What is smishing? How to spot and avoid an attack
You’ve probably heard of phishing, but what is smishing? Learn how scammers use text messages to spread malware and steal data, different types of smishing scams to look out for, and how to recognize the warning signs of a smishing attack. Then get Norton 360 Deluxe to help block scams and prevent threats.

Cell phones and mobile devices make connecting with friends and family easy—but they can also make you available for malicious interactions with scammers.
What is smishing?
Smishing is a type of phishing cybersecurity attack that uses deceptive text messages to trick recipients into providing personal information or clicking malicious links.
It’s called “smishing” because it combines the terms “phishing” and SMS (Short Messaging Service). Phishing is traditionally a social engineering attack over email, but smishing takes place over text messaging channels.
What the experts say
"A text message can point to a look-alike login, which then routes a victim to a live chat or voice follow-up." - Gen 2025 Threat Report
Threat Research Team, Gen
Scammers use smishing to perpetrate identity theft and fraud or even to spread different types of malware. Shielding yourself against smishing attacks involves staying vigilant, understanding the signs of suspicious phishing text messages, and learning to protect your mobile security.
Smishing vs. phishing vs. vishing
Phishing, smishing, and vishing are all tactics for stealing personal information—the difference lies in the form of their delivery.

Vishing and smishing are types of phishing.
