Password spraying: Prevention and detection tips
Remembering complex passwords can be a headache and you may be tempted to make them easier. But simple passwords make it easier for password-spraying cybercriminals to hack your accounts. Learn how password spraying attacks work and how to detect them. Then, get Norton 360 Deluxe with its built-in password manager to help secure your passwords and protect your accounts.

What is password spraying?
Password spraying is a type of brute force attack where cybercriminals take common passwords and “spray” them across several accounts in hopes of gaining access. This type of password attack is popular among hackers because it helps them get around hold-ups that come with repeatedly guessing a single account’s password, such as login attempt limits and account lockouts.
How do password spraying attacks work?
Password sprayers work by collecting lots of usernames and a list of commonly used passcodes. Next, they set up automations to rapidly test common password variations across multiple accounts in hopes of accessing as many as possible. If they’re successful, they get access to the hacked account.
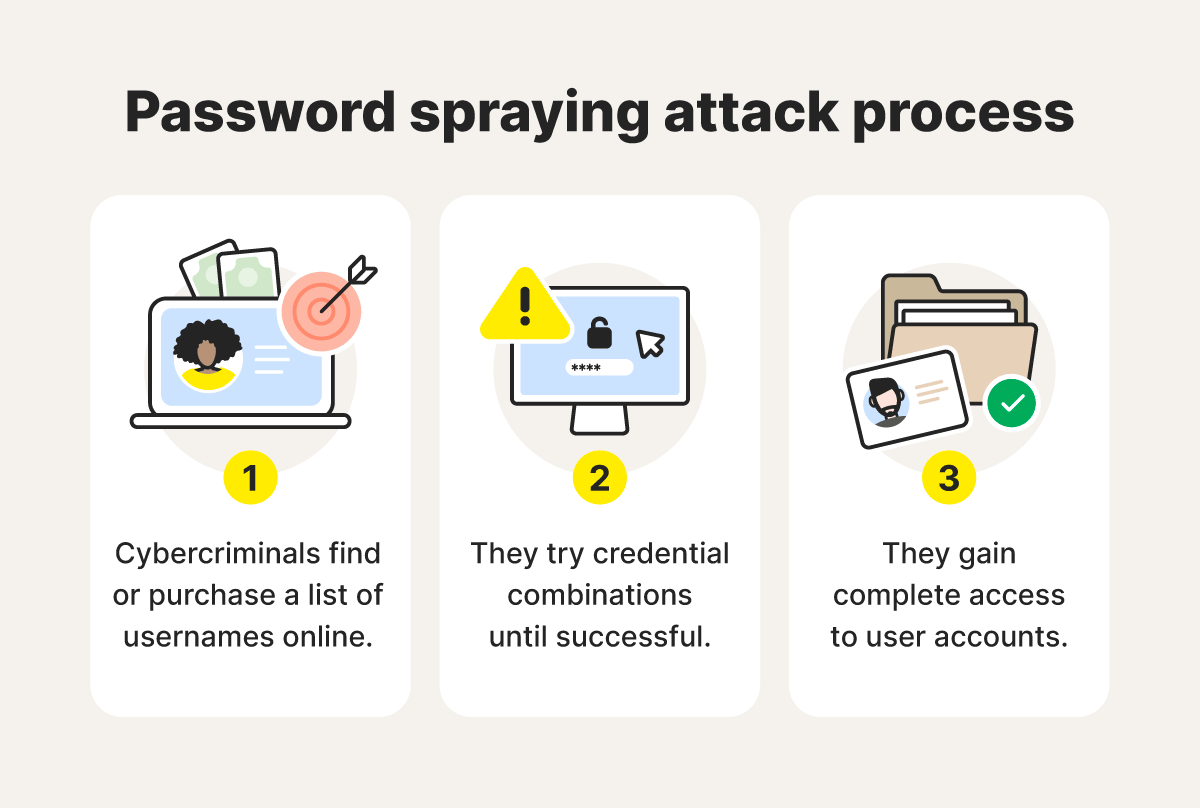

Here’s a closer look at how password spraying attacks work:
- Cybercriminals find or purchase a list of usernames online: Hackers often purchase credentials on the dark web to use for password spraying attacks. Some might also find company email address patterns and employee names on LinkedIn to hack the usernames of a given company.
- They try different credential combinations until successful: At this point, the act of password spraying begins by trying different combinations of usernames and passwords, often through an automated system. Cybercriminals typically repeat this process using one password per account at any one time to avoid account lockouts.
- They gain access to user accounts: Once the hackers uncover a user's password, they’ll have access to that user's personal information, which can lead to identity theft or account takeovers.
