IoT device security: An ultimate guide for securing your new tech
How do you help improve the security of IoT devices? Follow these IoT device security best practices to help make your gadgets more Cyber Safe.

’Tis the season to be jolly — and increasingly aware of Cyber Safety. This is especially true when it comes to our Internet of Things (IoT) devices and IoT device security. Because, just like us, cybercriminals are eager to embrace the most wonderful time of the year.
If you’re the type of techie who regularly receives IoT devices, such as smart watches, smart-home technology and more of the latest and greatest gadgets as gifts, it’s important to know how to protect IoT devices when you're setting them up. That includes not only protection against viruses and assorted malware but also from prying eyes.
Haven't put any new gadgets on your wish list this holiday? There’s still a good chance you’ll want to purchase one for someone you love, and an even greater chance of you doing the shopping on a connected IoT device. For perspective, Tinuiti found that 59 percent of holiday shoppers intend to gift electronics this holiday season. This is a 9 percent uptick from last year, with the vast majority doing their browsing using their desktop computers, tablets, and smartphones.
This is all to say that everyone should practice heightened Cyber Safety over the holidays. Here, we’ve summed up the most anticipated tech gifts of the holiday season, common IoT security issues, as well as features to keep your information safe. Of course, you’ll also find IoT device security best practices for you to know how to protect IoT devices and ensure your holiday and beyond remains merry and bright.
Top tech gifts over the holidays

According to Statista, the most popular tech devices you can expect to see on wish lists include:
- Smartphones
- Laptops
- Smart TVs
- Fitness tech
- Gaming consoles
What do they all have in common? Well, to a degree, most all are considered internet-connected and fall under the umbrella of IoT devices. Devices revolving around the IoT, such as smart toys to smart homes, remain on the rise. In fact, a study by the Toy Association found that 85 percent of parents have specifically sought out STEM/STEAM smart toys when purchasing presents for their children.
The rise of IoT devices + a need for IoT device security
To help you understand the relevance of IoT devices today, here are a few statistics to demonstrate their current and future impact on consumers and the economy:
- Every second, 127 devices worldwide hook up to the internet for the first time. (McKinsey)
- In 2021, there are more than 10 billion active IoT devices. (Statista)
- There are expected to be more than 64 billion IoT devices worldwide by 2025. (Business Insider)
- IoT has the potential to generate $4 trillion to $11 trillion in economic value by 2025. (McKinsey)
Given this rise in IoT devices, IoT device security is something that should be top of mind for all owners of these devices.
What is IoT device security + why it’s important
IoT device security applies to almost every electronic or piece of tech you own. To be precise, it applies to your internet-connected devices. IoT device security refers to the measures you take to protect your data and online privacy on these devices, from best practices to installing applicable security software, as well as how you harness the built-in security features of each IoT device.
IoT device security issues to recognize
Are IoT devices secure? The truth is that even as IoT devices can be excellent gifts for our very deserving loved ones, they aren't perfect when it comes to protecting against security issues. So, why do we need security in IoT devices? The answer lies in the following IoT device security issues you should be aware of.
Insufficient processing power
Many IoT devices come with a limited storage capacity. This decreases costs for the manufacturer and extends battery life for the consumer. However, this also prevents these devices from using cybersecurity tools like virus scanners and firewalls, ultimately leaving your device and your information vulnerable to cyberattacks.
Application vulnerabilities
Some IoT devices, like smart watches, are synonymous with applications. But older third-party applications may not have the security features seen in more modern applications. These can leave IoT devices vulnerable to cyberattacks. For example, when encryption standards are not met, hackers can potentially intercept personal information or sensitive data associated with your IoT device.
Lack of encryption
Some IoT devices also raise security concerns because of their lack of encryption. Many of today’s IoT devices, such as smart home and toy devices, are not equipped with the capability to securely transfer data from server to server. This can leave data and personal information vulnerable to prying eyes and ears.
Insecure passwords
Some IoT devices have password-related IoT security issues that put the safety of the user’s information at risk. The manufacturers of these devices often input weak default passcodes onto the device that go unchanged after setup. These weak default passwords are easier for hackers to figure out. For this reason, it’s best to ideate a unique password when setting up any new IoT device.
Ignorance of intrusion
A compromised IoT device will typically keep functioning normally from the perspective of the user. Besides bandwidth or power usage issues, there aren’t many clear signs that your IoT device is under attack by a cybercriminal. Leveling up your IoT network security can help, meaning being cognizant of the other devices connected to your internet network. This way, you can flag potentially malicious actors trying to hack into your device.
7 tips for how to protect IoT devices
Now that you know what are the security concerns related to IoT, you might be wondering “How do you ensure security in IoT devices?” Understanding some of the built-in security features of these devices and cybersecurity best practices can help you keep your IoT devices secure.
