What is cyberstalking? Key signs and ways to stay safer online
Cyberstalking is a problem that can impact anyone who uses the internet. Instead of brushing it off, take steps to boost your privacy online, lock down your devices, and learn how to report these crimes. Then, install a cybersecurity app to help secure your internet connection and protect your privacy so you can reclaim your digital life.

Cyberstalking can start as something minor — a few messages, a “follow” here, a “like” there — and quickly escalate into a relentless pursuit. Cyberstalking is rising faster than traditional stalking, with victims increasingly targeted through unwanted texts or social media messages. The hit Netflix show “Baby Reindeer,” based on real events, highlights this danger, showing both online and in-person stalking while authorities dismiss the threat and the perpetrator goes unconvicted.
Though cyberstalking can happen to anyone, women, young adults, and non-heterosexual individuals are more likely to be stalked, according to a 2025 study in The British Journal of Criminology.
However, armed with the right information, protecting yourself is possible. This post will walk you through the types of cyberstalking, how to recognize the signs, and what to do if you think you’re being targeted.
What is cyberstalking?
Cyberstalking is a form of online harassment where someone uses the internet or connected devices to monitor, intimidate, or threaten another person. It can happen on social media, through email or tracking software, or even via hacked devices. Cyberstalking isn't just a one-time incident, either — it's persistent and repeated.
It often begins with excessive contact, like repeated DMs or emails, but can evolve into something more threatening, including identity theft, public shaming, blackmail, and cyberbullying.
Stalking is a crime in all 50 states, and most state stalking laws include specific statutes covering digital stalking, too. But knowing when attention crosses the line into stalking, and learning how to protect yourself against cybercrimes, can help you put the severity of the issue into perspective.
Can looking at someone’s social media posts and photos be considered cyberstalking?
Many people use the phrases “creeping” and “stalking” to describe following someone’s online activities on social media or closely examining their profiles. But checking in on an ex-partner’s public posts or scrolling through your friend’s likes isn’t a crime, because those actions usually don’t involve harassment or other criminal activity.
However, when looking at someone’s social media posts becomes excessive, unwanted, or tied to intimidation or harassment, it may cross the line.
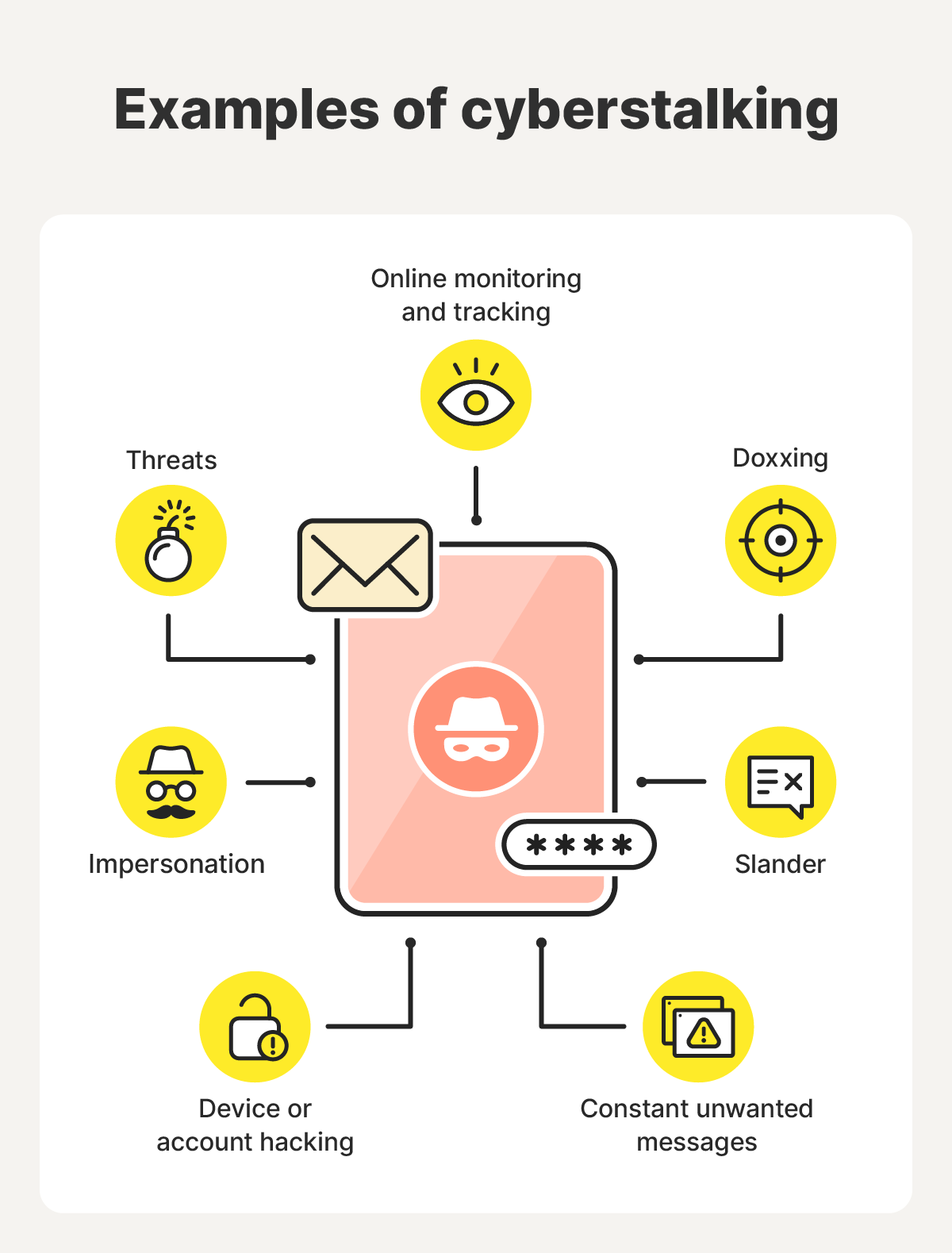
What are examples of cyberstalking?
Examples of cyberstalking include sending unwanted messages, hacking into devices, and engaging in blackmail. Motives can vary from jealousy and revenge to control or obsession. In some cases, stalkers on social media don’t even personally know the person they’re targeting.
According to the Cyberbullying Research Center, cyberstalking behavior is especially dangerous because it's easy to hide behind anonymous profiles, fake accounts, or even AI-generated personas that automate targeted harassment.
