iCloud Private Relay vs. VPN: Which is better and why?
Think Apple’s Private Relay feature is just like a VPN? It’s a common assumption, but one that could leave your data vulnerable. Here’s a closer look at how iCloud Private Relay works and why it isn’t a like-for-like substitute for the stronger privacy, broader protection, and advanced security features of a trusted VPN.

iCloud Private Relay and VPNs both help protect your online privacy, but their capabilities are far from equal. In this post, we'll break down the differences between the two technologies and help you determine which best suits your online security needs.
What’s the difference between iCloud Private Relay and a VPN?
The main difference between iCloud Private Relay and a VPN is in the breadth of protection they offer. Both help mask your location and online activity, but Private Relay is limited to Safari on Apple devices, while a VPN encrypts internet traffic across browsers, apps, and platforms.
iCloud Private Relay routes your Safari traffic through two separate relays — one run by Apple, the other by a third party — to hide your IP address and encrypt DNS requests. But its protection is limited: it doesn’t cover third-party browsers, non-Apple apps, or traffic outside supported regions.

VPNs, on the other hand, provide full tunnel encryption regardless of which browser or app you’re using, and typically let you choose from a wide range of server locations. VPNs also support a wider range of devices and platforms, making them more versatile for most users.
Here’s how Private Relay stacks up against a VPN at a glance:
iCloud Private Relay |
Virtual Private Network |
|
|---|---|---|
Compatible browsers |
Safari |
All browsers |
Compatible operating systems |
iOS 15, iPadOS 15, and macOS Monterey |
iOS, Android, macOS, and Windows |
How it works |
Encrypts and sends Safari web traffic through two relays. |
Encrypts all internet traffic and routes it through a VPN server. |
Strengths |
|
|
Limitations |
|
|
What is an iCloud Private Relay?
iCloud Private Relay, also known as Apple Private Relay, is a privacy feature included with iCloud+ subscriptions. It encrypts your Safari browsing data and hides your IP address from Apple, websites, and advertisers.
It's a great option for users who primarily browse with Safari and want to reduce web tracking. However, its protection is limited and falls short if you want to use other browsers or apps, or travel outside supported regions.