25 passwords that won’t hold up in a password spraying attack
Passcodes with predictable sequences like “123,” single words like “password,” and simple combinations like “Aa1234” are usually the first to be cracked in password spraying attacks. Here are 25 examples of passwords cybercriminals are likely to hack in one second or less:
1. 000000
2. 111111
3. 1234
4. 12345
5. 123456
6. 12345678
7. 123456789
8. 1234567890
9. 654321
10. 1q2w3e
11. Aa1234
12. abc123
13. admin1
14. admin123
15. demo
16. welcome
17. minecraft
18. Password
19. Password1
20. p@ssw0rd
21. P@55w0rd
22. Q2w3e4
23. qwerty
24. student
25. test
Not using passwords like the ones listed above may seem obvious, but not all passwords with special characters are created equally. Install Norton 360 Deluxe, which includes a built-in password manager, so you can generate, store, and retrieve your unique passwords in a few simple clicks. Norton 360 Deluxe also defends against a myriad of malicious online threats to help keep your device, your data, and your passwords safer.
How to detect password spraying attacks
If you start noticing unexpected account changes, strange new settings, or fishy activity, it could be a sign you’ve fallen prey to a password spraying attack.
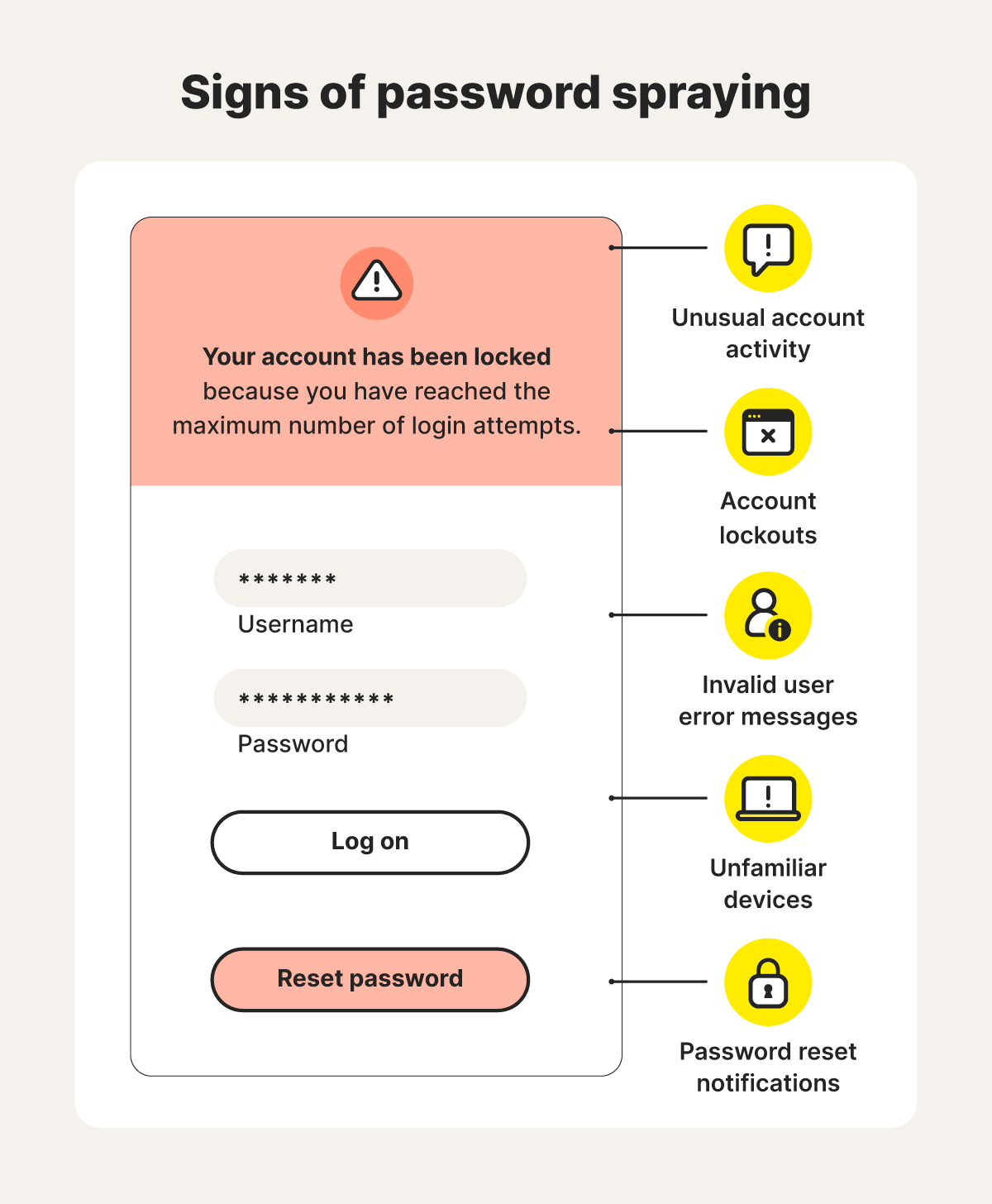
Here are some telltale signs of a password spraying attack:
- You’re locked out: If you can’t log in or you exceed your number of login attempts too quickly, it may be because a password spraying attack targeted your account just before you got there.
