What is pretexting?
Pretexting is a social engineering attack where a cybercriminal creates a fabricated story to bait their target into revealing sensitive personal or proprietary information, sending money, or downloading malware. This puts the target at risk for identity theft, financial fraud, and future attacks. Follow this guide to learn more about pretexting tactics and protection tips. Then get Norton 360 with LifeLock Select to help protect against pretexting attacks and identity theft.

What is pretexting and how does it work?
Pretexting in cybersecurity is a social engineering attack where a scammer creates a fictitious identity, steals someone’s identity, or creates a scenario to manipulate their target into disclosing information they otherwise wouldn’t.
To understand how pretexting attacks work, you might think of it as writing a story. The scammer makes up a believable story (a pretext) and casts themselves as a character. This character could be an authority figure like a lawyer, prospective employer, colleague, banking institution, tax fraud investigator, or hospital administrator. Or, they may assume the identity of someone you care about, such as a love interest, trusted friend, grandparent, or child.
Once the scammer establishes baseline credibility, they can gain the target’s trust using a plot device like:
- Pretending to be a grandchild who needs money to pay for an unexpected hospital visit.
- Catfishing the target, forming a long-term relationship, and making large requests.
- Posing as a potential employer and requesting sensitive information like a Social Security number (SSN) or requesting free “trial” work.
- Assuming the identity of an IRS agent and demanding the target pay overdue taxes.
- Pretending to work for a credit card company and asking a target to confirm their account details.
Running an OfferUp scam where they pretend to be interested in buying something in order to share verification codes or other information.
Then, they can use the information they obtain to steal money, open new accounts, change existing passwords, scam others, and more.
Is pretexting legal?
Pretexting is generally unlawful in the U.S., but most existing legislation about pretexting is industry-specific and doesn’t mention individuals carrying out these attacks. The most well-known piece of pretexting-related legislation is the Gramm-Leach-Bliley Act which prevents financial institutions from using deceptive practices to access private information. However, there are also laws that regulate the healthcare industry and general business practices.

