15 types of malware: real-world examples and protection tips
From crippling malware that can hijack your device to stealthy programs that steal your personal information, the risks posed by different types of malware are real — and growing. In this guide, you’ll discover the most common types of malware, find examples of real-life cyberattacks, and learn how Norton 360 Deluxe can help defend against malware and safeguard your digital life.

Malware is a program, code, or file designed to disrupt, damage, or steal data. Many malware attacks accompany scams that aim at stealing money, taking personal data, or holding information for ransom. Other malware attacks lead to unauthorized network access or cause major system disruptions.
Malware comes in many forms, and knowing the different types and how they can affect you is important. Below, you’ll learn about 15 types of malware attacks, how they work, different real-life malware examples, and what you can do to protect yourself.
Types of malware |
What the type of malware does |
Self-replicate and infect other files |
|
Spread independently through networks |
|
Disguise themselves as legitimate software |
|
Encrypts files and demands payment |
|
Create networks of infected computers |
|
Displays unwanted advertisements |
|
Secretly monitors user activity |
|
Hide malicious activity from detection |
|
Runs in memory without leaving a trace |
|
Spreads malware through fake ads |
|
Record keystrokes to steal information |
|
Steal computing power for crypto mining |
|
Permanently destroy data |
|
Creates false security alerts |
|
Trigger damage based on predefined rules |
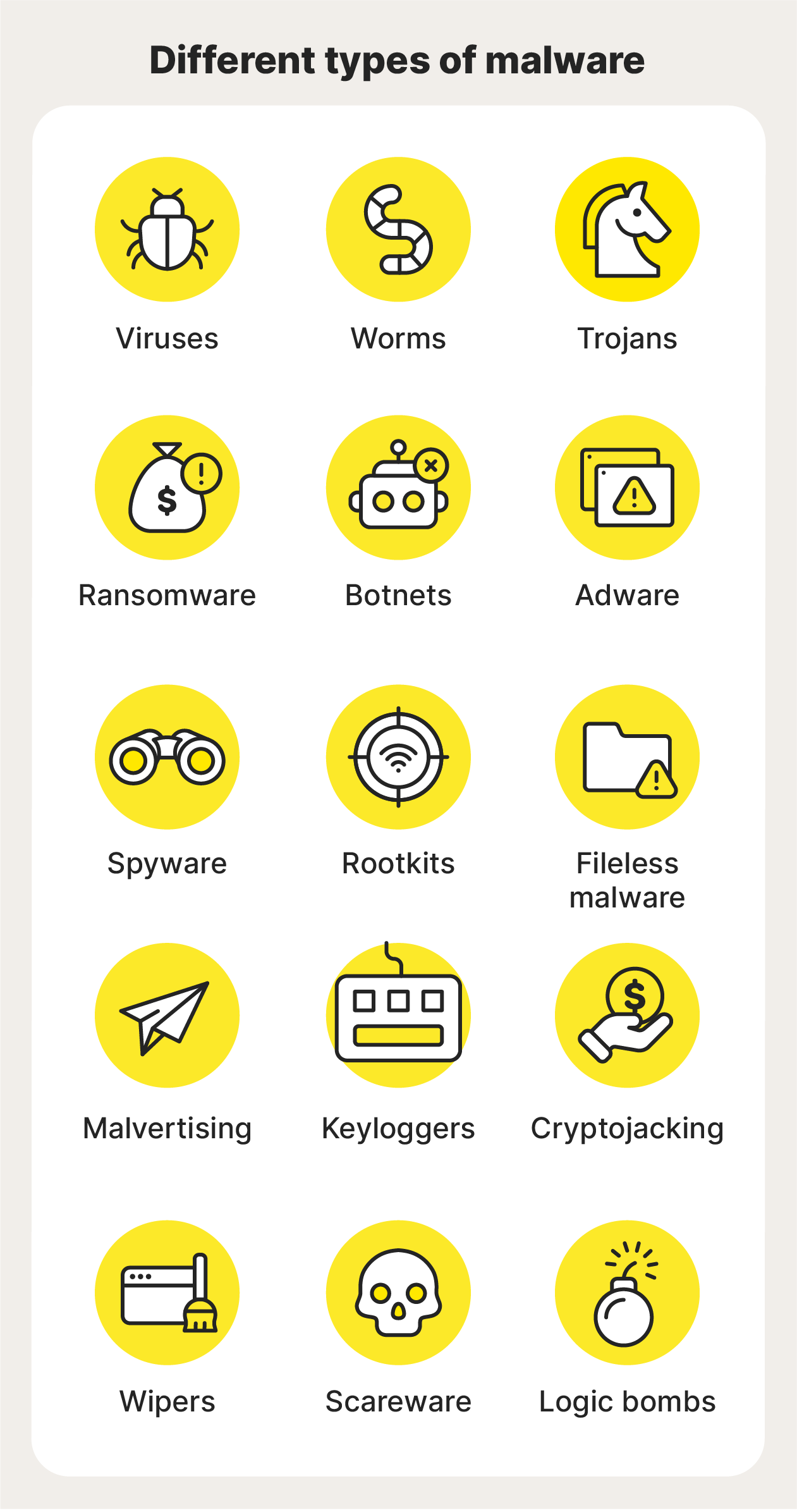
1. Viruses
A virus is malicious code that’s embedded within an application and activates when you open the app. It is named after its biological counterpart because viruses need a host (the application) to survive and spread.
