Split tunneling: What is it, how does it work, and is it secure?
Split tunneling is a game-changing VPN feature that lets you pick the app or site data you want to encrypt while routing other apps or data, like gaming connections, through the regular internet. Find out more about how it works and get Norton VPN to enjoy maximum privacy and performance.

VPNs are essential online privacy tools that establish secure pathways — or tunnels — through which internet data travels, encrypting your in-transit data and masking your location. But sometimes sending all your data through a VPN can be inconvenient, like if you’re using apps that rely on your specific location or trying to print a document locally.
That’s where split tunneling comes in handy, allowing you to exclude some of your internet traffic without having to turn off your VPN completely.
What is VPN split tunneling?
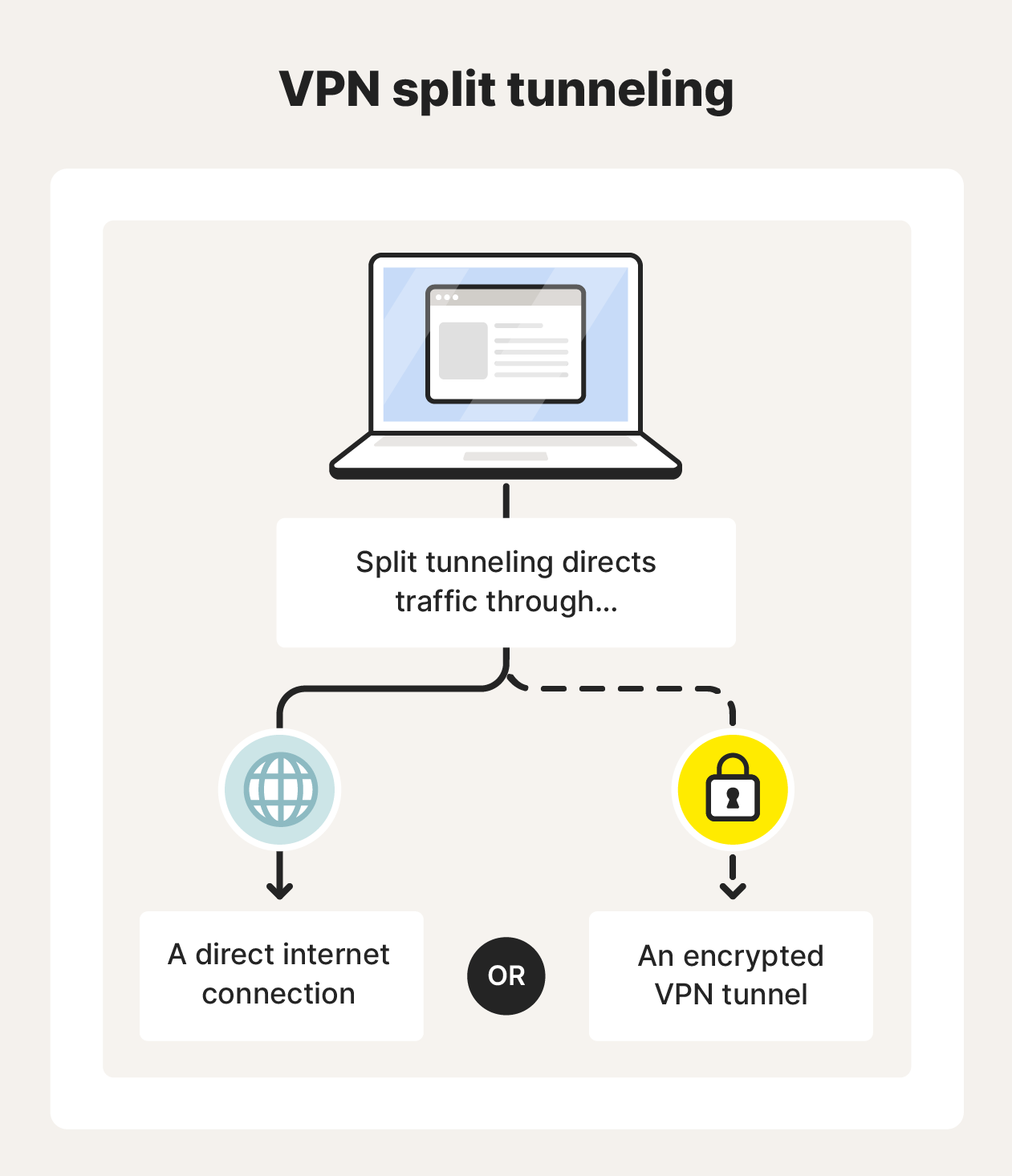
Split tunneling is a VPN feature that routes some traffic through the encrypted VPN tunnel while transmitting other data across the internet directly. This approach enhances flexibility while preserving privacy by only encrypting sensitive data streams, helping to boost your internet speed, reduce bandwidth usage, and maintain a balance between security, performance, and accessibility.