While pretexting may not be explicitly illegal for an individual (unless the target hasn’t given consent), pretexting can lead to charges of identity theft and fraud. However, there are a couple of caveats. First, pretexting is legal in personal relationships if there are no negative repercussions. For example, using pretexting to plan a surprise party or buy a gift is acceptable. Law enforcement can also legally use pretexting to gather evidence during active investigations.
Types of pretexting techniques
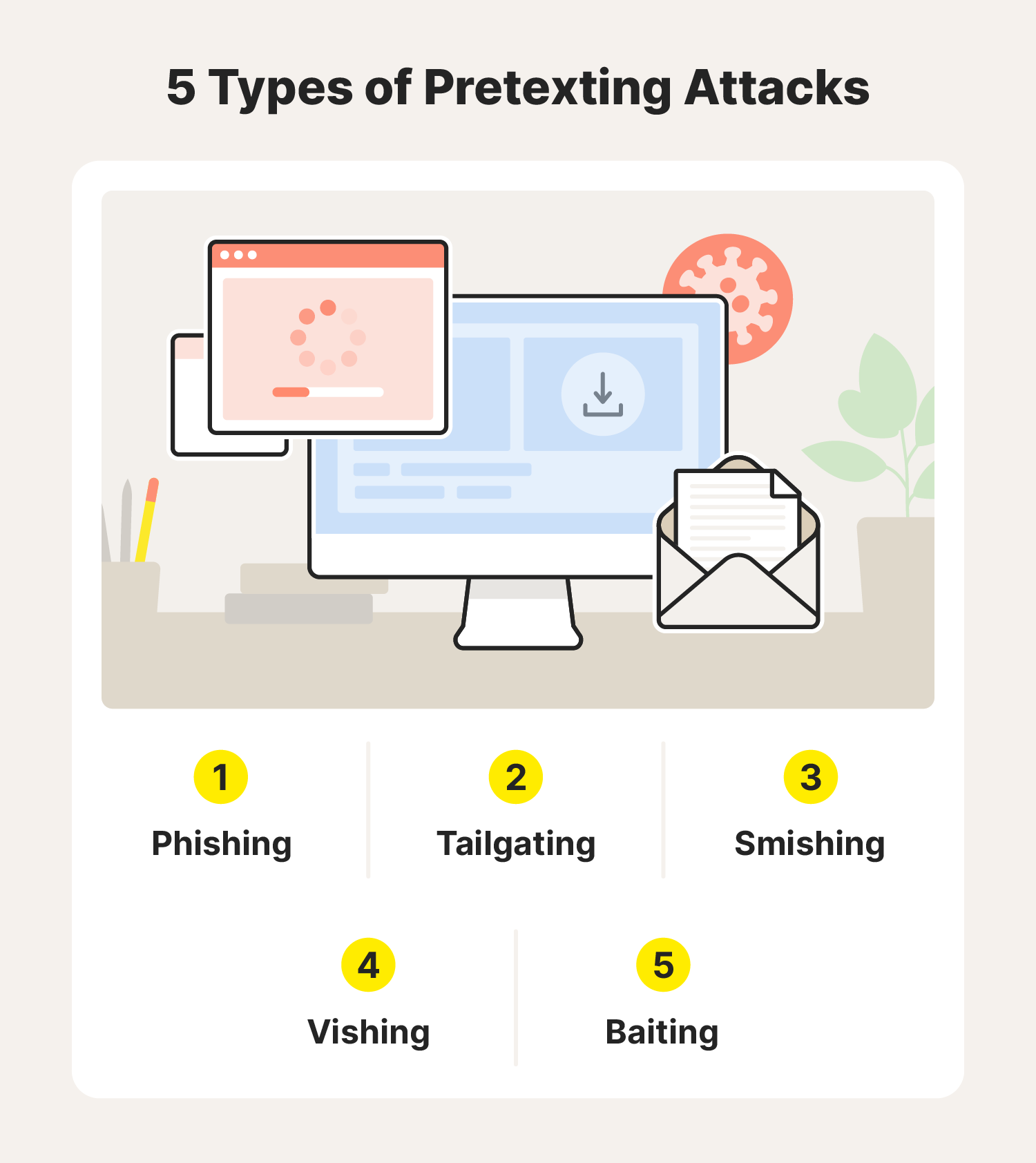
At its core, pretexting relies on storytelling, complex scheming, and manipulation. However, the underlying tactics can manifest in a few types of attacks.
Phishing
Phishing is pretexting via email and is often seen in Google Chat scams. It involves crafting a scenario that entices someone to click on a malicious link or file or hand over private information. Phishing also requires the scammer to pose as a trusted person or organization.
Tailgating
Tailgating is essentially hackers going phishing in the real world. Fraudsters assume a fake identity, such as a delivery person, prospective client, or employee, to gain physical access to information in restricted areas. Once they arrive on location, they will find the information they’re looking for by accessing computers, files, and anything else they can get their hands on.
Smishing
Smishing is like email phishing, but it occurs through SMS or text messaging. This channel is effective for pretexting because it allows hackers to connect with their target in an intimate, low-pressure way. Also, many people are inclined to trust someone texting them because it’s often difficult for strangers to find a personal phone number on their own.
Vishing
A combination of the words voice and phishing, or vishing, is just that—voice phishing. Vishing-based pretexting attacks happen over phone calls. To carry out these attacks, fraudsters may spoof or fake caller IDs or use deepfakes to convince their targets to trust them and disclose sensitive information.
Baiting
A baiting attack is pretty much what it sounds like—dangling something someone wants or cares about in front of them to manipulate them into doing what you want. Often, the bait comes in the form of a giveaway or free downloads. When a victim takes the bait (clicks on a malicious link or file), it will trigger an automatic download, installing malware on the target’s device that can allow the fraudster to access personal details.