Computer viruses can:
- Replicate by modifying code in your applications
- Stay dormant until you use infected programs
- Change their form to help evade antivirus detection
- Launch DDoS attacks to slow down or freeze your devices
- Exploit system vulnerabilities to spread
While many people often use “virus” interchangeably with malware, viruses are unique in the way they activate and spread. So although all viruses are a form of malware, not all types of malware are viruses.
Very common during the early days of the web, true viruses are an increasingly rare form of malware; they have largely been replaced by newer, more sophisticated malware strains. However, scammers may still send you links or PDFs with viruses, so open attachments with caution.
2. Worms
A worm is a self-replicating malicious program that spreads across networks without needing a host application, exploiting vulnerabilities to move between devices. Its autonomous nature and rapid spread make it particularly dangerous.
Worms can:
- Self-replicate without host applications
- Activate without user interaction
- Move between devices across networks
- Slow down computer and network performance
- Corrupt files and create security backdoors
- Install additional malware types
Worms earned their name because they “wriggle” across networks by exploiting system vulnerabilities such as outdated operating systems or other software. This makes them a particularly flexible and capable form of cyber attack.
3. Trojans
Trojans are a deceptive type of malware that masquerade as legitimate programs or files to deceive users into downloading and opening them. Unlike viruses or worms, Trojans do not self-replicate. Instead, they rely on social engineering to trick victims.
Trojan malware can:
- Take screenshots of your computer.
- Send messages using your applications.
- Disable your computer’s antivirus software.
- Install other kinds of malware.
Trojan malware earned its name from the ancient Greek Trojan horse myth. Like their namesake, the contents of Trojan malware can be extremely dangerous: once activated, they can steal data, damage systems, or create backdoors for hackers.
4. Ransomware
Ransomware encrypts a victim's data or locks their device, demanding payment for access or decryption. But even after payment, there’s no guarantee of recovery, making it a highly unpredictable and dangerous threat.
Ransomware can:
- Lock users out of devices completely
- Encrypt data, making it inaccessible
- Steal and leak data
- Disrupt system operations
Ransomware attacks can be devastating for businesses and individuals alike, as they often lead to significant financial losses and prolonged downtime. Some ransomware variants also threaten to release stolen sensitive data on the dark web, adding an extra layer of extortion.
5. Botnets
Botnets (or bots) are networks of infected computers that hackers control remotely. Unlike other malware types, botnets take over your device alongside several other devices, using them to flood servers with traffic, mine cryptocurrency, or send spam. They often result in your IP address being blocked or flagged, preventing you from visiting certain websites.
Bots networks can:
- Launch phishing attacks
- Search devices for sensitive data
- Perform DDoS attacks
- Conduct malicious activities under your IP address
Botnets can operate silently in the background while using your computer’s resources for criminal activities. If your computer is unusually slow, check your device’s task manager to see if unknown programs are running in the background.
6. Adware
Adware, short for advertising-supported software, displays unwanted advertisements while tracking your browsing activity. While some adware is used for legitimate marketing purposes, malicious versions can be platforms for malvertising or scareware. They can also facilitate identity thef.
Adware can:
- Display unwanted advertisements and pop-ups
- Disrupt the normal browsing experience
- Track and share your information with third parties
- Direct you to malicious websites through deceptive ads
7. Spyware
Spyware is malicious software that secretly infiltrates your device to monitor your internet activity, capture login credentials, and collect sensitive information. It’s particularly dangerous because it can operate undetected for prolonged periods, potentially leading to identity theft.