Phishing is a social engineering tactic used by scammers and cybercriminals. It’s often carried out via fake emails pretending to be from trusted sources. Phishing attacks accounted for 36% of all data breaches in the US in 2023.
Smishing, or SMS phishing, involves sending scammy, fraudulent, or malicious text messages hoping to get someone to reply or click a link.
Vishing, or voice phishing, is when scammers impersonate professionals or other trusted sources over the phone to trick victims into revealing sensitive data or transferring money or digital currency.
Channel |
Content |
Example |
|
|---|---|---|---|
Smishing |
SMS or text messages |
Requests for info or malicious links |
A text with a link to confirm a supposed delivery |
Phishing |
Requests for info or malicious links |
An email from your bank with a link to reset your password |
|
Vishing |
Phone calls, automated recordings, or voicemails |
Threats or requests for info, support, or money |
A caller poses as the IRS threatening legal action unless you pay unpaid taxes |
How does smishing work?
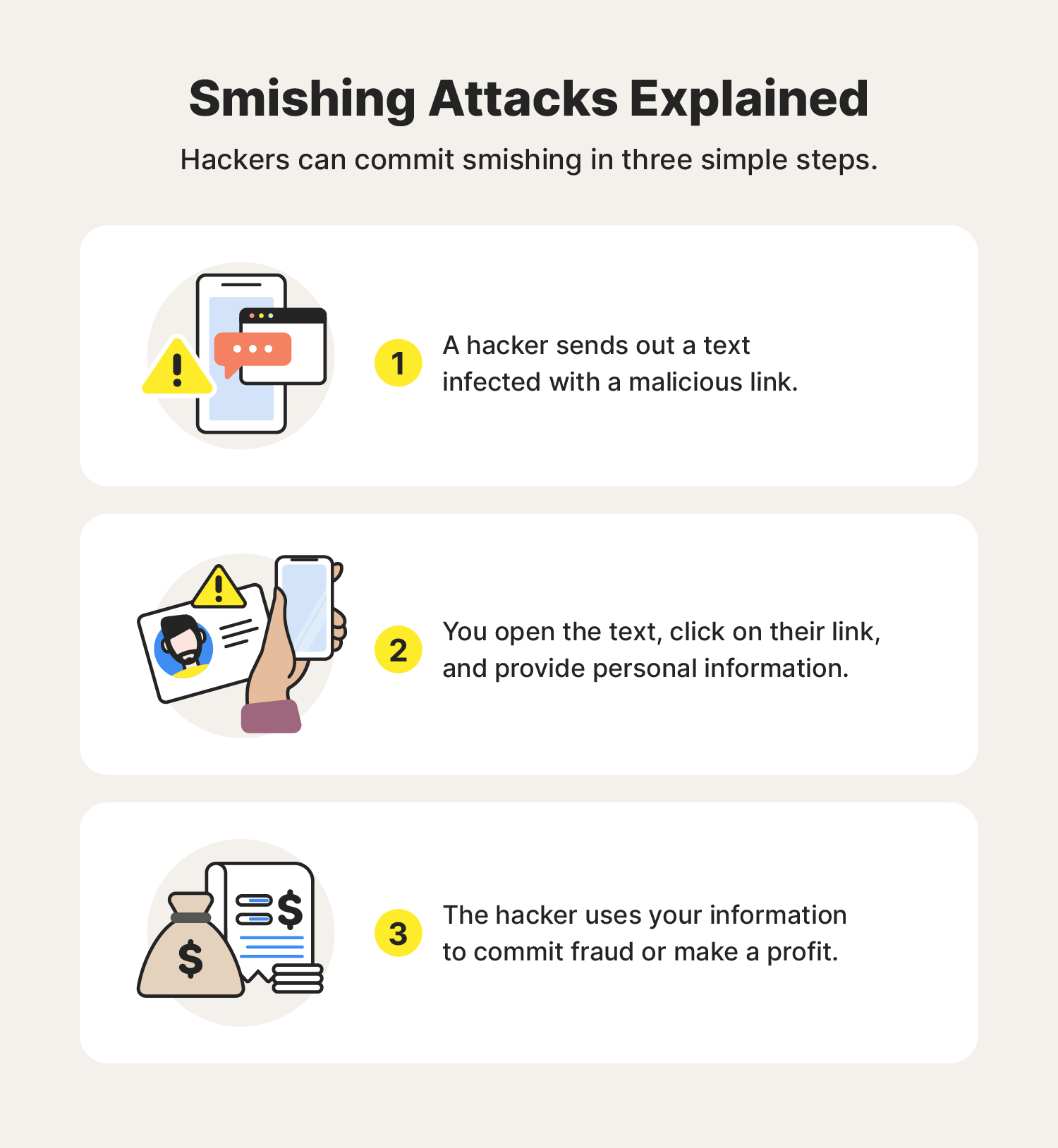
Cybercriminals use a combination of malware, malicious links, text threats, and social engineering tactics (like fear-inducing language and manipulation) to carry out smishing attacks. Here are the usual steps of a smishing attack:
- A scammer sends a text message using social engineering tactics to trick you into believing the message is legitimate.
- You click an infected link or provide personal information.
- The scammer uses your information to carry out further attacks, commit fraud, or even sell the stolen data on the dark web.