1. Use complex passwords, patterns, and PINs
Whether your IoT device denotes it as a password, passcode, pattern, or PIN, these are your first line of defense to securing your IoT devices. Think of it like keys to a door — no lock has the same one. The same should go for your passwords across devices and accounts.
To ensure your password’s strength, use different characters, symbols, and capitalization patterns for each of your online accounts. And if you struggle with keeping track of the passwords, consider a password manager that will keep your passwords safe and organized for you.
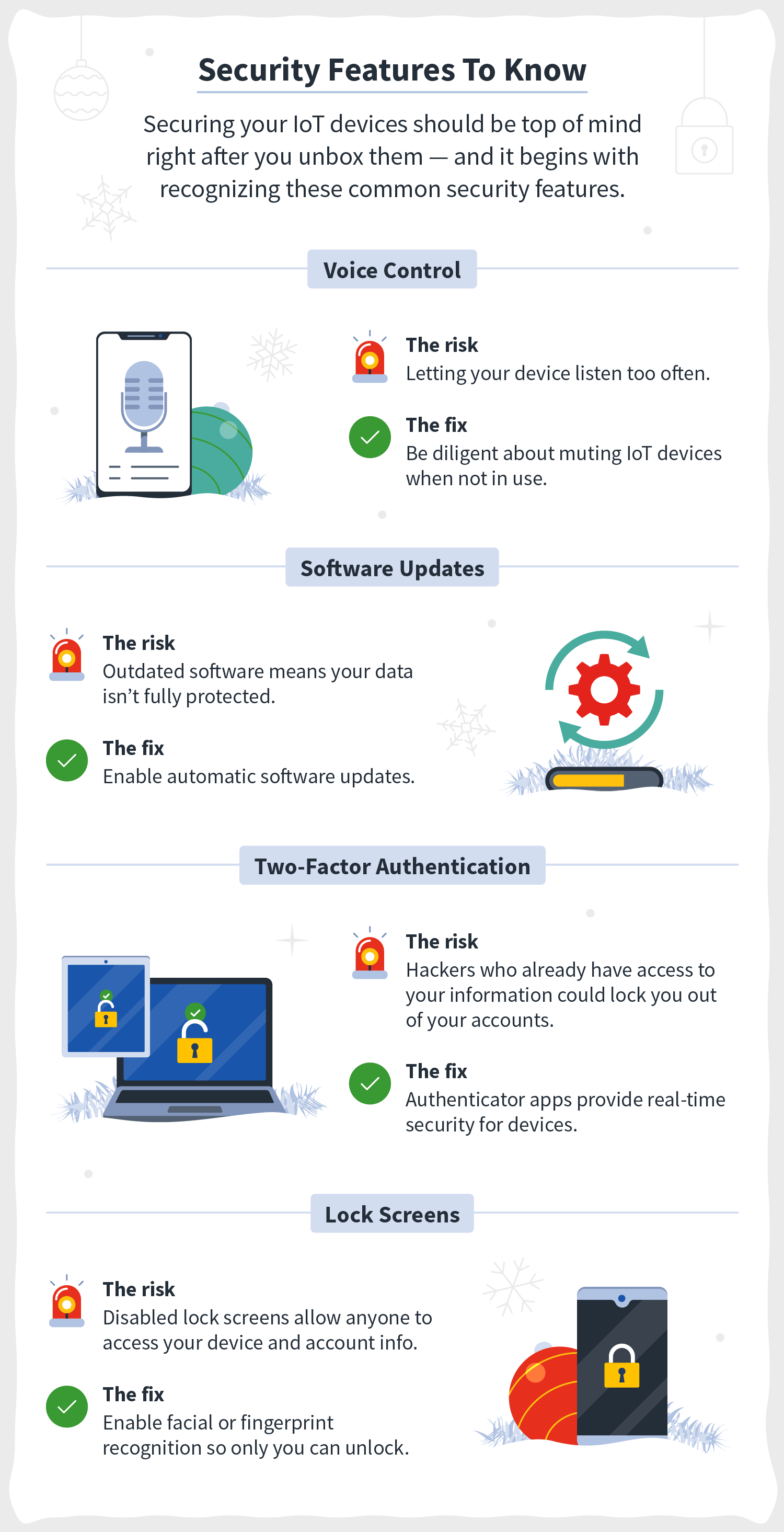
2. Enable lock screens
If a password is the key to your door, a lock screen is the physical door. Leave it open and anyone can walk in. That’s why most IoT devices lock up when not in use and require you to sign in again to access them. To keep your devices protected, enable lock screens so people don’t have direct access to your information.