Split tunneling is particularly useful because it lets you access region-specific services and sites that may block VPN traffic while still giving you the benefits of a VPN for other applications. For example, streaming services may stop you from watching if they detect that you’re spoofing your location or connecting via a known VPN IP address.
How does split tunneling work?
Split tunneling works by creating two distinct pathways for your internet traffic — one through an encrypted connection that works just like a standard VPN, and another through your regular internet connection that isn’t secured by VPN protocols.
If you have a VPN with split tunneling, you can configure the app settings to include or exclude specific programs from your secure connection. For instance, you can protect sensitive activities like online shopping or banking from man-in-the-middle attacks while allowing less critical traffic, such as streaming or casual browsing, to bypass the VPN.

Is split tunneling safe?
Split tunneling is safe if you’re using a reputable VPN service that encrypts sensitive activity and masks your IP — especially if you’re on a WPA2 or WPA3-protected network and following other digital security best practices.
However, split tunneling is never as secure as connecting to the internet via a full-funnel VPN for maximum protection against snoops and cybercriminals. To help keep yourself safer while split tunneling, always follow these Cyber Safety tips:
- Use secure messaging apps: Stick to trusted communication apps that use end-to-end encryption such as WhatsApp, Viber, and Signal.
- Use secure email providers: Trusted email services like Gmail or Outlook send messages over a secure Transport Layer Security (TLS) connection.
- Avoid risky networks: Don’t use split tunneling on public Wi-Fi or unsecured networks that could provide an easy backdoor for bad actors.
- Only visit secure web pages: Always check if a website is safe and has an SSL certificate, meaning a secure HTTPS connection will be established between your browser and the server.
And remember, whether split tunneling or not, a VPN won’t protect you against phishing or malware threats, so be sure to pair your VPN with powerful antivirus software to help defend against the full range of threats.
Norton 360 Deluxe is a comprehensive cybersecurity suite combining powerful device protection with a built-in VPN, offering robust security against online threats and ironclad online privacy, all in one, easy-to-use app.