5 types of smishing attacks
Smishing text messages can come in many forms because hackers like to customize their messages to fit their targets. Keep these different kinds of smishing texts on your radar to help ensure the Cyber Safety of your smartphones and tablets.
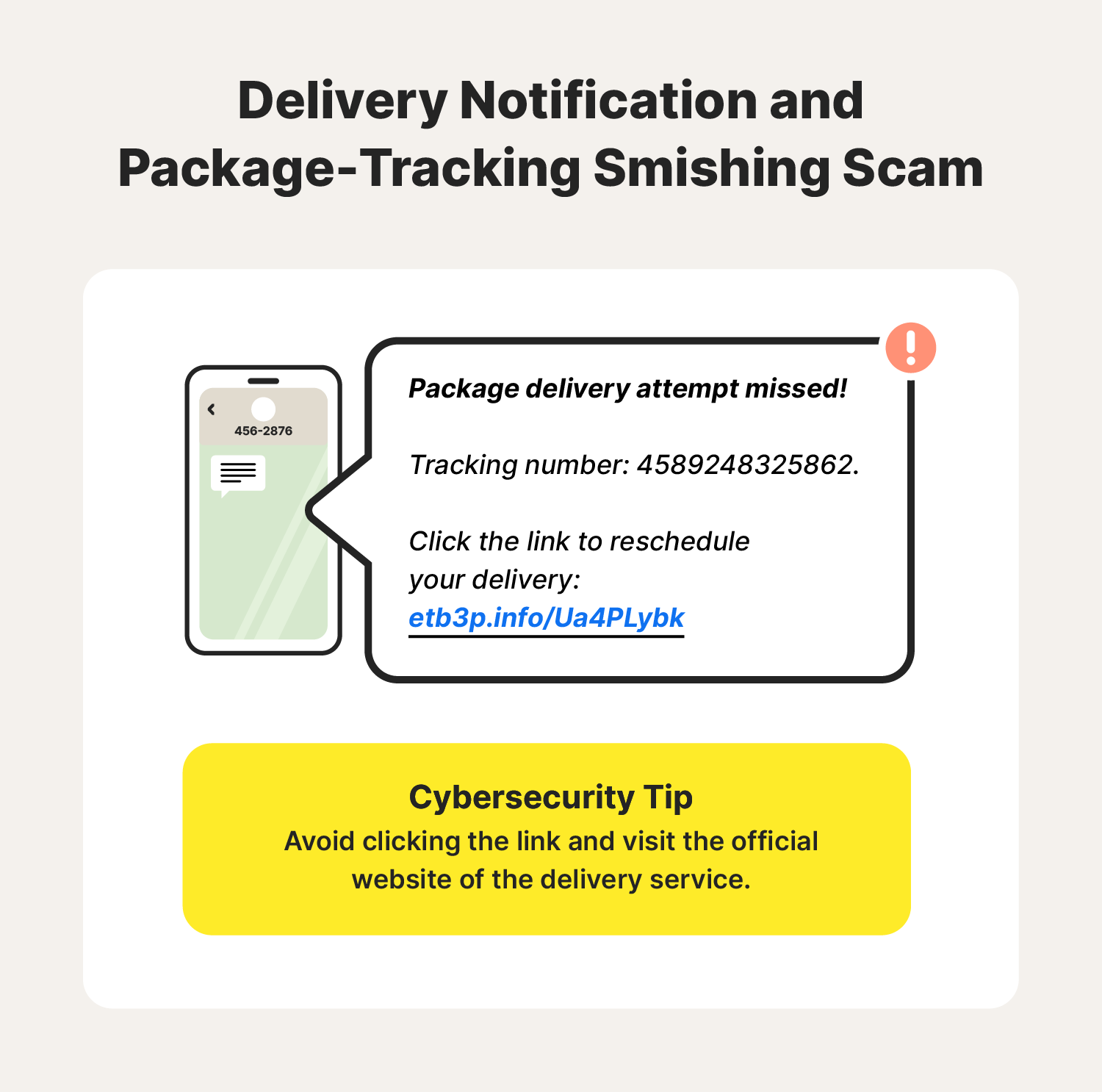
1. Delivery notification and package-tracking smishing
Package delivery scams are among the most common types of smishing attacks, especially during holidays or major sales events. You might receive a FedEx, UPS, or USPS scam text notifying you about a delivery snag or requesting an update on shipping details. TThis scam aims to trick you into clicking a text phishing link or divulging personal information.

2. Financial services smishing scams
Financial services smishing scams take advantage of the fact that almost everyone uses banks and credit card companies to manage their finances. These smishing messages pose as legitimate banking institutions to get you to volunteer sensitive data like your Social Security number, address, phone number, password, email, and more. Smishers often send fraud alerts, warning targets about suspicious activity on their account, prompting them to click a link or call a phone number, both of which are malicious.
Some IRS-related scams to watch out for are messages promising tax credits or help with setting up an online IRS account. The IRS has reported an increase in smishing attacks, so keep that in mind if you receive a text message supposedly from the IRS. And remember that the IRS will never text you.


