What is a VPN tunnel and how does it work?
A VPN tunnel provides an encrypted channel for your internet data, helping to prevent hacking and eavesdropping. Keep reading to learn more about VPN tunnels and how they work. Then, get Norton VPN to access ultra-secure, flexible tunneling protocols to suit your needs.

A VPN tunnel is a secure, encrypted connection between your device and a remote server that helps protect the data you send and receive from interception.
“Full tunnels” encrypt all your internet traffic, whereas “split tunnels” let you choose to encrypt some data streams while keeping others open, which can be helpful while streaming. The level of protection provided by any VPN tunnel depends on the encryption protocols used and the security measures of the VPN service itself.
Read on to learn how VPN tunneling works, its main pros and cons, how split tunneling fits in, and the different types of VPN tunneling protocols you’ll encounter.
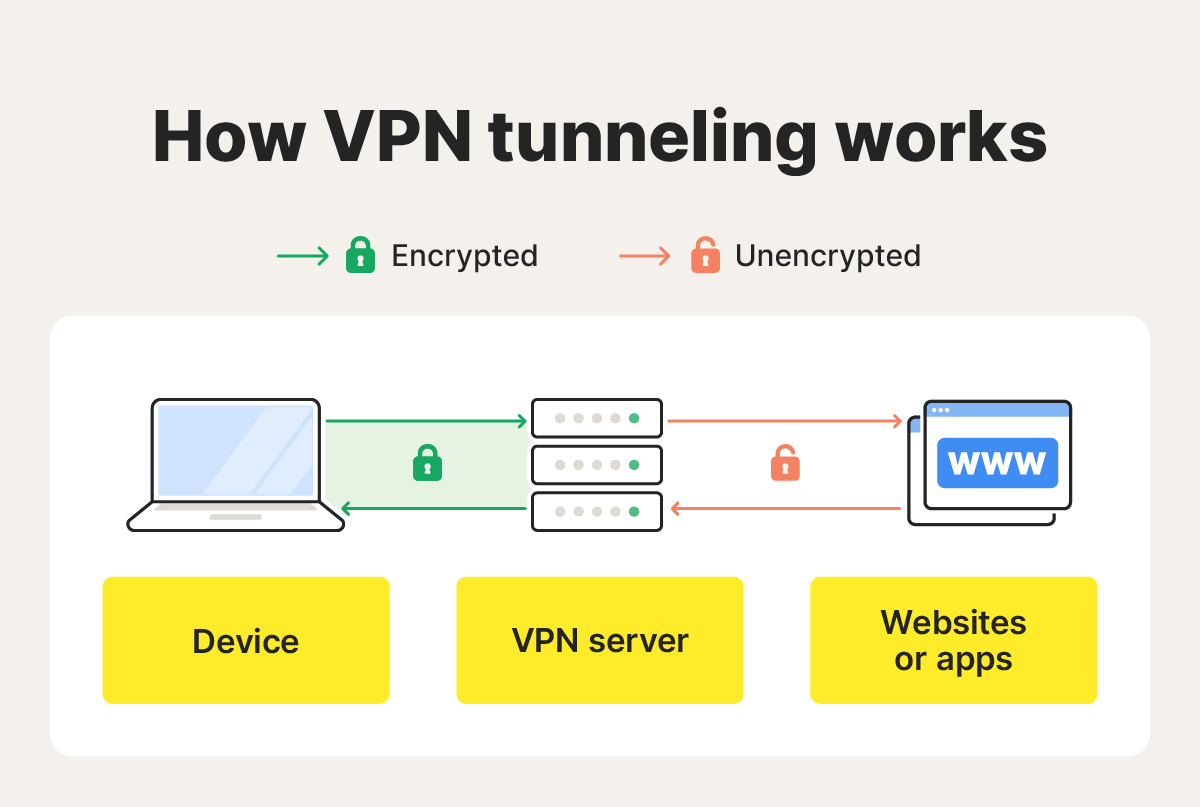
How does VPN tunneling work?
A VPN tunnel uses tunneling protocols to create a secure, encrypted connection between a device and a remote server. Internet traffic is then routed through this tunnel to protect data against packet sniffing or other forms of interception. This helps hide internet activity from hackers, snoops, and other third parties.
Here’s a closer look at how a VPN tunneling process works:
- You select a VPN protocol: Many VPNs come with a default protocol you can’t change. If you have multiple options, choose one based on your security and speed requirements.
- The VPN establishes an encrypted channel: Turn on your VPN to create a secure, encrypted connection to a VPN server. This obscures your real IP address behind the virtual IP assigned by the VPN server, making your session more private.
- Your data is encrypted: Now, you can privately shop, stream, game, message, and browse. All the traffic between your device and the internet will be encrypted and sent through the secure VPN tunnel.
- Your data is decrypted: The VPN server receives your encrypted data, decrypts (unscrambles) it, and then forwards it to the intended destination, such as a website or file-sharing service.
- The data is returned: The VPN server encrypts incoming data and sends it back through the secure tunnel to your device.