- Your account can’t be found: If you’re trying to sign in and you get an “invalid user“ error message, it might be the particular site’s way of locking your account due to multiple unsuccessful login attempts in response to a password spraying attack. Or, it could mean that the attack was successful and your account was deleted or removed.
- You receive a password reset email: If you’re not actively trying to sign in but you receive a rogue password reset email or text message, it could be a password spraying attack. Set up two-factor authentication (2FA) on all your accounts to require an extra layer of authentication to gain access.
- You’re signed in on an unknown device: If you gain access and see there’s an unfamiliar device listed in your login history, remove it immediately and change your password. Strange devices or devices in locations you’ve never been to are a big red flag.
- You notice strange account activity: If you notice strange posts, likes, comments, messages, or other activity originating from your account, it’s possible someone gained access through a password spraying attack. You may also notice changes in settings, new connections, and unauthorized purchases.

How to recover from password spraying attacks
If any of the warning signs above ring true for you, change your password immediately and set up multi-factor authentication to help protect you against future attacks. Here are some actions to help you recover after a suspected password spraying attack:
- Change your passwords immediately: Create a more secure password that’s at least 15 characters long—passphrases are good choices. Also, be sure to update any other accounts that use the exposed password.
- Log out on all devices: After choosing a new password for the affected account, log out on all devices. That will boot lingering password sprayers out of your account.
- Consult your organization’s cybersecurity department: If the attack occurs at work, let your organization’s cybersecurity or IT department know so they can find and patch any security vulnerabilities and start blocking known attack vectors.
- Turn your recovery into prevention: Consider taking preventive measures and choosing good antivirus software for better overall device security against many types of online threats and malicious attacks.
How to defend against password spraying attacks
Whether you want to batten down the hatches after a password spraying attack or set up a more proactive defense, Norton 360 Deluxe can help keep your passwords more secure with a built-in password manager. Plus, you’ll get multiple layers of defense against hacking, malware, scams, and other online attacks.
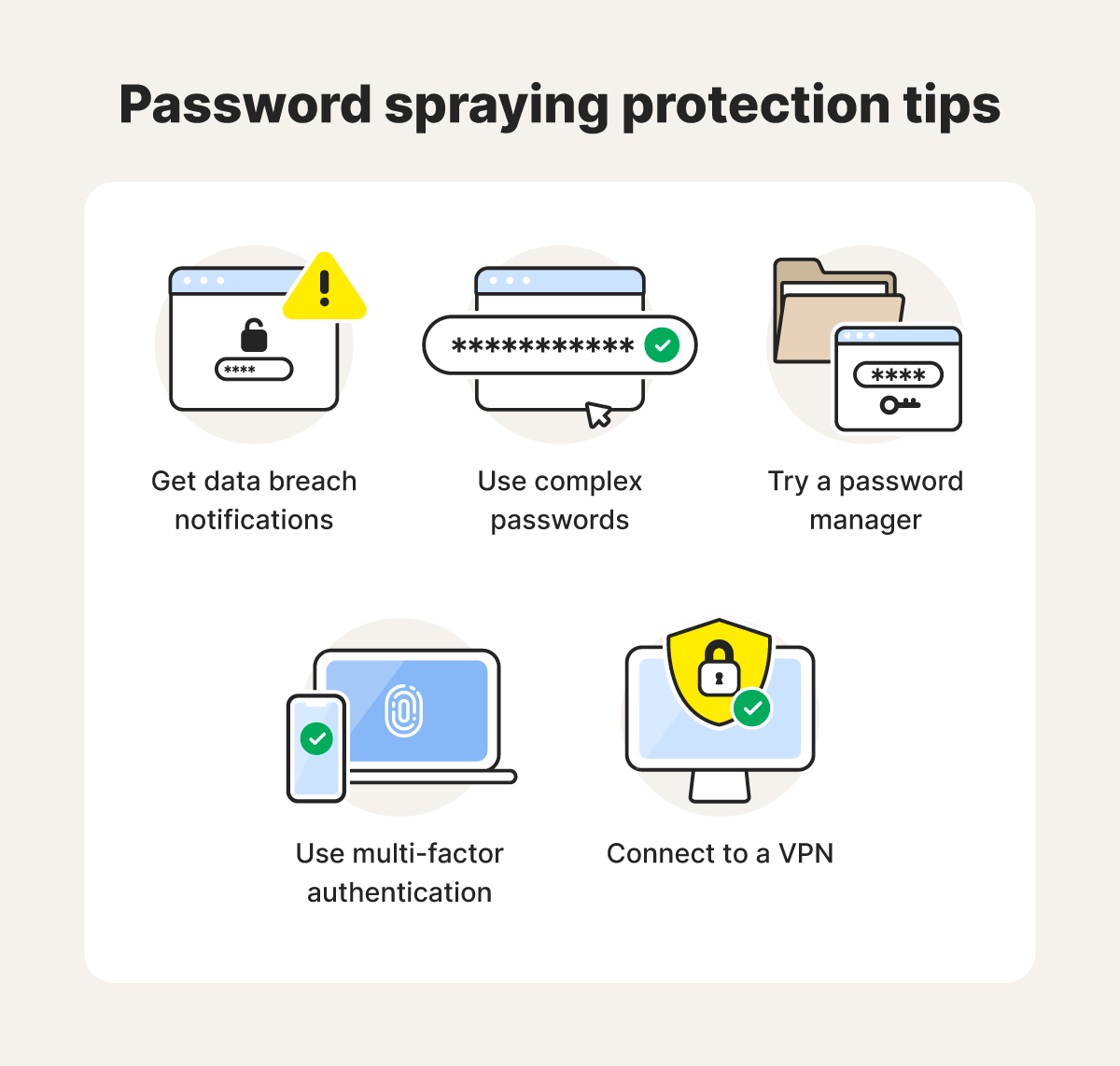
Once you have a powerful cybersecurity tool at your defense, it’s also important to shore up your protection against password spraying attacks in other ways. Here’s a closer look at the most effective ways to defend against password spraying:
Check for breached data
With a data breach detection tool, you can check your email address to see if it’s been compromised. It also shows you other data involved in data breaches to give you a heads-up when someone exposes your personal information, including potentially leaked passwords. With that knowledge, you can change your passwords and take additional security measures to help keep hackers out of your accounts.