You should consider using Private Relay if you want to:
- Browse on Apple devices exclusively: iCloud Private Relay is built directly into iOS and macOS devices, including iPhones, iPads, MacBooks, and iMacs.
- Boost your privacy with minimal setup: Once you subscribe to iCloud+, you can enable Private Relay with no additional configurations required.
- Limit web tracking: By hiding your IP address and encrypting DNS requests, Private Relay makes it harder for websites and advertisers to identify you or follow your browsing behavior.
How does an iCloud Private Relay work?
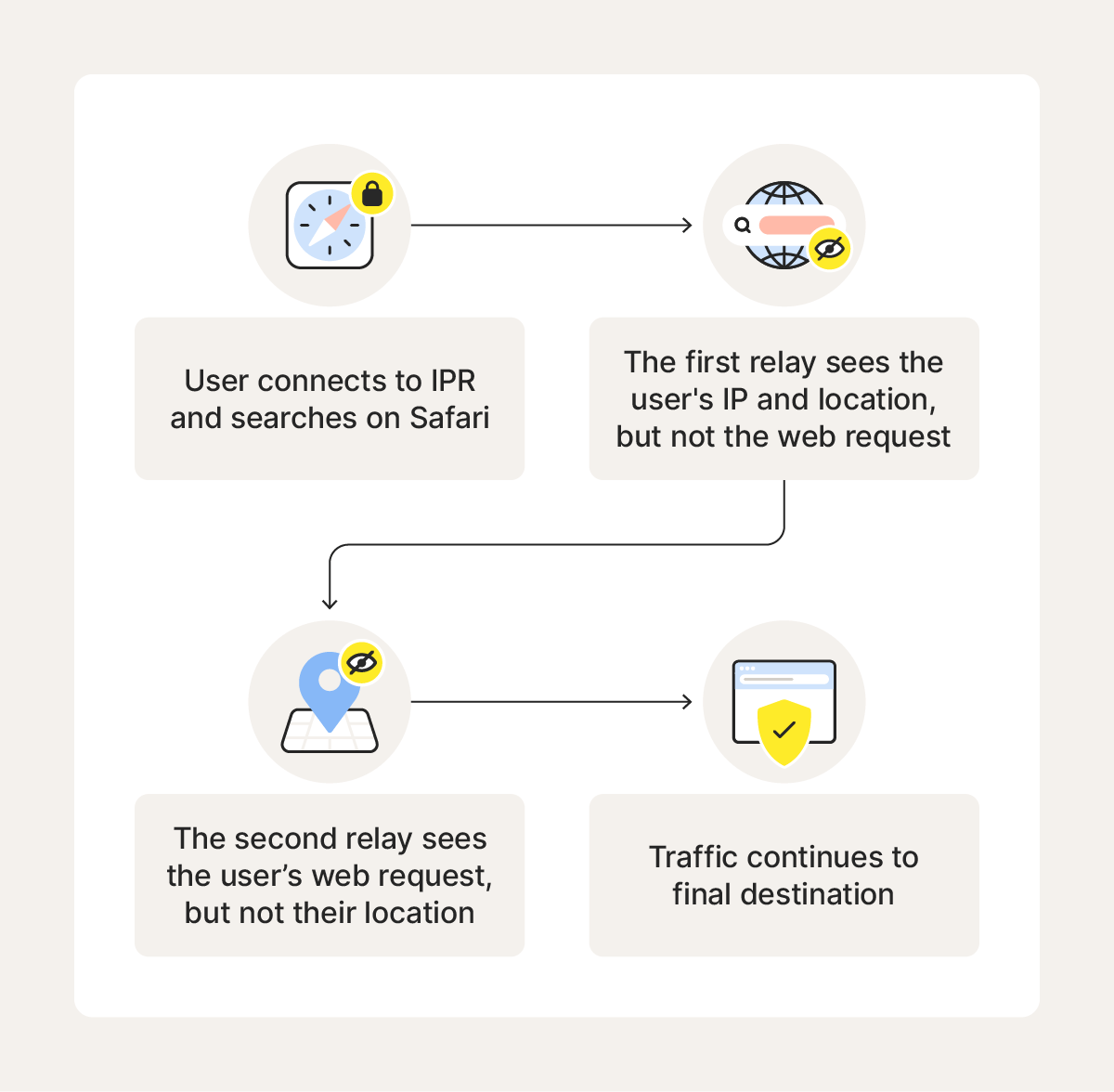
Apple Private Relay works by routing encrypted Safari web traffic through two independent relays — one operated by Apple and one by a third-party provider — to obscure your IP address and browsing destination from any single party.
Here’s how it works, step by step:
1. Request encryption and submission
When you enable iCloud Private Relay and start a Safari browsing session, your device encrypts your DNS records and the URL of the site you want to visit. This encryption ensures that your internet service provider and other intermediaries can’t see the web address you're trying to reach.
2. First relay (ingress proxy)
The encrypted request is sent to the first relay, operated by Apple. This relay decrypts only enough to see your IP address and approximate location (like your city or region), which is used to assign a local relay IP for geo-relevant content. However, it cannot access the actual destination website.
3. Second relay (egress proxy)
Apple forwards the partially encrypted request to a second relay run by a third-party content delivery network (CDN). This egress proxy decrypts the web address and forwards the request to its destination. It can see the website you’re trying to reach, but not your real IP address or precise identity.
4. Website response
The destination website receives and responds to the request as if it originated from the relay server’s IP, not yours. At no point can the website or either relay link your identity with your browsing destination — the data is deliberately siloed to protect your privacy.

Advantages of iCloud Private Relay
iCloud Private Relay provides a simple and accessible privacy solution for Safari users within the Apple ecosystem. Its key benefits include:
- Native integration with Apple devices: Private Relay is built directly into Safari, requiring no third-party apps or extensions.