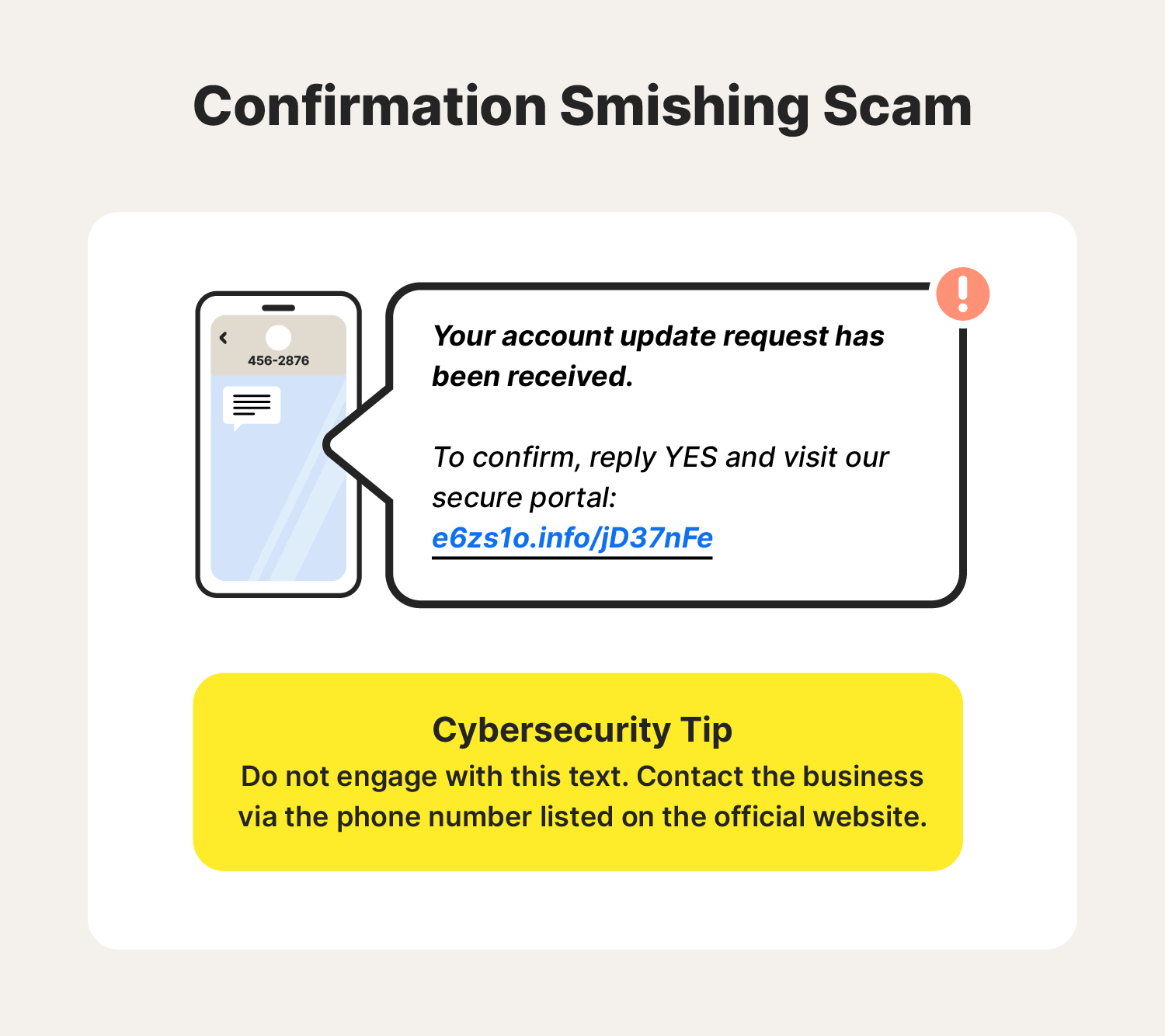
3. Confirmation smishing scams
A confirmation smishing scam uses fake confirmation requests to get you to expose sensitive information. This could be for an online order, an upcoming appointment, or an invoice for business owners. The smishing text may contain a link directing you to a site that asks you to input login credentials or other sensitive data to verify your appointment or purchase.