Spyware can:
- Collect personal data without consent
- Monitor your activity in real time
- Operate stealthily in the background
- Share your private information with criminals
- Cause your device to slow down
Unlike some forms of malware — such as worms — which function in a highly specific way, spyware is a broad category of malware that relates to what it does, not how it does it. Most commonly deployed via Trojans, spyware can also spread via worms or rootkits.
8. Rootkits
Rootkits are sophisticated malware that infiltrate devices at the operating system level, giving cybercriminals full, remote control of your computer or phone. By exploiting system-level privileges to disable security software, rootkits can remain hidden for extended periods.
Rootkits can:
- Take remote control of infected devices
- Grant cybercriminals admin access
- Spy on user activity
- Disable security software
- Hide the presence of other malware
Rootkits’ stealth makes them particularly dangerous, as they can be used to install additional malware, steal sensitive data, or monitor user activity without detection, often compromising a device long before the victim realizes anything is wrong.
9. Fileless malware
Fileless malware operates without leaving traditional files on a system. Instead, it exploits legitimate tools, like system memory or in-built processes, to execute malicious code. This makes it harder to detect, as it can avoid some conventional antivirus scans and leaves minimal traces on infected devices.
Fileless malware can:
- Execute attacks without using malicious files
- Piggyback on legitimate system processes
- Bypass certain types of traditional antivirus software
- Operate using trusted system tools
The evasive nature of fileless malware allows it to potentially persist much longer than traditional malware. And even though it removes itself after restarting, it can use system tools like PowerShell to spread between computers.
10. Malvertising
Malvertising spreads malicious code through deceptive ads containing hidden threats like infected images, cookies, or scripts. These ads can compromise your device when clicked or even just viewed. Malvertising can appear on both legitimate and malicious websites.
Malvertising can:
- Steal credit card information
- Install malware automatically through drive-by downloads
- Damage the reputation of legitimate businesses
- Infect devices through trusted websites.
Malvertising is difficult to prevent because it often exploits trusted ad networks to spread malware, meaning both site owners and users might be caught unaware.
11. Keyloggers
Keyloggers are a specific type of spyware that record everything you type on your device. They may take screenshots or monitor other system activity too. They’re often used by cybercriminals to steal sensitive data like passwords, credit card numbers, or the contents of private messages.
Keyloggers can:
- Attach to firmware such as your computer’s BIOS
- Be implanted by Trojans or fileless malware
- Record sensitive personal information
- Take screenshots and monitor system activity
Many modern keyloggers can also capture clipboard contents, record audio, and rip webcam inputs, making them powerful tools for comprehensive surveillance and data theft.
12. Cryptojackers
Cryptojacking malware hijacks a computer’s resources to mine cryptocurrency for cybercriminals. Unlike other malware that might destroy a system or steal data, cryptojackers seek to profit by exploiting others’ computing resources.
Cryptojackers can:
- Siphon computer processing power
- Increase electricity costs
- Slow down host devices
- Cause host devices to overheat
While cryptojacking may seem less harmful than data theft or ransomware, its impact can be significant. The constant strain on a device can cause slow performance, overheating, and increased energy consumption, leading to higher electricity bills.
13. Wipers
Wipers permanently delete data from infected devices. Unlike ransomware, which holds data hostage, wipers simply delete it. They can render devices inoperable by targeting critical boot systems.
Wiper malware can:
- Permanently erase data beyond recovery
- Target and destroy boot systems
- Render devices completely unusable
- Serve as a tool for cyberwarfare
Wipers might also steal data before removing it from a system; they are often used in targeted attacks by cybercriminals or state-sponsored actors to cripple systems, disrupt operations, or destroy sensitive data, leaving little to no trace.
14. Scareware
Scareware is designed to deceive users into thinking their device is infected with viruses or threats. It typically displays fake security alerts or system scans, pressuring users to purchase unnecessary software or services. These tactics exploit fear and urgency, often leading to financial loss or further compromising their security.