Full vs. split tunneling
The two basic types of VPN tunnels are full tunnels and split tunnels. A full tunnel encrypts all your internet traffic, while a split tunnel lets you choose which apps, sites, or IP addresses use the VPN and which bypass it.
Split tunneling is helpful when certain apps or services don’t work properly with a VPN. For example, some banks block logins from foreign VPN servers, so excluding your banking app from the tunnel keeps it accessible while still helping to secure the rest of your online activities.
A full tunnel, by contrast, is generally more secure because it routes every data stream on your device through the VPN. The trade-off is convenience — you’ll need to switch it off completely to reach sites that block VPN traffic if split tunneling isn’t available.
Full Tunnel |
Split Tunnel |
|---|---|
Routes all traffic |
Routes selected traffic |
Encrypts all data connections |
Encrypts select connections that you specify |
Slower speeds through the tunnel |
Faster speeds outside of the tunnel |
Consumes more bandwidth on VPN connections |
Reduces bandwidth usage on VPN connections |
Benefits of a VPN tunnel
A VPN tunnel is the core VPN function that helps ensure the privacy and security of the data you send and receive by encrypting your traffic before it leaves your device. This makes it far more difficult for advertisers, ISPs, or cybercriminals to track you, intercept your data, or monitor your activity.
Here are some additional benefits of a VPN tunnel:
- Helps protect against tracking: A VPN tunnel hides your real IP address and encrypts your traffic, making it harder for advertisers, websites, and other third parties to track your online behavior or target you with personalized ads.
- Secures public Wi-Fi: When you use a VPN on public Wi-Fi, your tunneled data is protected from anyone attempting to intercept it. This can help prevent man-in-the-middle (MITM) attacks, where attackers capture information passing through unsecured networks.
- Helps protect against cyberthreats: Some VPNs also integrate built-in threat protection or bundled antivirus software, offering more comprehensive defense against malware and unsafe sites.
- Accessing geo-restricted content: By routing your traffic through servers in other countries, a VPN tunnel can give you access to content libraries and websites that may not be available in your current location.
- Bypass censorship: In countries with strict internet controls, a VPN tunnel can be a vital lifeline to help you stay connected to the services and news you rely on while traveling.
- Avoids ISP throttling: Because a VPN hides what you’re doing online, it can reduce certain types of content-based throttling, such as when ISPs slow down video streaming or online gaming traffic to manage congestion.
Disadvantages of a VPN tunnel
Sending your traffic through a remote VPN server can sometimes create drawbacks, especially if the VPN is low-quality or poorly configured. Knowing these limitations can help you decide whether full tunneling or split tunneling is the better fit for your needs.
Here are the main disadvantages of a VPN tunnel:
- Slower speeds and increased latency: A VPN tunnel adds an extra step to your connection, which can reduce speeds or increase ping, especially if the VPN server is far away or overloaded.
- Connection drops: Lower-quality VPNs may suffer from unstable servers that drop the connection. If the VPN drops without a kill switch, your real IP address or unencrypted data could be exposed.
- Data logging: Not all VPNs follow a strict no-log policy. Some collect connection metadata and may even sell user data to advertisers, undermining the main privacy benefits of using a VPN in the first place.
- Blocked access: Some websites and streaming platforms block traffic from known VPN servers. This is where split tunneling comes in, letting you exclude specific apps and websites from your secure tunnel
Some of these potential disadvantages can be avoided by choosing a reputable VPN provider with a strong no-logs policy, reliable servers, and optional add-ons like antivirus protection or ad blocking for more complete privacy and protection.
Types of VPN tunneling protocols
VPN tunnels rely on various protocols to create tunnels and encrypt data. These protocols vary in speed and security — here’s an overview.
VPN protocol |
Security |
Speed |
|---|---|---|
Mimic |
High |
Fast |
WireGuard |
High |
Fast |
OpenVPN |
High |
Medium |
L2TP/IPSec |
Moderate |
Medium |
IKEv2/IPSec |
High |
Medium |
SSTP |
High |
Medium |
PPTP |
Low |
Fast |
Mimic
Norton’s Mimic protocol is a proprietary VPN protocol that disguises your tunneled connection data as HTTPS traffic. This means your connection appears to be secure web traffic, allowing it to bypass firewalls and VPN-blocking technologies. It also uses less power and is capable of establishing high-speed connections.
Mimic features patented post-quantum cryptography to protect against cyberattacks, such as simple hacking attempts from classic computers to high-tech hackers with access to the most advanced decryption software.
- Security: High
- Speed: Fast
- Type: Full tunnel or split tunnel
The only place you can get a VPN with Mimic protocol is Norton VPN. It’s available for Android, iOS, Windows, and macOS devices, and allows you to switch between split and full tunneling depending on what you’re doing online.
WireGuard
WireGuard is an open-source VPN protocol. It’s known for fast connection speeds, efficient resource usage, and straightforward configuration. WireGuard uses advanced cryptographic techniques to create a secure, encrypted data tunnel.
WireGuard was released in 2020 and is still under active development. Ongoing updates aim to improve speed, stability, and integration with apps, so its performance is expected to keep getting better over time.