- Simple Setup: Enabling Private Relay takes just a few taps in the iCloud+ settings, with no need for any in-depth technical configuration.
- Minimal-log policy: Apple Private Relay avoids storing user identifiers, IP addresses, or detailed browsing activity. While some performance and usage metrics are retained to maintain service quality, they aren’t tied to specific users.
Limitations of iCloud Private Relay
While iCloud Private Relay offers convenient, low-effort privacy protection, it comes with notable trade-offs in functionality and flexibility. Here are the main drawbacks:
- Apple-only compatibility: Private Relay is exclusive to Safari and Apple devices, which limits its usefulness for users who rely on other popular browsers such as Chrome or Firefox, or cross-platform workflows.
- Geographic restrictions: Due to regulatory and policy restrictions, iCloud Private Relay isn’t available in certain countries. Users in these regions aren’t able to activate or use the feature, regardless of their device or iCloud+ subscription status.
- Basic feature set: iCloud Private Relay doesn’t offer advanced features typical of a sophisticated VPN, like split tunneling, server selection, or kill switches. This minimalist approach suits general browsing but lacks the granular controls often needed for advanced privacy or networking use cases.
- Potential internet speed reduction: Because Private Relay routes traffic through multiple relays and encrypts DNS and IP data, users may experience minor latency or reduced speeds. While the slowdown is typically negligible, it’s still a trade-off.
- Requires an iCloud+ subscription: Private Relay isn’t free. Although iCloud+ plans start at under $1 per month, the feature is locked behind a recurring subscription — something to consider if you're only looking for private browsing capabilities.
What is a VPN?
A virtual private network (VPN) is a privacy tool that encrypts all internet traffic from your device and routes it through a secure server in a different location. This process masks your IP address, hides your browsing activity, and helps you stay more anonymous online across every browser and app you use.
More enhanced VPNs like Norton VPN go a step further, offering advanced features such as double-hop routing, which sends your traffic through two VPN servers for added privacy, and IP rotation, which frequently changes your IP address to make it harder for trackers to follow your online behavior.
Compared with Apple Private Relay, VPNs generally provide more advanced features, greater flexibility, and better compatibility. Thanks to their stronger, more comprehensive encryption, VPNs offer broader protection for your internet traffic and location data, shielding it from a wider range of network observers including internet service providers and public Wi-Fi snoops.
You should use a VPN if you want to:
- Browse on non-Apple devices: Most VPNs are platform-agnostic, offering protection across Windows, Android, Linux, and other systems, alongside macOS and iOS.
- Use non-Safari browsers and secure apps: Whether you prefer using Chrome, Firefox, Edge, or another browser, a VPN can encrypt your traffic. It also shields data transmitted through other apps, keeping your entire internet connection private.
- Access content while traveling abroad: By connecting to servers in different countries, VPNs help you bypass geo-restrictions and access region-locked services or websites as if you were at home.
- Take control of your privacy settings: With support for customizable encryption protocols, obfuscation, kill switches, and split tunneling, VPNs let you fine-tune your connection to balance privacy, performance, and access according to your needs.
How does a VPN work?