Scareware can:
- Display fake virus warnings and security alerts
- Trick users into downloading malware
- Direct targets to fake phishing websites
- Initiate tech support scams
- Generate persistent pop-up messages
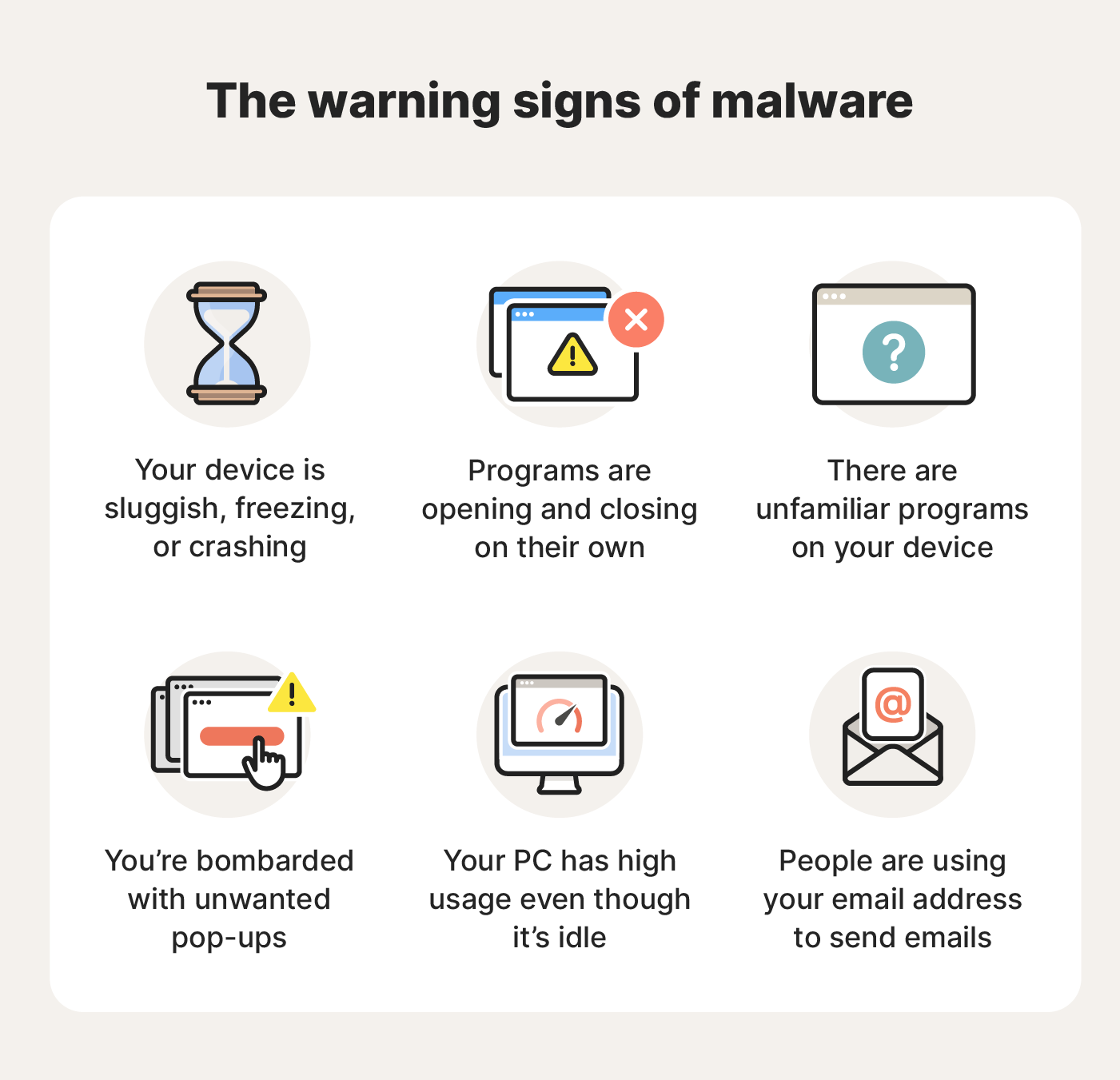
Warning signs of malware include unexpected pop-up alerts, urgent messages claiming your device is infected, and requests to download or purchase security software from untrusted sources.
15. Logic bombs
Logic bombs lie dormant until the user meets specific trigger conditions. Unlike other malware that activates immediately, logic bombs wait for particular circumstances before activating, such as a specific date, time, or user action.
Logic bombs can:
- Delete important files from your device
- Corrupt data and crash your system
- Leak sensitive information
- Cause slowdowns and system failures
Logic bombs get their name from how their code “detonates” after meeting certain conditions. Unlike other forms of malware, they don’t self-replicate or spread; they are typically tailored for targeted attacks, making them harder to detect until the damage is done.

How is malware injected or deployed?
Malware can be injected or deployed through various methods, including phishing emails, malicious website downloads, infected USB drives, and software vulnerabilities. But email is by far the most common attack vector, with 88% of malware attacks in 2023 arriving via email.