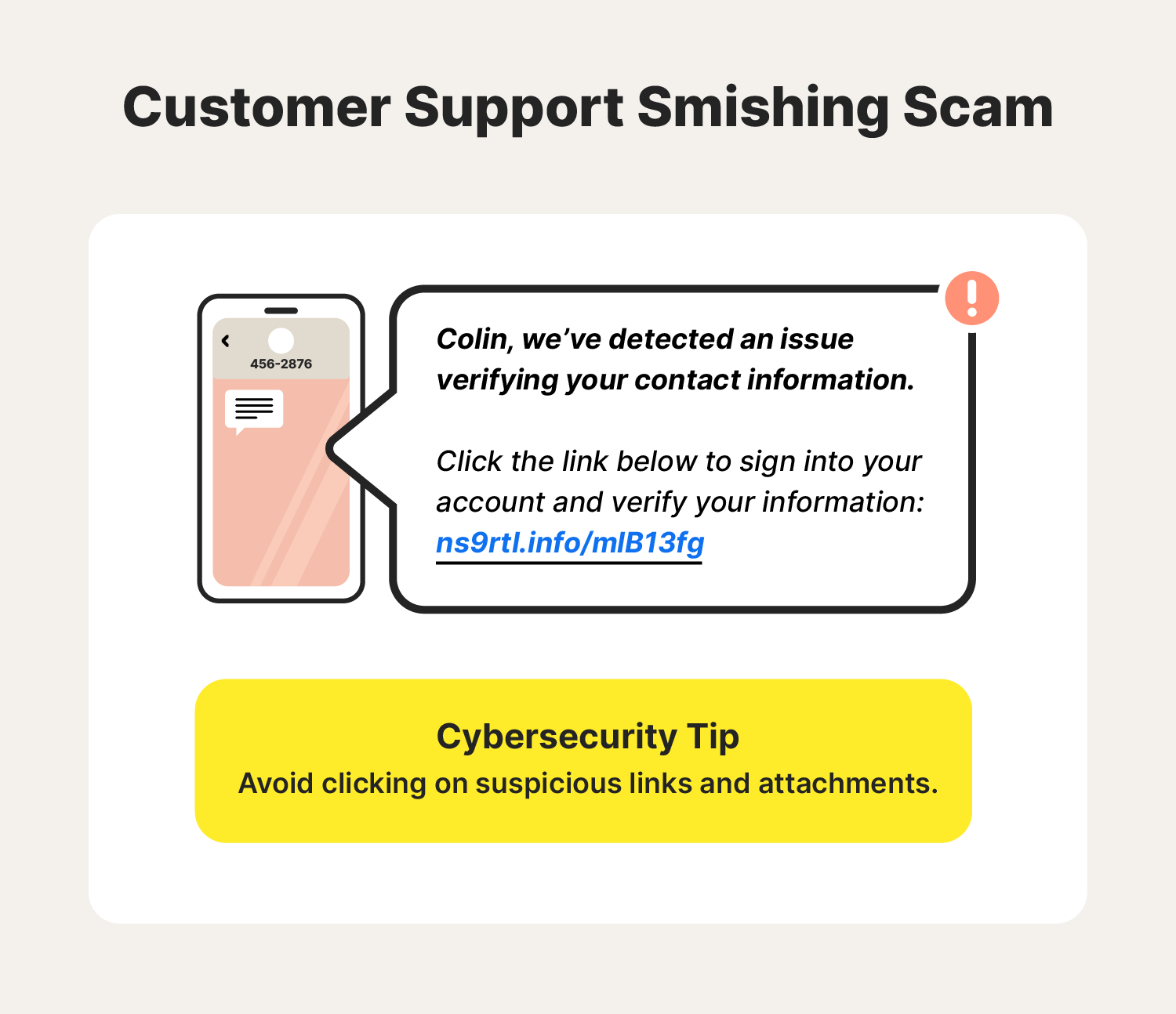
4. Customer support smishing scams
Customer support smishing scams send smishing texts posing as any company a person may trust—not just banks or credit card companies. They may pose as a representative from an online business or a retailer notifying you of an issue with your account. They’ll provide instructions to solve the issue, which may include directing you to a fake site infected with spyware.