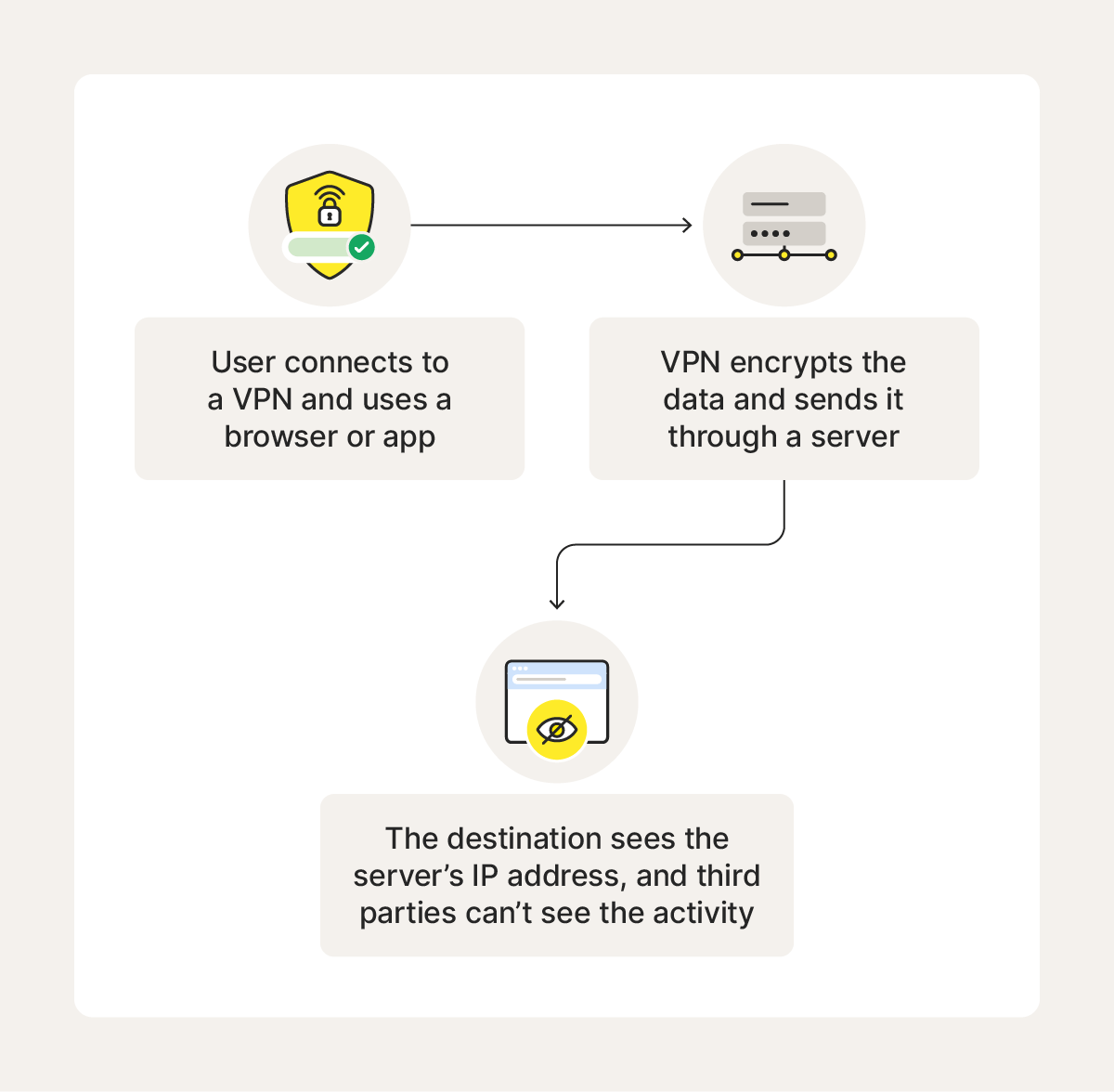
VPNs protect your privacy by creating a secure, encrypted tunnel between your device and the internet. This hides your IP address and ensures that all your online activity is routed through a remote server, making it difficult for websites, trackers, or internet service providers to trace your behavior or location.
Here’s a closer look at how VPNs work:
- You connect through a VPN app installed on your device, which establishes a secure link to a VPN server.
- Your internet traffic is encrypted before it leaves your device — scrambling the data so others can’t see what you’re doing.
- The VPN server routes your data, hiding your real IP address and replacing it with one from its own location.
- Websites and services see only the VPN server’s IP, not yours. Encrypted data travels back through this secure tunnel, keeping your activity private from hackers, ISPs, and other prying eyes.
By rerouting and encrypting all the data you send and receive online, VPNs help cloak you behind powerful anonymity, protecting your personal information and maintaining privacy — even on unsecured public Wi-Fi networks.

