7 cybersecurity tips for small businesses
As a small business owner, you might think cybercriminals will overlook you, but that’s an assumption they’re banking on. Safeguard your systems by following seven key cybersecurity tips, and learn how Norton Small Business can provide even stronger protection.

Small businesses are prime targets for cyberattacks, including phishing, drive-by-download malware infections, watering hole attacks, and more. Why? Because small business owners often overlook cybersecurity until it’s too late. They don’t have the luxury of dedicated IT teams, making them vulnerable.
That’s likely why nearly half of small business owners have experienced a cyberattack. Unfortunately, about 60% of those affected go out of business within six months due to severe financial loss, operational disruptions, or irreparable reputational damage.
The good news is you don’t need a Fortune 500 budget or dedicated IT staff to bolster your defenses. Below are some cybersecurity tips for small businesses that will help you cover the critical bases — so you can focus on priorities like driving company growth.
1. Train employees on Cyber Safety
Informed employees are key to the long-term success of small businesses and startups. If your staff is untrained in the ways of Cyber Safety, they could also inadvertently expose you to threats by sharing sensitive data with unauthorized people, clicking shady email links, or creating weak passwords.
Make sure your employees are trained on the following topics:
- Phishing scams: Teach employees to look for mismatched email addresses, phone numbers, and website links, as well as watching out for spoofing attempts. They should avoid clicking links or opening attachments until they have verified the sender’s identity.
- Information security: Teach employees how to safely share company data by verifying recipient identities, encrypting messages, and not initiating sensitive transfers while connected to unsecured networks.
- Safe browsing: Teach employees to use secure browsers and be cautious of unfamiliar websites, suspicious pop-ups, and unexpected download prompts. They should also avoid entering sensitive data before verifying a site’s legitimacy.
- Password management: Teach employees to use long, complex, and unique passwords for each account. Use a secure password manager, like the one included in Norton Small Business, to keep track of them, rather than jotting passwords down and leaving them where they can be lost or stolen.
Also, be aware of insider threats — employees with malicious intentions. They may steal sensitive company or client data, sabotage systems, redirect funds, or introduce malware into your network. The best way to protect against this is to monitor for irregular activity and limit access by role.
2. Identify your vulnerabilities
Whether your business is new or under-resourced, you may have vulnerabilities that expose you to cyberthreats. If your network or systems aren’t configured right, you don’t know how to detect malware, or your data isn’t properly backed up, you could suffer financial losses or reputational damage.
Since you can’t fix what you haven’t found, begin with:
- Asset inventory: Create an inventory tracking spreadsheet containing all IT assets (hardware, software, data, cloud services, mobile devices). This will help you monitor attack surfaces that may be vulnerable, so you can take preventive measures.
- Risk assessment: Make another list outlining potential threats beyond software and system vulnerabilities. This should cover insider threats, natural disasters, human error, supply chain risks from third-party vendors, and even physical security breaches.
- Vulnerability scanning: Utilize tools like the Cybersecurity & Infrastructure Security Agency’s scanning service, which monitors publicly accessible websites, systems, and networks for known vulnerabilities.
- Penetration testing: If your business operates in a regulated industry or relies heavily on web-based applications, consider contracting ethical hackers to simulate an attack and uncover hidden vulnerabilities.
- Cybersecurity audit: Each year, confirm foundational security measures are in place, including firewalls, intrusion detection and prevention systems, antivirus, software updates, two-factor authentication, access controls, etc. They should be operational and effective against evolving threats.
3. Implement security protocols
Cybersecurity protocols are rules that help protect company devices, networks, and data from attackers. They often involve authenticating identities, encrypting data, and generally taking steps to minimize risk and prevent unauthorized access.
- Require identity authentication: Implementing two-factor (2FA) or multi-factor authentication (MFA) ensures that unauthorized parties can’t access company systems with just a stolen password.
- Restrict access where you can: Role-based access control (RBAC) ensures that employees only have access to the data and systems they need to do their job. This helps stop malicious insiders and hackers from easily gaining widespread access to critical information and infrastructure.
- Manage contractors: Thoroughly vetting third-party contractors and applying the principle of least privilege (POLP) — granting only the minimum access needed — helps prevent intrusions, reduces attack surfaces, and is often necessary for regulatory compliance.
- Define how employees can use company resources: Establishing an acceptable use policy (AUP) sets clear guidelines for how employees can interact with company devices, networks, and data. This minimizes risky behaviors like downloading unauthorized software or visiting malicious websites.
- Create a Bring Your Own Device policy: If you allow employees to use their own devices for work, lay out strict security measures. At a minimum, require them to use 2FA or MFA, install a virtual private network (VPN), and clearly state any other obligations. You should also provide them with robust antivirus and consider anti-tracking software.