- Security: High
- Speed: Fast
- Type: Full tunnel or split tunnel
OpenVPN
OpenVPN is a widely used, open-source VPN protocol known for its strong security and flexibility. Its strength in encryption, customizability, and ability to bypass firewalls make it one of the most popular VPN tunneling protocols.
This protocol works with major operating systems, including Linux, Windows, macOS, Android, and iOS. It supports both TCP and UDP connections across these operating systems.
- Security: High
- Speed: Medium
- Type: Full tunnel or split tunnel
Layer 2 Tunneling Protocol (L2TP/IPSec)
L2TP/IPsec tunneling combines the Layer 2 Tunneling Protocol and Internet Protocol Security to establish a secure VPN connection. L2TP creates a tunnel for data transmission, while IPsec handles the encryption and authentication of that data. Together, they provide reliable VPN connections for various devices and operating systems.
L2TP/IPSec is an older protocol considered slower and less secure than newer protocols like OpenVPN and WireGuard. Despite this, it’s still widely supported. However, you should avoid using it if you have stronger alternatives that match your needs.
- Security: Moderate
- Speed: Medium
- Type: Full tunnel
Internet Key Exchange (IKEv2/IPSec)
IKEv2/IPsec combines the higher security of the Internet Key Exchange with IPSec. It’s considered the faster, more stable cousin to L2TP/IPSec. It’s also ideal for mobile devices thanks to MOBIKE, a feature that switches between mobile and Wi-Fi connections while maintaining its connection.
IKEv2/IPsec is generally faster than OpenVPN, but not as fast as WireGuard. Due to its mobile-friendly features, it remains a popular way to use a VPN on iOS and Android devices.
- Security: High
- Speed: Medium
- Type: Full tunnel and (depending on the VPN client/OS) split tunnel
Secure Socket Tunneling Protocol (SSTP)
SSTP is a secure VPN protocol developed by Microsoft. It uses an SSL/TLS-encrypted tunnel and is built into Windows devices. SSTP is stealthy enough to bypass some firewalls, but does not include built-in obfuscation features.
Unlike most VPN protocols, SSTP is only built into Windows and works natively there without a third-party VPN client. On other platforms, like Linux, macOS, or Android, you either need to install a VPN app that includes SSTP support or rely on community tools like SSTP-Client for Linux.
SSTP is a secure VPN protocol developed by Microsoft that creates an SSL/TLS-encrypted tunnel. Because it uses the same port as HTTPS, SSTP can slip through many basic firewalls, although it does not provide additional built-in obfuscation features.
SSTP is natively supported only on Windows, where it can be used without installing a third-party client. On other platforms — including Linux, macOS, and Android — you must either use a VPN provider that offers SSTP support or rely on community tools such as SSTP-Client for Linux.
- Security: High
- Speed: Medium
- Type: Full tunnel and (depending on the VPN client/OS) split tunnel
Point-to-Point Tunneling Protocol (PPTP)
PPTP (Point-to-Point Tunneling Protocol) is one of the oldest VPN protocols and isn’t used much anymore. In its heyday, it was known for its extremely fast connection speeds and easy setup. But that speed comes at a cost, because its level of data encryption is weak compared to today's standards. That means it's easier for hackers to access user data in transit.
- Security: Low
- Speed: Fast
- Type: Full tunnel
Make your VPN work for you
The security, speed, and compatibility of a VPN ultimately come down to the strengths of its underlying protocols.
Norton VPN offers powerful encryption with fast connection speeds and a choice of several industry-leading tunneling protocols like WireGuard and OpenVPN, as well as Mimic, our proprietary VPN protocol that masquerades as a standard HTTPS connection for ultimate privacy, security, and accessibility.
FAQs
What’s the difference between a VPN, a VPN server, and a VPN tunnel?
A VPN is a service that protects your privacy by masking your IP address and online activity. It creates a secure, encrypted VPN tunnel between your device and a remote VPN server, safeguarding your online data from interception. The VPN server acts as an intermediary between your device and the wider internet, hiding your real location and identity.
Can VPN tunnels get hacked?
A VPN tunnel can be hacked, but this is rare and usually happens with low-quality, outdated, or cracked VPN. The level of security depends on the protocol, encryption strength, and the provider’s safeguards. High-quality services like Norton VPN use strong standards such as AES-256, making direct attacks on the tunnel practically impossible.
Can a VPN tunnel block all forms of online tracking?
No, VPN tunnels can’t block every type of online tracking. It hides your IP address, but tracking based on cookies, browser fingerprinting, or device identifiers can still follow you across sites. A VPN with an integrated ad and tracker blocker can reduce some of this, but it won’t stop all tracking methods.
Can a VPN tunnel protect against cyberattacks?
A VPN tunnel can protect you from network-based attacks, such as criminals intercepting your data on public Wi-Fi. However, it cannot stop phishing attacks, malicious links, or other scams that trick you into revealing information. For full protection, pair a VPN with security tools like antivirus software and safe browsing features.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.








Want more?
Follow us for all the latest news, tips, and updates.