Types of split tunneling
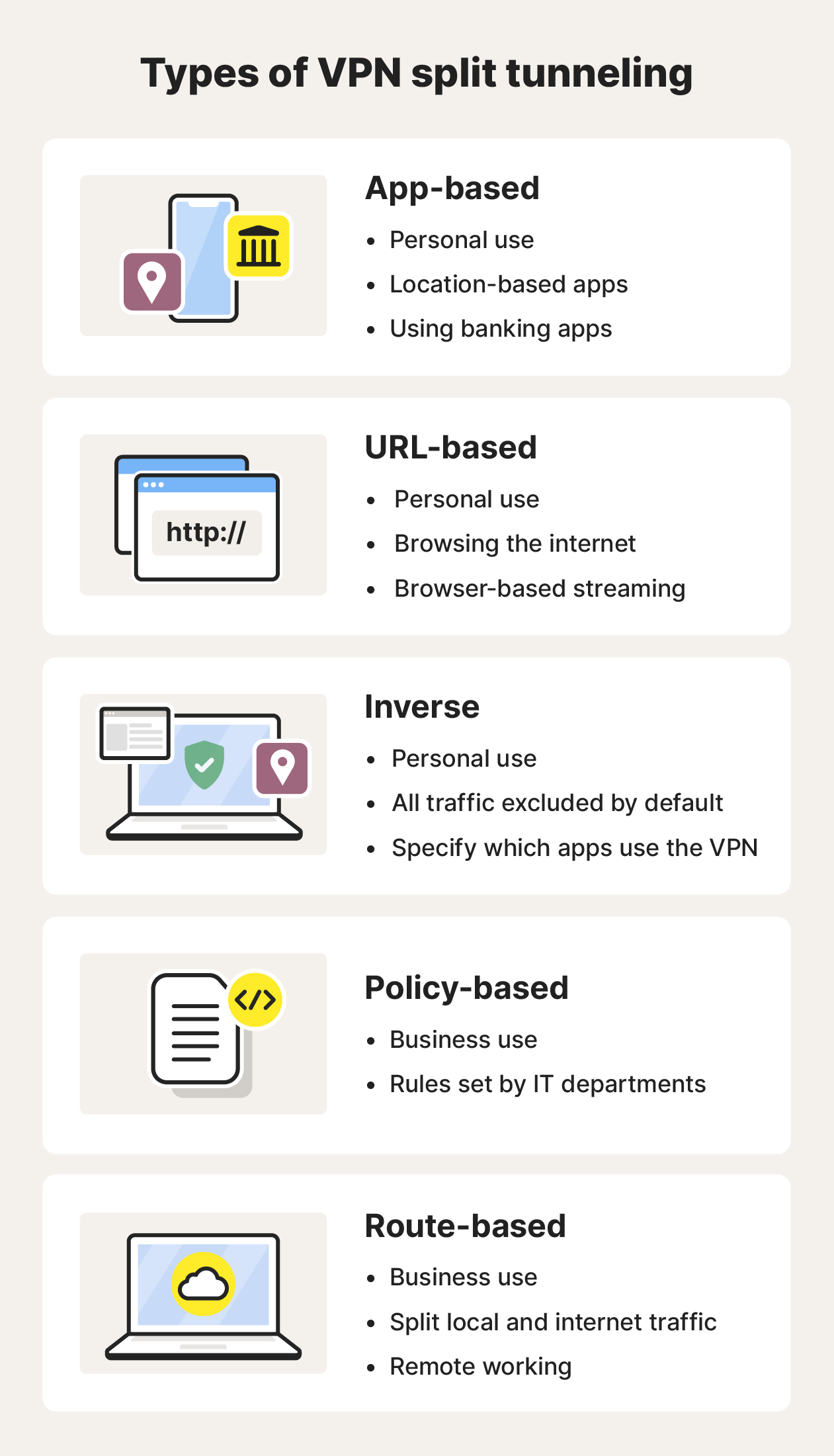
All split tunneling works on the same fundamental principles, but it can be categorized into different types based on how traffic is processed according to different usage categories or criteria, such as apps, URLs, or policies.
Here are the main types of split tunneling and what they do:
- App-based: Lets you choose specific applications to exclude from your VPN.
- URL-based: Allows you to select which websites bypass the VPN.
- Inverse: Specifies which apps or websites you include with your VPN.
- Policy-based: Follows organization-specific rules typically set by IT departments.
- Route-based: Separates traffic between local and internet connections.

The split tunneling options available to you will depend on your particular VPN service. For instance, browser-based SSL VPNs typically only offer URL-based split tunneling, while mobile VPNs for iPhone or Android often use an app-based split tunneling.
Pros and cons of split tunneling
Split tunneling provides flexibility by allowing you to balance your online privacy and performance needs, but it comes with trade-offs. While it can improve speed and efficiency, improper use may expose your data to security risks. So understanding its benefits and limitations is essential to deciding when, how, and if you should use it.