Other cybersecurity statistics show that 20% of people believe their romantic partner is somewhat likely to plant a cyberstalking program on their phone. That number shows just how prevalent this type of cybercrime is.
Below, we cover common examples of cyberstalking in detail.
Constant unwanted messages
Some cyberstalkers may flood your inboxes with emails, texts, or DMs. These can start friendly but quickly shift to obsessive or aggressive tones. It may be violent or just excessive and unwanted communication.
Reddit users have described receiving harassing messages, including threats of kidnapping and other violence. Some have even admitted to cyberstalking themselves, like this Reddit user who confessed to cyberstalking a girl at his gym — it started as a simple crush before evolving into excessive messaging through a fake Instagram account.
Online monitoring and tracking
Online monitoring and tracking can be one of the more subtle forms of internet stalking. The ethics vary depending on who you ask: many people believe that checking someone out online is fine, but the threshold for when it starts becoming obsessive depends on the context and frequency.
This Reddit thread is a perfect example, where a user asked how far others have gone while social media stalking. Answers varied greatly, ranging from a quick social media check to a thorough review of someone else’s online activity, including Discord likes, Spotify profile data, and every public photo available.
Some cyberstalkers take it to the next level and use spyware, location-sharing apps, or social media surveillance to keep tabs on where you are, what you post, and who you’re with. This online monitoring can be invasive and may serve as a precursor to real-world harassment.
Hacking into devices or accounts
Some cyberstalkers gain unauthorized access to phones, email accounts, or even smart home devices. They might read private messages, steal sensitive information, or impersonate you.
For example, a victim of cyberstalking asked for help in a Google forum because their email account had been hacked. The cyberstalker-turned-hacker had forwarded personal messages to the target’s contacts, to whoever they thought would be most offended by them.
Threats of violence or blackmail
When stalkers escalate, it’s serious, and some may threaten harm or try to blackmail you with compromising content. This social media threat may start with the stalker trying to build a relationship with you. For example, someone might use information or photos shared in private messages against you, a tactic often seen in romance scams.
Some cyberstalkers may blackmail you using other sensitive information. In one case, a blackmailer threatened Nikkie Tutorials, a professional beauty influencer and makeup artist, by outing her trans identity, which she hadn’t publicly disclosed at the time. Thankfully, she managed to take control of the story and has grown her YouTube channel to a dizzying 15 million subscribers.
Derogatory statements or false accusations
Internet stalking often includes spreading rumors, lies, or false accusations to damage the victim’s reputation. Some stalkers create fake posts or even websites to humiliate or discredit others.