13 common pretexting attacks and examples
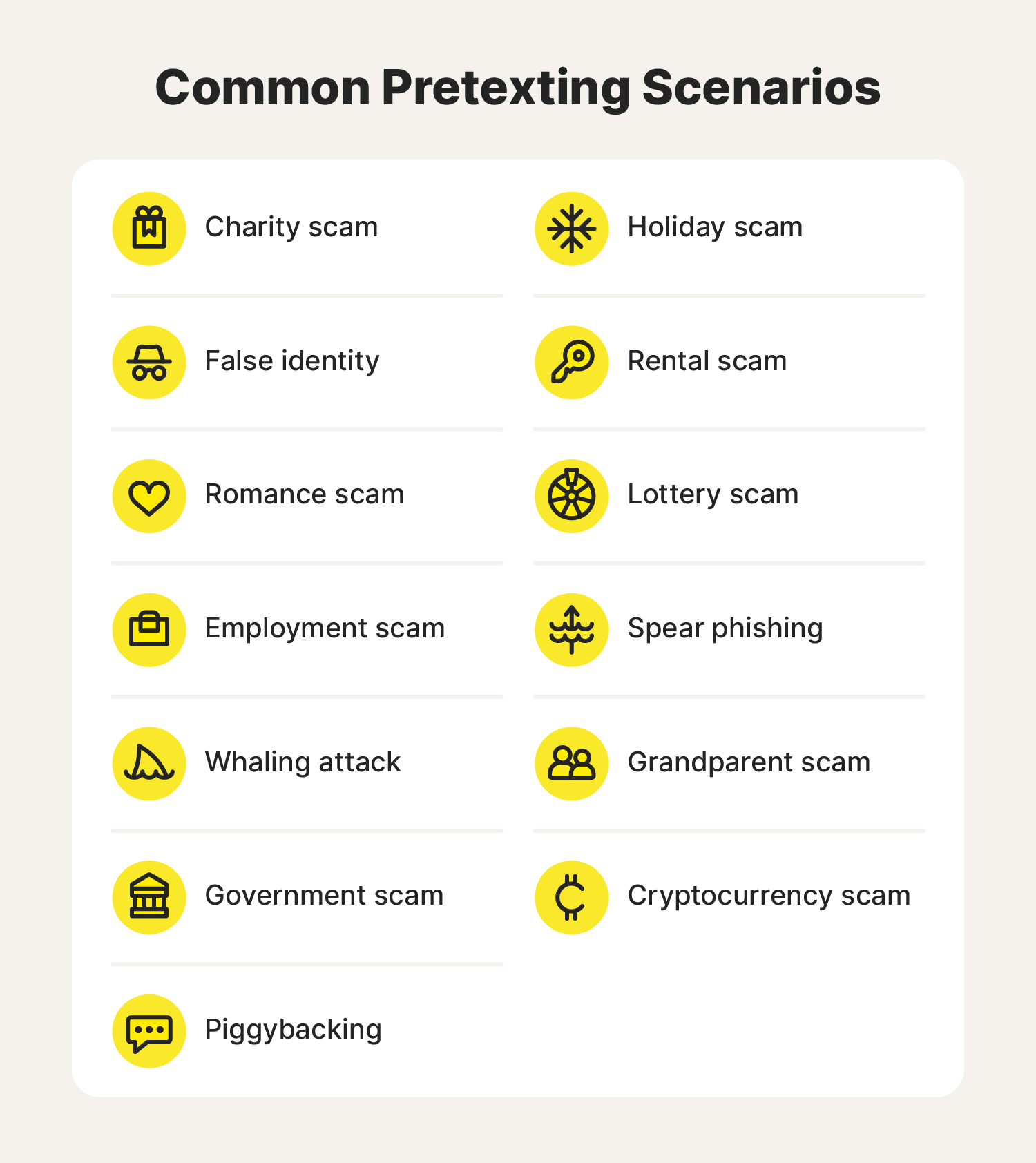
Here are some of the most common pretexting scenarios scammers leverage to trick unsuspecting people into disclosing private information:
- Charity scam: A scammer claims to be with a nonprofit organization collecting donations for a charitable cause and steals funds from well-intentioned donors.
- False identity: A fraudster develops a fictional persona or impersonates someone the target knows to manipulate them into disclosing sensitive information.
- Romance scam: A cybercriminal creates a fake online identity to catfish their unsuspecting target, form a romantic attachment, and convince them to send money or personal information.
- Employment scam: A scammer targets job seekers by pretending to be an employer or recruitment agency contact—convincing them to perform work for free or send personal details.
- Whaling attack: A scammer masquerades as an executive to manipulate “big fish,” aka high-ranking employees, into disclosing confidential information or completing large transactions.
- Government scams: A common type of “government” cyber scam is when a hacker pretends to be an IRS employee to scare taxpayers into paying money they don’t owe.
- Piggybacking: In cybersecurity, piggybacking usually happens through password sharing or when someone takes over an authenticated web session. Reusing passwords gives the attacker a clue on how to access other accounts, and not logging out allows them to search your computer for confidential information.
- Holiday scams: Several scams prey on people’s goodwill during the holiday season. Some of these include email phishing attacks, fraudulent online deals, church fundraisers, fake gift cards, and more virtual impersonators trying to get financial details.