Advantages of a VPN
For many users, the advantages of a VPN — such as full-device encryption, broader compatibility, and more advanced privacy controls — make it a more compelling option than Apple Private Relay. Key benefits that users typically value include:
- Comprehensive privacy: VPNs encrypt all internet traffic from your device — not just browser data from Safari — ensuring protection across diverse apps and platforms.
- Device and OS compatibility: Most VPNs work seamlessly on Android, Windows, and Linux (some can even be installed on routers), offering flexibility across ecosystems.
- Stable and reliable connections: Premium VPNs deliver consistent uptime and low latency, even during peak usage, for uninterrupted browsing and streaming.
- Additional security features: Leading VPN providers offer advanced, built-in protections like kill switches, DNS leak prevention, and split tunneling.
- Support for multiple encryption protocols: Users can choose from options like WireGuard, OpenVPN, IKEv2, or Mimic to optimize their connection for speed, privacy, or other criteria.
- Access to a wide range of servers: Often offering thousands of servers in dozens of countries, VPNs allow users to choose servers that suit their needs, whether that’s accessing region-specific content or maximizing their connection speed.
- Control over tunneling preferences: VPNs often let users decide whether to route all traffic through the VPN or only traffic from specific apps and websites, improving performance and usability.
- Commitment to a no-log policy: Trusted VPNs promise not to collect or store user activity data, helping to ensure privacy even in the event of a data request or breach.
Limitations of a VPN
While VPNs are a powerful and flexible tool for protecting online privacy, performance implications, cost, and legal accessibility can be limiting factors for some users. Potential drawbacks of using a VPN include:
- Slower internet speeds and latency: Encryption and routing may impact internet performance since your traffic has to travel through an additional server and undergo encryption and decryption processes.
- Subscription costs: Premium VPNs typically cost more than iCloud+ because they offer more comprehensive protections and a wider feature set. Even so, you can typically get a VPN for just a few dollars a month.
- More complex setup and configuration: Standard VPN setups are generally user-friendly. However, more complex configurations like manual router setup or advanced protocol selection can intimidate non-technical users.
- Legal restrictions in certain countries: VPNs are banned or restricted in places like China, Russia, and Iran.
Protect your privacy and security on any browser
If you want to safeguard your online activity beyond Safari — boosting privacy across all your devices and apps — Norton VPN delivers the all-around protection Apple Private Relay can’t.
With bank-grade encryption, a wide network of over 100 global server locations, and seamless compatibility across operating systems, Norton VPN offers the privacy, security, and performance you need for digital peace of mind.
FAQs
Is iCloud Private Relay a VPN?
No, iCloud Private Relay is a privacy feature, not a full VPN. While it encrypts Safari traffic and hides your IP address, it doesn't provide system-wide protection or offer advanced features like server selection, app-level encryption, or full anonymity across all internet activity.
How do you enable iCloud Private Relay?
To enable Private Relay, go to Settings (or System Preferences on a Mac) > iCloud > Private Relay, then toggle it on. If you’re not already subscribed to iCloud+, follow the on-screen prompts to upgrade before activating the feature.
Can I use iCloud Private Relay with a VPN?
Yes, you can use a VPN while iCloud Private Relay is enabled, but they won’t operate simultaneously. If a VPN is active, traffic will bypass Private Relay and follow the VPN’s routing instead. You’ll benefit from whichever is active at the time, but not both on the same data stream.
How reliable is iCloud Private Relay?
Users report that iCloud Private Relay is sufficiently reliable for regular use, but note that it doesn’t offer the same level of privacy enforcement or versatility as a premium VPN.
What is a private relay on an iPhone?
A Private Relay on an iPhone is an Apple feature that helps protect your privacy by encrypting your Safari browser traffic and routing it through two separate relays. This masks your IP address and location from websites and network providers, making it harder for anyone to track your online activity or pinpoint your exact location.
Does private relay work with Chrome?
No, Apple's iCloud Private Relay is Safari-only. It doesn't protect activity in Chrome, Firefox, or other third-party browsers, nor does it secure in-app traffic. For full-funnel protection, you need a VPN.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.









Want more?
Follow us for all the latest news, tips, and updates.