While the following aren’t protocols per se, these technologies should be integrated into your team’s workflow to help strengthen your defenses.
- Scam detection tools: Use an AI-powered scam detector to verify whether a suspicious text, email, or social media message is a scam.
- Website checkers: Use a tool with zero-day phishing detection capabilities to analyze websites for subtle signs of phishing or scams, alerting you to risks.
- Private browsers: Use a secure browser like Norton Private Browser to help block threats like phishing, malware, dangerous websites, malicious downloads, and scams. It also helps enforce set privileges on shared computers by ensuring the next user can’t see past work or searches.
4. Protect your network
Every device on your network is a potential access point for attackers. If you haven’t taken the necessary precautions or correctly configured your network, your entire business infrastructure and sensitive data could be susceptible to network attacks.
Secure your network using:
- Firewalls: These filter incoming and outgoing network traffic based on predefined security rules, helping prevent unauthorized access to your systems.
- Intrusion detection and prevention systems (IDPS): These systems continuously monitor network traffic for suspicious activity or known attack patterns, automatically blocking threats or alerting administrators to potential breaches. They sometimes pick up malicious activity that a firewall misses.
- Secure encryption protocols: Using the latest encryption standards like WPA2 or WPA3 for your Wi-Fi ensures that data transmitted wirelessly is scrambled and safe from eavesdropping.
- Network segmentation: Dividing your network into smaller, isolated subnetworks helps contain breaches. If one segment is compromised, the attack can’t spread throughout your entire network.
- Service Set Identifier (SSID) concealment and default password changes: Hiding your Wi-Fi network’s SSID makes it less visible to casual scanners and opportunistic attackers. Changing the default router password and regularly updating your router’s firmware also make it harder for attackers to gain control of your network.
- Virtual private networks: VPNs, like the one included in Norton Small Business, create a secure, encrypted connection to protect sensitive data in transit, even if your employees are connected to an unsecured network. This is especially useful if you or your employees connect remotely or over public Wi-Fi, which could make it easier for hackers to intercept traffic.
5. Store sensitive data securely
Data storage and handling requirements are more strictly regulated in certain industries, like healthcare and finance, but it should be a top priority no matter your field. A data leak stemming from mishandling can lead to a tarnished reputation, lawsuits, lost intellectual property, higher insurance premiums, fines, and so on.
Keep customer and proprietary data safe from prying eyes with these habits:
- Use the 3-2-1 strategy: This plan relies on redundancy to ensure that important data is always available in the event of corruption, hardware failure, natural disasters, theft, hacking, or a ransomware attack. It requires you to keep three copies of the data: store two backups in different locations, and keep one copy offsite.
- Encrypt data: Whether your data is in storage or in transit, you should encrypt it to protect it from unauthorized access.
- Use secure payment processing: Always use Payment Card Industry Data Security Standard (PCI DSS) compliant payment gateways, and avoid storing sensitive customer card data directly on your own systems. This reduces your liability and the risk of financial data breaches.
- Use cloud storage: Reputable cloud storage services let you securely store sensitive data and access it whenever and wherever you need. Norton Cloud Backup is a reliable and easy-to-use solution with built-in security features that make it a great choice for small businesses.
- Control access: Remember the RBAC and POLP rules (detailed in our third tip) for managing employee and contractor access. Limit sensitive data to only those who need it. Use strong authentication controls to support this.
- Review retention policies: Keeping sensitive data longer than necessary increases risk. Regularly delete or archive data you no longer need to reduce unnecessary risk of exposure.
- Secure endpoints: Ensure computers, phones, and other devices with access to sensitive data have full-disk encryption, strong passwords, and up-to-date endpoint security software.
6. Maintain your systems and software
Regular software, device, and application updates are important for patching security vulnerabilities. As systems age, attackers often find and exploit weaknesses. When this happens, hackers can steal data, install malware, or disrupt network operations with denial of service attacks.
Ensure your systems are always running on the most current version by:
- Enabling auto-updates.
- Allowing software update push notifications.
- Assigning someone on staff to check for updates monthly.
Monitor your social media accounts
Around 96% of small businesses use social media accounts for digital marketing — which means keeping your accounts safe is paramount.
The Norton Small Business Premium plan includes Social Media Monitoring to help safeguard your online presence. By linking your professional business pages to our portal, you gain proactive protection: we’ll monitor for suspicious activity and alert you to potential threats. This helps you effortlessly protect these essential assets — as well as your hard-won reputation.
7. Create an incident response plan
An incident response plan in cybersecurity is documentation that outlines the steps to take before, during, and after a security breach or cyberattack. It can help improve response time, minimize damage, and maintain customer trust.
At a minimum, your plan should include:
- Who to contact internally and externally.
- Who is responsible for what action item.