In 2024, Taylor Swift was targeted with nude deepfakes in an attempt to exploit her image and brand. Since then, many similar celebrity cases have emerged.
This threat goes beyond celebrities, too, with perpetrators using AI to slander people more easily. For example, a disgruntled teacher used AI voice cloning to frame his school’s principal, making it seem like the victim was saying racist and disparaging comments about students and teachers.
Identity theft and impersonation
In some cases, cyberstalkers may use your personal details to impersonate you online. They might create fake social media profiles or use deepfake AI tools to cause harm to you and your community.
One such case happened in Albuquerque, when a woman assumed different identities to harass and extort various victims for years. This case highlights how cyberstalkers can also use other tactics, such as identity theft and fraud, to stalk and extort victims.
Doxxing
Doxxing is when someone publishes private information, such as your phone number or home address, on the internet. It’s a common tactic to intimidate, shame, or encourage others to join the harassment, and it can put your physical safety at risk.
One example of doxxing involved rapper Nicki Minaj. When a content creator posted a criticism of Minaj’s new song online, some of the rapper’s fans retaliated by doxxing his address and sending him a pizza. While a pizza may seem harmless on the surface, having your personal address and physical location shared publicly can lead to escalation and potential harm for you and your loved ones.

Cyberstalking vs. cyberbullying
The main difference between cyberstalking and cyberbullying lies in intent and intensity.
Cyberbullying often targets younger users, especially between the ages of 12 and 15, and typically includes teenagers “blasting” their peers online to humiliate them.
On the other hand, cyberstalking is more personal and persistent, and often involves threats, surveillance, or emotional manipulation. Its goal often goes beyond online humiliation and is the precursor to potential real-life stalking.
Who can be a cyberstalker?
Anyone, from strangers to family members, can be a cyberstalker. Often, they’re people you know and trust, like the case of a Michigan mother who cyberstalked her daughter for two years, as shown in the Netflix documentary “Unknown Number: The High School Catfish.”
While some people are victims of cyberstalking strangers, 57% of victims know their stalker.
Cyberstalkers can be any of the following:
- Ex-partners
- Family
- Ex-friends
- Acquaintances or coworkers
- Internet strangers
- Social media followers
Sometimes, even bots or hacked accounts are used to facilitate stalking behavior.
Consequences of cyberstalking
Cyberstalking can have a real-world impact, affecting every aspect of life, not only when victims close their browsers or turn off their phones. From impacting social relationships to financial stability, common negative repercussions of cyberstalking can include:
- Psychological turmoil: Anxiety, PTSD, fear, or depression.
- Physical symptoms: Trouble sleeping, headaches, fatigue, nausea, or illness from stress.
- Social problems: Isolation, avoiding online and physical spaces, or strained connections.
- Financial stress: Costs from stolen information, missed work, job loss, or legal action.
If a cyberstalker impersonates someone or shares embarrassing information — like sensitive pictures or videos — it can negatively impact their relationships with friends and family. That can make it more difficult for them to keep or find employment, or live a fulfilling public life.
When cyberstalkers are caught and prosecuted, they face fines of up to $250,000 and as many as five years imprisonment. In some states, convicted cyberstalkers may lose access to firearms.


How to protect yourself against cyberstalking
Cyberstalking is a serious threat, but you’re not powerless. With the right steps and tools, you can help protect yourself.
Manage your personal information
Limit what others can learn about you online to help protect your privacy. Here are a few ways to take control of your personal information:
- Scan the web: Do an online search for your family’s names to see what information is available about them online. If you find details you wouldn't want a cyberstalker to get, learn how to remove personal information from sites.
- Keep personal details private: Avoid listing things like your birthday, school, employer, or address on public profiles. The less personal information you share, the safer you’ll be online.
- Think before you post: Skip sharing real-time updates about where you are or what you’re doing. Posting travel plans or daily routines can unintentionally give away too much information.
Control your online presence
Controlling your online presence, mainly by being as private as possible, can help you avoid potential threats. Here are a few tips to help you achieve that:
- Set social media to private: Use privacy settings on social media so you’re only sharing posts with close friends, relatives, and others in your trusted circle. Privacy settings can help prevent your profile from appearing in results when others search for your name online. Don’t give potential stalkers the chance to find you if you can help it.
- Disable your location: Be careful about publicly sharing information that lets a cyberstalker know where you are. This includes "checking in" somewhere on social media or publicly announcing plans to attend a certain event. If you post photos online via social networks or other methods, be sure to turn off the location services metadata in the photo.