3. Use voice command
Voice command, or voice activation, has become almost standard on new IoT devices, including Siri on Apple products, Google Assistant on Android, and Amazon's Alexa. There are even refrigerators that can field your grocery list. It makes our busy lives easier to dictate our needs via voice command. And oftentimes these features have voice-recognition software enabled to only listen to their owners' voices.
4. Set up two-factor authentication
Two-factor authentication (2FA), or multi-factor authentication, is a second step in verifying your identity to log in to an IoT device or account. This may be in the form of security questions, verification codes sent via SMS or email, or maybe an additional PIN or password. Some 2FA types are even physical, in the form of hardware tokens like USB drives, and others types are biometric, using tools like facial recognition.
5. Make patching security issues routine
Though most devices can fix security flaws using routine software updates, some IoT devices aren’t designed with this capability. This leaves some technology at a greater risk of being taken advantage of by lurking cybercriminals searching for vulnerable devices.
Consider visiting your device manufacturer’s website to manually search for downloadable security patches that can resolve bugs and security flaws. Patching devices with the latest security features can provide newly gifted devices with an extra layer of protection.
6. Consider segmenting networks
Most successful IoT attack incidents occur when a connected IoT device operates on a network containing sensitive and private user information. To ensure the security of your network and the devices connected to it, consider segmenting your internet network. This can be done by creating a guest network for your more vulnerable IoT devices examples, such as gaming consoles, smart speakers, and smart TVs.
By segmenting your network, you can prevent compromised devices from gaining access to your primary network, which most likely hosts the information hackers are after.
7. Be on top of your IoT network security
As mentioned above, IoT attacks can oftentimes go unnoticed because there aren’t preset security features designed to alert users of suspicious activity. Because of this, hackers can sometimes go unseen for months on end, accessing information as it comes through your network.
To avoid this, keep your IoT network security top of mind by regularly checking for unapproved devices that have found their way onto your network. Taking the time to vet the network your IoT device is on can lessen the likelihood of your data falling into the wrong hands.
More device security tips
When it comes to protecting your IoT devices, you can never be too careful. But the precautions don’t stop there. Consider these cybersecurity safety measures when unboxing other new tech gifts.
Mobile device security
No matter your preference — iPhone, Android, iPad, or other tablets — it’s the apps you download on them that can most often cause security issues on your mobile devices. Malware infections can occur from third-party app stores and also drive-by downloads, whereby you don’t give consent for something to be downloaded. Given the mobile nature of smartphones and tablets, it’s also important to protect them from strangers who might come across them. Consider the following pointers to keep your devices secure:
- Understand what apps you’re downloading and read privacy policies associated with them to inform what permissions you grant.
- Install security software to help ward off cyber threats and protect the private information stored on your IoT devices. Enable your device’s “find my” feature to help you locate it if it’s lost.
- Protect mobile devices from strangers by securing your lock screen using a biometric login versus an easy-to-hack passcode or pattern.
Protect mobile devices from strangers by securing your lock screen using a biometric login versus an easy-to-hack passcode or pattern.
Computer security
We conduct a lot of important business on our laptop and desktop computers. Whether you’re on a PC or Mac, computer security threats — resulting in identity theft, data loss, and even financial loss — often stem from our browsers, plug-ins, and applications. This is why each of these components need special attention upon setup, as well as the following considerations:
- Monitor what personal information you’ve granted your browser access to and whether it really needs that information.
- Install security software for comprehensive protection from cyber threats.
- When browsing, never click on pop-ups.
- Be mindful of whether or not your connection is private.
- Install a VPN to ensure your data is encrypted and illegible to cybercriminals.
Kids are no longer the only ones engaging in video games. According to a survey by FinancesOnline, almost 30 percent of Americans (age 36 – 50 years old) play video games at least once a month. Still, kids under 18 make up almost a quarter of gamers in the U.S., according to the Entertainment Software Association. This means video game security is a topic for everybody, and so are these best practices:
- Install video game security software to ward off cyber threats.
- Use strong passwords across your gaming accounts.
- Use anonymous gamertags that don’t allude to personal information.
- Instill digital citizenship in kids to prevent cyberbullying.
- Consider downloading parental controls to monitor kids’ online activities.
IoT devices change every year, and so do the cybersecurity threats that come with them. Thankfully, there are experts to roll out new security tools to help ensure your holidays stay jolly. In fact, you might consider putting a cybersecurity suite on your own holiday wish list. Better not be naughty.


Cyber threats have evolved, and so have we.
Norton 360™ with LifeLock™, all-in-one, comprehensive protection against viruses, malware, identity theft, online tracking and much, much more.
Try Norton 360 with Lifelock.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.





Want more?
Follow us for all the latest news, tips, and updates.