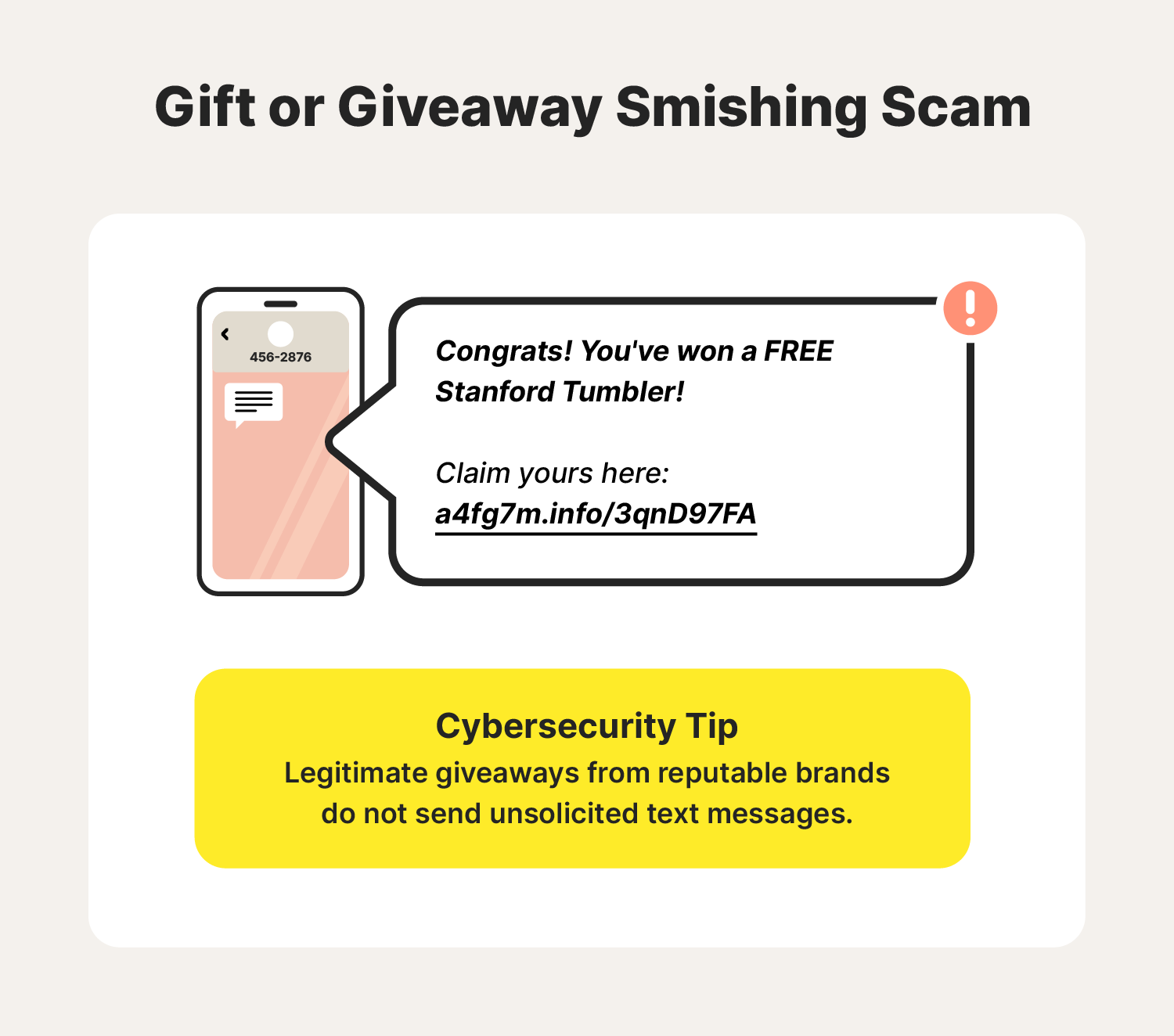
5. Gift or giveaway smishing scams
This type of smishing attack offers you a free gift or advertises a fake contest giveaway, trying to get you to click a malicious link to claim your prize. If you tap the link and end up on a website, your “gift” may be your own device infected with malware.

Smishing attack examples
Learning about real-life smishing examples can help you understand how to avoid them in your everyday life.
- UPS Canada (2023): UPS experienced a data breach where unauthorized access to their package lookup tool exposed some recipients’ details. UPS warned customers that attackers had targeted some recipients with smishing attacks demanding payment before delivery.
- Verizon (2022): Verizon acknowledged a smishing campaign targeting its users. The smishing text appeared to come from a user's own phone number in hopes of them clicking the malicious link attached to the message.
- Tokyo Olympics (2020): Threat intelligence firm CYFIRMA detected a smishing campaign targeting Olympics fans by attempting to sell fake event tickets to steal personal data and banking information.
- United States Postal Service (2020): The CEO of SlickRockWeb reported a smishing campaign posing as the USPS to trick users into compromising login credentials.
- State of Texas (2020): A delivery notification smishing attack masquerading as DHL, UPS, FedEx, and Amazon became so widespread that Attorney General Ken Paxton sent a press release to warn Texas residents.
- E-ZPass: Attackers sent texts claiming recipients owed a toll balance to trick them into clicking on phishing links and sending small amounts of money.
To help protect yourself against a smishing attempt, learn the warning signs and smishing protection tips.