- Rental scam: A fraudster poses as a property owner or manager and convinces someone searching for a home to send their SSN, bank account details, credit card number, or other identifying information.
- Prize and lottery scams: A scammer tells their target they won something but requires them to pay money or disclose private information to get it.
- Spear phishing: A cybercriminal poses as someone the target trusts and tricks them into opening a malicious email or revealing private details about themselves.
- Grandparent scam: A scammer tricks a grandparent into sending money and information by assuming the identity of one of their grandchildren and claiming to be in urgent need.
- Cryptocurrency scam: Schemers trick businesses and individuals into sending money by telling them that worthless or nonexistent cryptocurrency is an investment they can’t miss out on.
Best practices for preventing pretexting attacks
Discovering that you unwittingly fell prey to a social engineering attack like pretexting can be scary and tough to recover from—albeit not impossible. Still, it’s best to protect yourself from attacks altogether to avoid the hassle.
Here are several best practices to help prevent pretexting attacks:
- Learn to identify pretexting warning signs: Study the common strategies and scenarios we discussed earlier to catch pretexting attempts early.
- Enable user authentication: Keep hackers from accessing your accounts even if they have the password by requiring users to prove their identity via multifactor authentication (MFA) or two-factor authentication (2FA).
- Vet friend and access requests: Don’t accept message requests from people you don’t know, and block anyone who asks suspiciously invasive questions.
- Don’t post answers to common security questions online: Refrain from participating in posts that sneakily ask you to share information often used for security questions, like your mother’s maiden name or the street you grew up on. Also, avoid disclosing sensitive information, such as your address, when you post updates. Hackers can use all of this information to try to take over your accounts or manipulate you later.
- Don’t provide private information over the phone or email: Never share personal information like your SSN and account numbers over the phone. Most reputable companies will not ask you to do this.
- Create strong passwords: Poor password security makes it easier for hackers to break into several accounts once they gain access to one, so avoid using the same simple passwords on multiple accounts. Instead, opt for long, unique passwords that use a variety of letters, numbers, and symbols.
- Don’t leave your devices unattended: Through tailgating, a cybercriminal can physically alter your device or steal confidential information, so it’s best to keep your technology with you.
- Use software that monitors your device for malicious activity: Use a reputable antimalware scanner to receive alerts about suspicious activity and remove threats from your computer.
- Try a scam detector: You can also try using an AI-powered assistant like Norton Genie to help identify suspicious emails, messages, and links before you open them.
Safeguard your personal information
Fraudsters have a way of weaving convincing stories, even deceiving people who know to look for red flags. With that in mind, you might consider fortifying your device against viruses, hackers, and other cyber threats with help from antivirus software like Norton 360 with LifeLock Select.
FAQs about pretexting
There are an untold number of pretexting schemes hackers can use to manipulate people. Learn more about the nuances of pretexting and what to do if you suspect someone is targeting you.
What is the difference between pretexting and phishing?
Pretexting requires a hacker to create a fabricated scenario or persona to gain the user’s trust and convince them to divulge personal details.
There are phishing-based pretexting schemes. However, phishing usually employs deceptive, fraudulent communications like emails and texts to trick users into clicking on a malicious link or voluntarily sharing sensitive information.
What is pretext calling?
Pretext calling in cybersecurity occurs when a scammer calls their target using a false identity and spins a story, convincing them to send money or disclose information.
How do attackers find information to use in pretexting attacks?
Hackers often find the information needed to wage a pretexting attack by researching potential targets online. However, they sometimes resort to in-person stalking as well. Here are a few examples of what an attacker may do to learn private details.
- Snoop through social media
- Read news articles and announcements
- Access public records
- Browse company websites
- Trick targets into disclosing private information
- Dumpster dive
What should I do if I suspect someone is using social engineering to steal my private information?
If you suspect someone is using a social engineering tactic like pretexting to access your personal information, follow these steps:
- Don’t share personal details: Keep sensitive information like your SSN, passwords, or credit card numbers private until.
- Vet them: Check their credentials, verify that their company website is legitimate, and educate yourself on what information is essential for them to conduct the task they are carrying out.
- Report your suspicions: If you suspect an issue, secure your accounts, document all interactions and details about the harm they caused, and give it to your local law enforcement agency.
What happens if I fall for a pretexting attempt?