- Guidelines for notifying customers, employees, and stakeholders.
- Steps for isolating affected systems.
- Data backup and recovery instructions.
- Legal and reporting obligations.
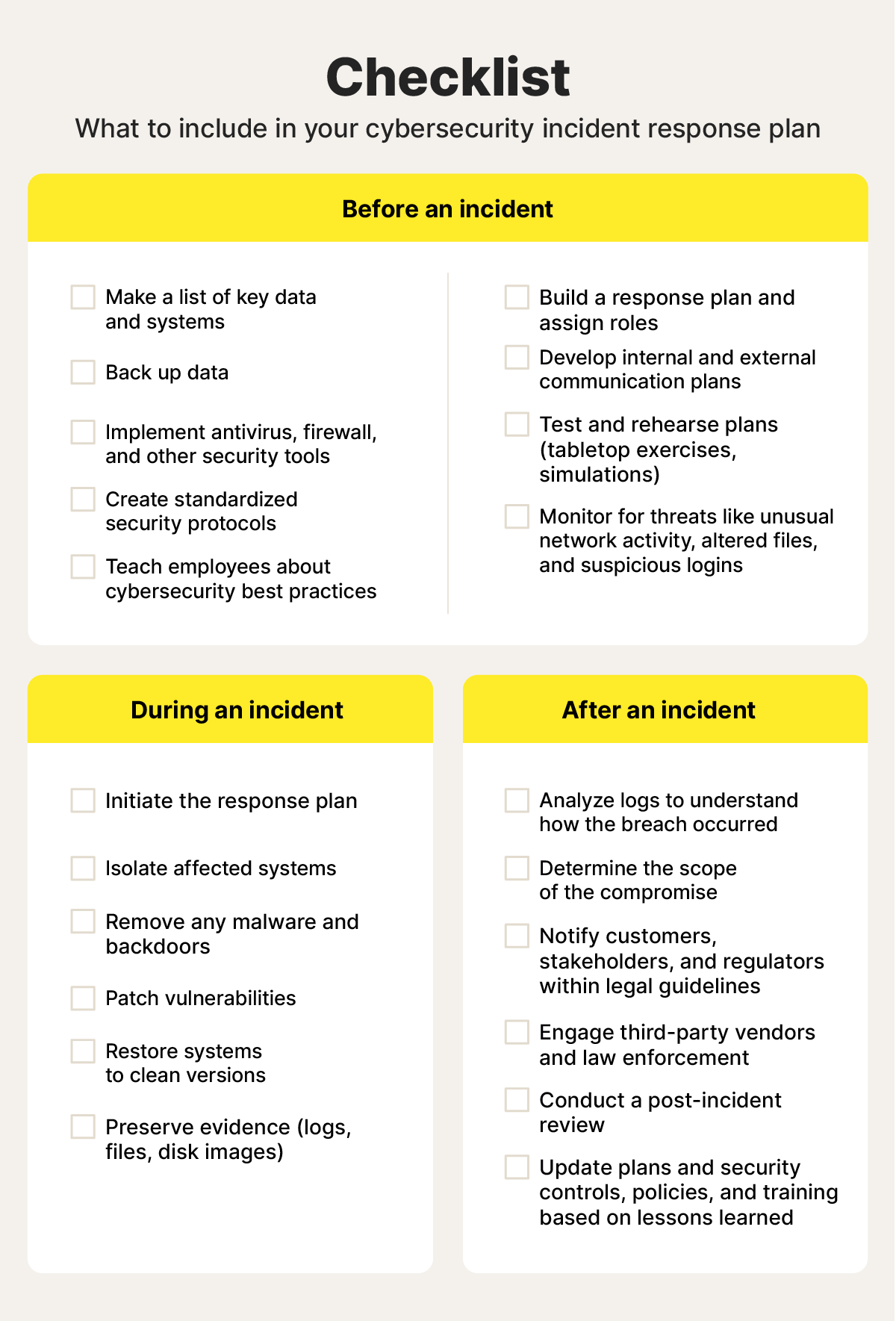

Download your checklist here.
Defend your small business from cyberthreats
Protecting your business from cyberthreats starts from within. Training your employees is a priority, as is arming your network and devices with robust security software.
Antivirus helps detect, block, and remove malware from computers and networks. As a small business, this is a key component to protecting data and preventing disruptions caused by cyberattacks. Norton Small Business offers award-winning antivirus, as well as other privacy and security essentials like cloud backup storage, a password manager, a VPN, and a private browser. Subscribe today to protect your tomorrow.
Editorial note: Our articles are designed to provide educational information for you. They may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review the complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc. For more details about how we create, review, and update content, please see our Editorial Policy.










Want more?
Follow us for all the latest news, tips, and updates.