Smishing attack warning signs
Use these smishing attack warning signs to help determine if you’re dealing with smishing spam texts on your mobile device:
- Suspicious phone numbers: Smishing messages often come from numbers that don’t follow the typical 10-digit layout or use a series of the same number.
- Misspelled words or grammatical errors: Reputable businesses ensure their communications are free of typos and grammatical errors before sending them to customers. These careless mistakes are red flags and often signs of a scam.
- Links and files from unknown numbers: Phishing through text messages often includes deceptive links with unusual URLs that take you to an unsafe website.
- Urgent requests: Scammers frequently employ urgency to frighten their victims. However, genuine companies give ample notice about issues, so delete these messages or verify them with the supposed sender through an official channel.
- Money requests: Messages urging online money transfers are likely scams aiming to drain your funds.
- Prize notifications: Receiving prize alerts for contests you didn't enter is a red flag; steer clear of engaging or clicking any embedded links.
How to avoid smishing scams
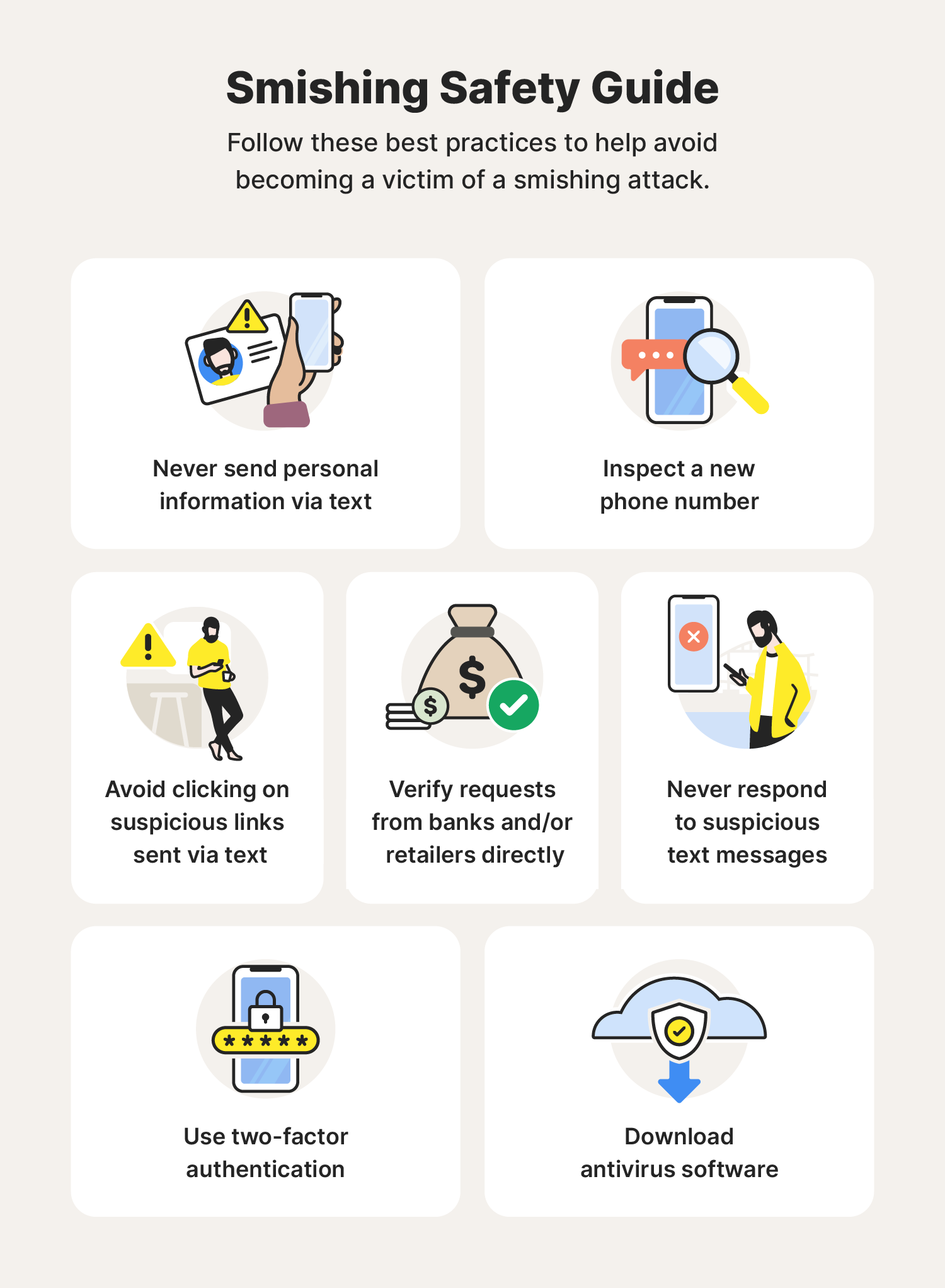

Your cell phone is likely one of your most used and trusted devices. Avoid potential smishing scams with the help of these cybersecurity tips:
- Do not send personal information via text: Never give out personal details, such as passwords, credit card numbers, addresses, or emails via text.