Here’s a closer look at the specific techniques cybercriminals use to spread malware:
- Security vulnerabilities: When vulnerabilities in devices and software are discovered, hackers can take advantage to launch what’s known as a zero-day exploit.
- Exploit kits: Cybercriminals may use purpose-built exploit kits to search for device vulnerabilities and inject malware through loopholes in security infrastructure.
- Man-in-the-middle attacks: Malware can be injected into intercepted internet data during a man-in-the-middle attack.
- Drive-by downloads: When users visit a malicious website, drive-by-downloads automatically send users a file without their knowledge, exploiting vulnerabilities in a user’s browser.
- Social engineering: Cybercriminals can manipulate people into clicking malicious links, downloading bad attachments, or sharing sensitive information. This can encompass email phishing, vishing, or smishing.
- USB and External Devices: Malware is delivered via infected USB drives or other external devices plugged into a computer.
- Trojanized Software: Malware is hidden inside seemingly legitimate software that installs alongside the program.
- Network Infiltration: Hackers breach a network to plant malware, often using brute-force attacks or stolen credentials.

How to protect yourself from malware
You can significantly reduce your exposure to malware by adopting proactive measures such as using trusted antivirus software, keeping systems updated, practicing safe browsing habits, and avoiding suspicious links or downloads.
- Keep software updated: Regularly update your software and operating system to patch vulnerabilities that malware could exploit.
- Avoid suspicious links and attachments: Never click on links or download attachments from unknown emails, messages, or websites as they could harbor malware.
- Adjust spam filters: Configure your spam filters so you’re less likely to engage with a malicious link, email, or attachment to begin with.
- Practice safe browsing: Stick to secure, well-known websites and be cautious of clicking on ads or pop-ups that could lead to malicious sites.
- Backup your data: Regularly back up important files to minimize loss in case of infection by a wiper or ransomware.
- Limit admin privileges: Restrict admin access to reduce the potential damage malware can cause on your device or network.
- Avoid third-party app stores: Install software and apps only from official vendors or verified platforms to reduce the risk of downloading Trojans.
- Enable a firewall: Use a firewall to monitor incoming and outgoing network traffic and block unauthorized access.
- Install trusted security software: Use a reputable antivirus to help detect and block threats before they can harm your device.
Protect yourself from different types of malware
With so many different types of malware to contend with, you need 360-degree protection.
From viruses and ransomware to spyware and cryptojackers, Norton 360 Deluxe provides comprehensive protection against malware. With powerful real-time threat detection, Smart Firewall protection, and 50 GB of Cloud Backup storage, Norton 360 Deluxe helps protect you from all angles.
FAQs
What’s the hardest malware to detect?
The hardest type of malware to detect is often fileless malware, because it doesn’t leave traces on a hard drive and can evade traditional file-based detection techniques. That’s why it’s important to use a cutting-edge antivirus like Norton 360 Deluxe, which uses heuristic behavior-detection techniques to identify threats.
How does malware spread?
Malware spreads through infected email attachments, malicious websites, software vulnerabilities, compromised networks, or removable media. It can also propagate via phishing attacks, social engineering, or file-sharing platforms. Once executed, malware may be able to independently spread to other devices and systems.
Can malware damage your computer hardware?
While malware typically targets software and data, some types, like crypto miners or firmware attacks, can indirectly damage hardware by causing GPU or CPU overheating, or physical wear due to intensive processing.
Can I get malware from public Wi-Fi?
Yes, public Wi-Fi networks can be exploited to perform man-in-the-middle attacks in which hackers intercept data in transit and inject malicious code into the data packets. Using a VPN to encrypt the data you send and receive helps protect against this risk.
How many types of malware are there?
There are many types of malware including viruses, trojans, ransomware, botnets, and keyloggers. Some of these malware types can even hybridize, meaning malware can fall into multiple categories. And the number of types continues to grow as evolving threats emerge.
Editorial note: Our articles are designed to provide educational information for you. They may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review the complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc. For more details about how we create, review, and update content, please see our Editorial Policy.
- 1. Viruses
- 2. Worms
- 3. Trojans
- 4. Ransomware
- 5. Botnets
- 6. Adware
- 7. Spyware
- 8. Rootkits
- 9. Fileless malware
- 10. Malvertising
- 11. Keyloggers
- 12. Cryptojackers
- 13. Wipers
- 14. Scareware
- 15. Logic bombs
- How is malware injected or deployed?
- How to protect yourself from malware
- Protect yourself from different types of malware
- FAQs








Want more?
Follow us for all the latest news, tips, and updates.