Here’s a breakdown of the pros and cons of split tunneling:
Pros |
Cons |
|---|---|
Faster connections for non-VPN traffic |
Reduced privacy and security |
Reduced bandwidth consumption |
More complex setup and management |
Access to local network devices |
Risk of misconfiguration |
Bypass VPN-blocks |
May violate organizational security policies |
When should you use split tunneling?
You should consider using split tunneling when you're connected to a secure network and only some of your activities require the enhanced privacy of encryption and IP masking. This helps ensure critical data security while lowering your bandwidth usage and allowing other, less-sensitive applications to benefit from faster, direct internet access.
Here are some specific use cases for split tunneling:
- Streaming: Bypass your VPN and access streaming data directly to avoid buffering, slow speeds, or reduced video quality.
- Remote Work: Access corporate resources securely through the VPN while using split tunneling to directly access non-sensitive websites.
- Gaming: Enjoy faster, low-latency video games by routing gaming traffic outside the VPN for lower ping.
- Large downloads: Exclude large, non-sensitive downloads from the VPN to save bandwidth and speed up the process while still securing critical tasks.
- Accessing local network devices: Maintain connections to local devices such as printers or smart home devices without disrupting VPN usage for secure internet browsing.
- Bypassing geo-restrictions selectively: Use the VPN for accessing region-locked content while allowing apps or sites that require your real location to see your local IP address.
- Online Banking: Encrypt financial transactions through the VPN while accessing general websites or other internet services without the extra latency.
How to enable split tunneling on Norton VPN
To enable and configure split tunneling on the Android and Windows versions of Norton VPN, it’s a simple matter of opening the app settings and customizing your preferences.
Norton VPN split tunneling on Android
Here’s how to set up split tunneling on your Android device with Norton VPN:
- Launch the Norton VPN app.
- Tap the Settings icon in the top-right corner of your screen, then VPN Preferences.
- Tap Split Tunneling, then move the slider to enable the feature.
- Under Exclude specific apps from using VPN, tap the checkbox next to the app you want to exclude from the VPN tunnel.
- Turn off the VPN, then turn it on again to apply the change.
Norton VPN split tunneling on Windows
To enable split tunneling on a Windows PC with Norton VPN:
- Open Norton VPN on your PC.
- On the dashboard, click VPN Preferences, then move the slider to enable VPN split tunneling.
- Click Manage Apps under Split Tunneling. In the new window, click Add Application to exclude an app from going through the VPN.
- Follow the on-screen instructions to confirm and save your preferences.
Take control of your online activity
While it’s best to keep your VPN turned on for maximum privacy and security, performance or accessibility issues sometimes mean it’s necessary to disable your connection. Split tunneling lets you have your cake and eat it, too.
Get Norton VPN to access split tunneling on Android and Windows, customize your connection via thousands of geo-optimized servers, and ensure your sensitive internet data is always secured with watertight AES-256 encryption, backed up by a powerful kill-switch feature for ultimate peace of mind.
FAQs
Can I control which traffic goes through a split tunnel?
Yes, you can control which traffic goes through a split tunnel by specifying which apps or websites are routed through the encrypted VPN tunnel and which ones bypass it for direct internet access.
What’s the difference between a full and split-tunnel VPN?
A full-tunnel VPN encrypts 100% of your outgoing and incoming internet traffic, while a split-tunnel VPN lets you select which data streams to exclude or include.
How do I turn off split tunneling?
Most VPN services let you turn off split tunneling by disabling it in the settings menu of the VPN app.
How do I know split tunneling is working?
You can test whether split tunneling is working by accessing a site or service that you’ve chosen to exclude from the VPN and checking your IP address through an IP lookup tool. If the IP matches your local network, the traffic is bypassing the VPN, confirming split tunneling is active.
Editorial note: Our articles are designed to provide educational information for you. They may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review the complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc. For more details about how we create, review, and update content, please see our Editorial Policy.







Want more?
Follow us for all the latest news, tips, and updates.