa, Asia, Europe, and the Middle East.
In 2009, the group reportedly distributed infected CD-ROMs to participants at science conferences, embedding trojans designed to exploit unknown vulnerabilities. In at least one case, malware installed the DoubleFantasy backdoor, potentially granting attackers persistent access to monitor activities and steal sensitive research.
Advanced persistent threat prevention
The most effective ways to defend against APTs are to avoid falling for infiltration tactics like phishing and social engineering, increase your security measures, keep software updated, and invest in cybersecurity tools.
Here’s a closer look at what prevention might look like for you:
- Keep an eye out for phishing attacks: Know how to recognize potential threats to help avoid clicking on a phishing link and attackers infiltrating your network. If you can’t tell if a message is legitimate, run it through an AI-powered assistant like Norton Genie to assess red flags before interacting with it.
- Learn to recognize social engineering: Early identification of a social engineering attempt can disrupt the infiltration phase of an advanced persistent threat.
- Set strong passwords: Create strong and unique passwords to make it more difficult for attackers to access restricted data and move laterally within a network.
- Enable biometric identification: Use biometrics like your face, iris, or fingerprint to access sensitive data; it’ll be more difficult for APT attackers to gain unauthorized access, since physical traits are harder to replicate.
- Update your software: Software updates often patch known vulnerabilities, limiting the entry points attackers can exploit.
- Use a VPN: A virtual private network (VPN) can help make you and your internet activity less visible to snoops. It can also help keep attackers from intercepting sensitive data while it’s in transit.
- Install antivirus: Antivirus software can help protect against, detect, and remove malware installed during an APT attack. Just keep in mind that it may not catch all advanced persistent threats if they utilize new or custom technologies.
- Limit privileges: By enforcing strict access control and limiting user privileges, organizations can prevent attacks from spreading laterally and minimize the overall impact of a potential data breach.
Encrypt your internet connection with a VPN
Because advanced persistent threat attacks are so sophisticated, they can lurk on a network undetected for a long time. To limit the potential impact and scope of a breach, take steps to defend your data. Start by using a VPN — an essential component of a robust cybersecurity strategy.
While no VPN can guarantee protection against advanced persistent threats, Norton VPN safeguards your digital privacy by encrypting the data you send and receive online — making it unreadable to snoops and cybercriminals.
FAQs
What is the main goal of an APT attack?
The main goal of an advanced persistent threat attack is to establish a long-term, undetected presence on a target’s network to steal sensitive data.
What differentiates an APT from other malware?
An APT differs from other malware because it’s an advanced and prolonged cyberattack. These attacks frequently employ sophisticated, difficult-to-detect malware to infiltrate systems for long-term strategic goals, such as espionage or intellectual property theft.
This is unlike typical malware, which hackers often use for quick financial gain, to disrupt operations, or to vandalize. Similar to Pegasus spyware, APTs are only used by highly sophisticated hacking groups.
How does an advanced persistent threat work?
An advanced persistent threat involves an attacker infiltrating a network through a vulnerability or human error. Then, they move laterally on the infected network to get more footholds. Finally, they exfiltrate data over the course of months or even years.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.








Want more?
Follow us for all the latest news, tips, and updates.