- Use a private browser: Private browsers like Norton Private Browser can help you reduce your digital footprint and block trackers.
- Block suspicious accounts: Don’t hesitate to block or remove anyone who seems intrusive or makes you uncomfortable.
Secure your devices and accounts
Protecting your device with robust security software helps keep you safe from potential hacking threats. Here’s what to do:
- Download security software: Security software like Norton 360 Deluxe alerts you to threats like phishing attacks, and scans your device to find and remove malware. While it’s not a guarantee against cyberstalking, it’s a big step toward helping to keep you and your family safer.
- Scan your device for intruders: Cyberstalkers who get their hands on one of your devices can quickly and easily install stalkerware or spyware to monitor your every online move or track your physical location by phone.
- Use strong passwords and MFA: Passwords should be unique and at least 15 characters. You can even use a strong password generator and a password manager to keep everything organized. Multi-factor authentication helps ensure that even if your password is compromised, your accounts still stay safe.

What U.S. law says about cyberstalking
Cyberstalking is illegal in the U.S., but there isn’t a single, comprehensive law that explicitly provides protections against it. Many laws protecting citizens from cyberstalking are written at the state level, so contact your local law enforcement agency if you’re unsure of your rights. And, check out Justice.gov’s Cyberstalking Guide for further resources.
The few federal protections that do exist include:
- Combat Online Predators Act: A law that increased the maximum prison sentence for perpetrators who stalk minors online.
- 18 U.S. Code § 2261A (Title 18): An anti-stalking law prohibiting various forms of stalking, including using electronics to cause physical harm or emotional distress.
- Violence Against Women Act (VAWA): This act aims to help protect women from violence and harassment. In 2022, lawmakers added new measures relating to cyberstalking, such as protection for victims of non-consensual image sharing.
The VAWA also created the National Resource Center on Cybercrimes Against Individuals to improve protections for victims of cybercrime, and train investigators and others in law enforcement on these types of crimes. As of now, the punishments for cyberstalking may include fines, victim compensation, felony charges, restraining orders, and imprisonment.
How to report cyberstalking
If you encounter someone who’s cyberstalking another person, or you’re receiving threats, report it to the police immediately. Many police departments have cybercrime units that are trained to handle online crimes. When you’re not in immediate danger, there are a few steps to take before contacting the authorities:
- Scan your device: A hacker might have installed spyware or malware on your device, making it unsafe to take any further measures if they’re already one step ahead of you. Use a malware scanner to find and remove any malware.
- Gather evidence: Save absolutely everything — messages, call records, posts, screenshots, and timestamps. Then, compile your evidence somewhere safe.
- Report to the platform: Use built-in tools on social media or messaging apps to report abuse.
- Report the crime to the authorities: Use your collected evidence to report to the local police and the Internet Crime Complaint Center (IC3).
If you suspect that your cyberstalker has access to your device or accounts, seek help via a public computer or someone else’s device to keep your cyberstalker in the dark. Doing so may help prevent them from blocking your reporting efforts.
Stop cyberstalkers in their tracks
Prevention is your first line of defense, but if you find yourself being targeted, remember: you're not alone. Lean on your support network and use trusted tools like Norton 360 Deluxe to help protect your devices from malware, like spyware, and other threats that cyberstalkers might try to use to spy on you or access your personal information.
With strong cybersecurity and privacy practices, you can regain control and prevent stalkers from invading your digital life.
FAQs
Is cyberstalking a crime?
Yes, in many regions, including the U.S., U.K., and Canada, cyberstalking is a crime that can lead to arrest and prosecution.
How is cyberstalking different from other forms of online harassment?
Cyberstalking is different from other forms of online harassment because it’s often persistent, personalized, and threatening in nature — it causes fear of safety. Other forms, such as trolling or cyberbullying, while still harmful, don’t typically have the same violent or obsessive intent.
How do you prove cyberstalking?
Keep absolutely everything: emails, messages, screenshots, and timestamps. Document everything clearly and organize it in chronological order by date. Then, report it.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.
- What is cyberstalking?
- What are examples of cyberstalking?
- Cyberstalking vs. cyberbullying
- Who can be a cyberstalker?
- Consequences of cyberstalking
- How to protect yourself against cyberstalking
- What U.S. law says about cyberstalking
- How to report cyberstalking
- Stop cyberstalkers in their tracks
- FAQs









Want more?
Follow us for all the latest news, tips, and updates.