Use complex passwords
Long, randomly generated passwords are much harder for hackers and password sprayers to crack. In fact, the National Institute of Standard and Technology (NIST) recently issued a new version of the Digital Identity Guidelines. In it, they suggest that the traditional composition rule of requiring letters, numbers, and special characters is no longer necessary.
Instead, the NIST recommends randomly generated, 15-character (minimum) passwords—emphasizing randomness over character types. And don’t forget that every password you use should be unique to one account.
Generate random, complex passwords with Norton Password Generator—a free online tool that can help you create unique passwords for all your online accounts.
Try a password manager
A secure password manager—like the one built into Norton 360 Deluxe—can both generate ultra-complex passwords and safely store them all in one place until you need them. All you need to do is remember one password to access them all and you’ll be able to use them across your synced devices.
Use two-factor authentication
When your login page asks for a one-time password sent to your email or phone number, this is called two-factor authentication (2FA). Enabling this feature across accounts adds an extra layer of security to your logins. Some accounts let you choose the extra authentication type, like a one-time code, biometric scan, or verification via an authenticator app.
Connect to a VPN before using public Wi-Fi
A VPN encrypts your internet traffic, making it difficult for others on unsecured networks to intercept and read your data, including your account passwords. This extra layer of protection can significantly reduce your risk of falling victim to password spraying attacks when using public Wi-Fi networks.

Password protection and threat detection
Get Norton 360 Deluxe to help keep your passwords—and your accounts—safer. Plus, you’ll get access to the password manager, which helps securely store your account login credentials, and a built-in VPN to keep the data you send and receive online more private. Protect against password spraying attacks, scams, hacking, and other online threats with Norton today.
FAQs about password spraying
Still have questions about password spraying? Here’s what you need to know.
What’s the difference between password spraying and a dictionary attack?
Password spraying targets multiple accounts with the same common password. The attacker will usually space out attempts if the first password doesn’t let them in. Dictionary attacks, by contrast, use a list of many possible passwords against a single account. Both password spraying and dictionary attacks are examples of brute-force attacks.
What is the difference between password spraying and credential stuffing?
Credential stuffing and password spraying are similar in that they both use usernames found online. However, in credential stuffing an attacker also has the password for a user’s account. They then try these login credentials on other accounts, hoping the user has reused the same username and password on multiple accounts.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.







Want more?
Follow us for all the latest news, tips, and updates.