- Inspect new phone numbers: Odd phone numbers may indicate a smishing attempt. Be careful of international numbers or those that don't follow the typical format.
- Avoid clicking suspicious links or files: The core of a smishing attack is often a malicious link. Avoid clicking these links at all costs. Also, if you can tell a text is fake when you receive it, delete it immediately.
- Contact the business directly: Scammers commonly impersonate valid businesses or banks. If a text seems questionable, contact the institution directly to verify it.
- Never respond: One of the best ways to avoid future smishing attempts is to not engage. Replying to a smishing text confirms that your number is active and may lead to further attacks.
- Use two-factor authentication: Even if you get tricked and your password gets compromised, two-factor authentication adds an extra protective layer. For example, biometric technology uses a fingerprint or facial recognition to verify your identity.
- Download antivirus software: Downloading trusted antivirus software like Norton 360 Deluxe can help keep your device secure by protecting against hacking and blocking malware and other online threats before they infect your device.
How to respond to smishing
If you receive a suspicious text message that has tell-tale signs of smishing and phishing, don’t panic. Learn these best practices so that you know how to respond to smishing attempts:
- Don’t respond: Never reply to a suspected smishing text.
- Report the attack: Mark the text as spam, report the number, and notify your mobile service provider. There are also official channels to report these scams, like the Federal Trade Commission.
- Update your passwords: Change the passwords of any accounts you think might be at risk. Use long and unique passwords or passphrases to enhance password security.
- Monitor your finances: Check your bank statements and credit card activity. If you notice anything suspicious, alert your bank immediately.
- Scan your device for malware: Use trusted antivirus software to run a thorough malware scan on your device. If you’ve clicked any links, there could be threats lurking.
Help protect against online scams with Norton 360 Deluxe
As with other social engineering tactics, smishing exploits human error—that’s why staying informed is key. And using strong security software like Norton 360 Deluxe can help protect you from malware, hacking, and other online threats. Download Norton 360 Deluxe today to help keep your phone safer online.
Smishing FAQs
Check out these frequently asked questions about smishing to properly handle the situation if you encounter a malicious text message.
What is smishing short for?
Smishing is a combination of “SMS” (short message services) and “phishing.”
What is smishing in social engineering?
In the context of social engineering, smishing involves attackers using psychological tactics through deceptive text messages designed to trick recipients into taking particular actions—like clicking malicious links or providing personal data or financial information.
Can I get a virus from opening a text?
Opening a text message is generally safe, but actions that may follow, like clicking a malicious link or downloading a malicious attachment, can introduce a virus or malware to your device.
What is the difference between phishing and smishing?
Smishing is a type of phishing. Phishing often refers to deceptive email scams, while smishing only uses text messages.
Is smishing a cybercrime?
Yes, smishing is a cybercrime that uses malicious text messages to commit fraud or steal personal information to benefit the cybercriminal.
Why do cybercriminals use smishing?
Cybercriminals use smishing because text messages are instantly accessible and illicit quick replies, making it a highly successful medium for scammers. The purpose is usually to steal a victim’s personal data or have them click a malicious link.
What do you do when a strange number texts you?
If you receive a text from an unknown number, especially if the content seems odd or too good to be true, don’t click any links, do not respond, consider reporting the number as spam, and think about blocking the number.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.







Want more?
Follow us for all the latest news, tips, and updates.