If you fall for a pretexting attack, the hacker can use the information they obtain to steal your identity or access more privileged information.
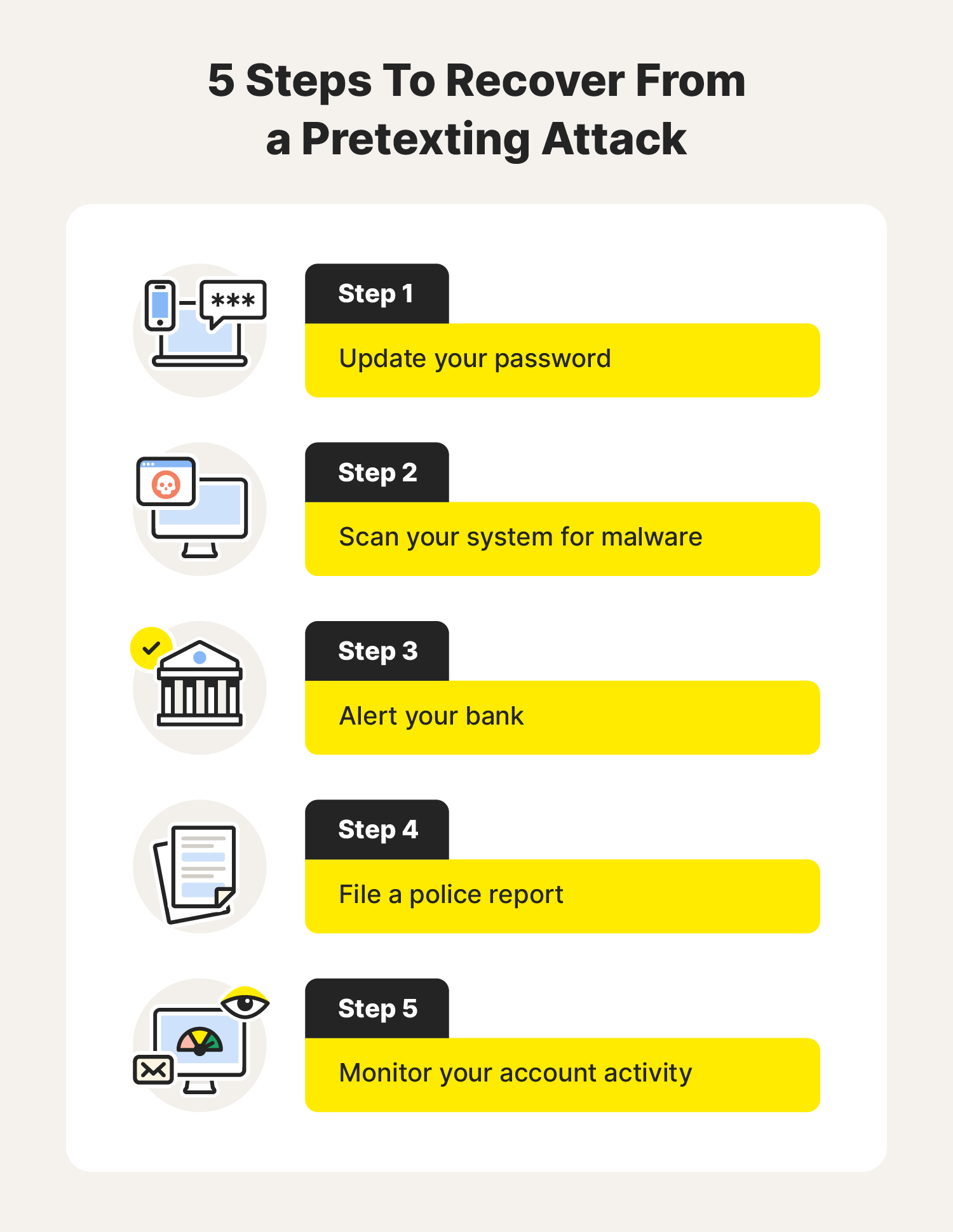
To prevent further repercussions, follow these steps:
- Change your passwords immediately.
- Run a malware scan or take the compromised device in to be assessed by an expert.
- Alert your bank to unauthorized access and transactions.
- Report the attack to the police or your business’s IT team.
- Monitor your credit score and look out for new accounts.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.







Want more?
Follow us for all the latest news, tips, and updates.