Password attack 101: A definition + 10 types of password attacks to avoid
This password attack protection guide overviews common types of password attacks, as well as password attack prevention tips to help improve your privacy and cybersecurity.

An unfortunate truth is that signing up for online accounts is a tad easier when you can use a username and password you know you’ll be able to remember — we’re creatures of habit, after all. However, in the digital age, reusing the same login credentials can make you vulnerable to a password attack. These kinds of cyberattacks compromise and exploit your personal information by decoding the passwords used to keep people out.
Thankfully, there are several measures you can take to build your defenses against password crackers, beginning with diving into this comprehensive guide to the types of password attacks. You can explore the different ways people avoid them, in addition to some password theft prevention tips you can use to boost your Cyber Safety.
10 types of password attacks + how to avoid them
By taking the time to understand the different types of password attacks and learning how to avoid them, you can show password hackers you’re playing chess while they fool around with checkers.
1. Brute force attack
A brute force password attack is essentially a guessing game where the hacker tries different password combinations using hacking software until they’re able to crack the code. These hackers hope that their victims either reused a password that’s already compromised or used a generic phrase, such as “12345.”
How to avoid: Create unique passwords for every online account.
2. Credential stuffing
Credential stuffing is a brute force attack that uses stolen credentials to break into your online accounts and profiles. Aside from using spyware and other kinds of malware to get the credentials they want, the dark web often has lists of compromised passwords for cybercriminals to use for their devious plans. Hackers may use these lists to carry out their credential stuffing schemes and exploit your data.
How to avoid: Enable two-factor authentication on your online accounts when possible.
3. Social engineering
Cyberthieves have a variety of skills — one of which is creating believable websites. Password hackers create what people know as social engineering websites that they design to seem like legitimate login pages. These cybercriminals send you to a fake login field that won’t give you access to your account. It only records the information you type in, giving the cybercriminal exactly what they want.
How to avoid: Never click on suspicious links or attachments.
4. Dictionary attack
Another sibling of the brute force attack family is the dictionary attack. These cyberattacks play on our habit of using single-word phrases as our passwords. The hacker may use automated password-guessing software to try every word in the dictionary as your password to see if they have any luck.
More advanced dictionary attack hackers develop a list of keywords specific to your life, such as birthdates, sibling/pet names, and/or previous street names.
How to avoid: Create complex passwords that include a variation of numbers, letters, and symbols.
5. Keylogger attack
A keylogger is spyware used to track and record what you type on your keyboard. Despite being legal to use, depending on the reasoning, hackers take advantage of this software by intentionally infecting vulnerable devices and recording private information without their knowledge.
How to avoid: Install reliable antivirus software onto your device.
6. Password spray attack
Password spraying is when a hacker uses a large number of stolen passwords — sometimes in the millions — on a small number of online accounts to see if they can gain access. Hackers use advanced automated password-guessing software that can limit the number of attempts that it tries on an account. This lets them avoid triggering security alerts and continue trying under the radar.
How to avoid: Make a routine of changing your passwords every couple of months.
7. Phishing
Password phishing attacks often come in the form of an email or text message bringing your attention to some kind of urgent matter. The hacker may pair these messages with a link to a strategically designed social engineering website created to trick you into logging into your profile. These websites will record the credentials you type in, giving the attacker direct access to your actual account.
How to avoid: Double check the URLs before logging into accounts.
8. Man-in-the-middle attack
A man-in-the-middle attack uses phishing messages to pose as a legitimate businesses to complete the following goals:
- Use malicious attachments to install spyware and record the passwords
- Embed links to social engineering websites to get people to compromise their own credentials
How to avoid: Double-check the sender’s email address on suspiciousemail messages.
9. Traffic interception
Traffic interception is a man-in-the-middle attack. This is when password crackers eavesdrop on network activity to capture passwords and other types of sensitive information. There are a number of ways cybercriminals do this, one of which is by monitoring unsecure Wi-Fi connections. But they could also use a tactic called SSL hijacking — when the cybercriminal intercepts a connection between a target and the legitimate site they’re on and records any information shared between the two.
How to avoid: Avoid public Wi-Fi and install a VPN.
10. Shoulder surfing
Being aware of your physical surroundings is just as important as watching for suspicious activity online. One way that hackers get their hands on passwords is by looking over people’s shoulders in public as they type. People are often too focused on putting in their password to check for nosey neighbors looking their way.
How to avoid: Enable biometric features like facial recognition to sign into accounts on mobile devices.
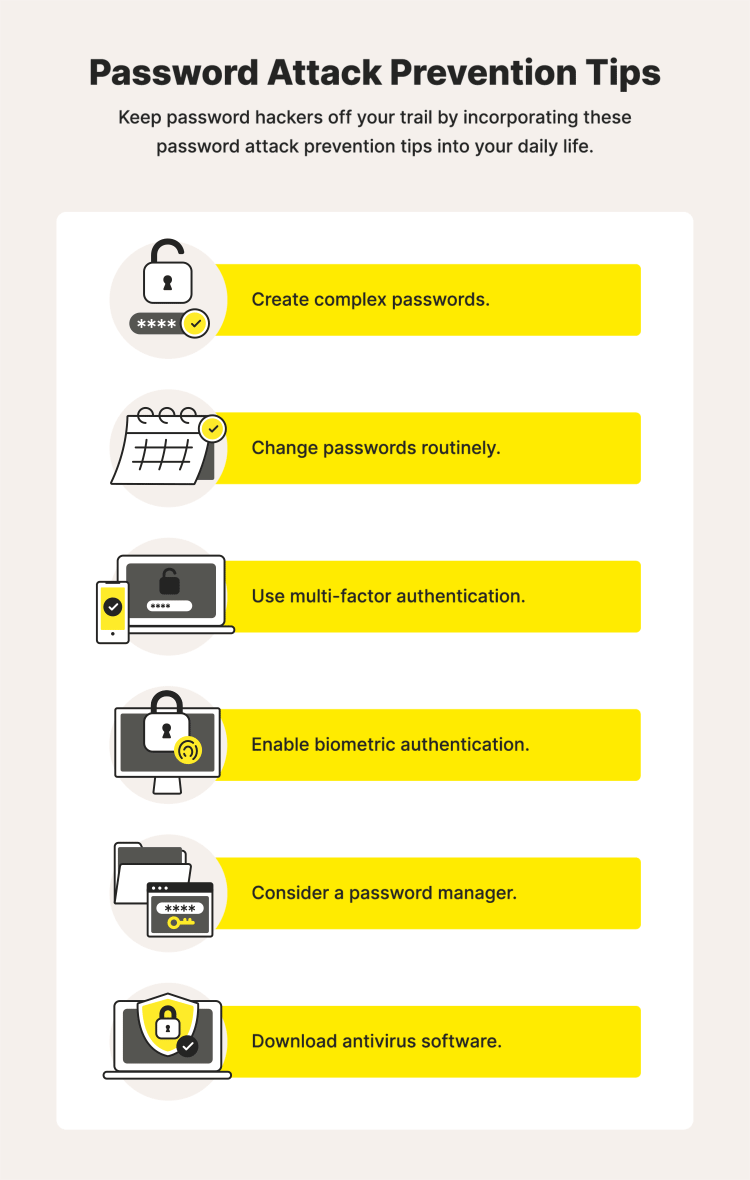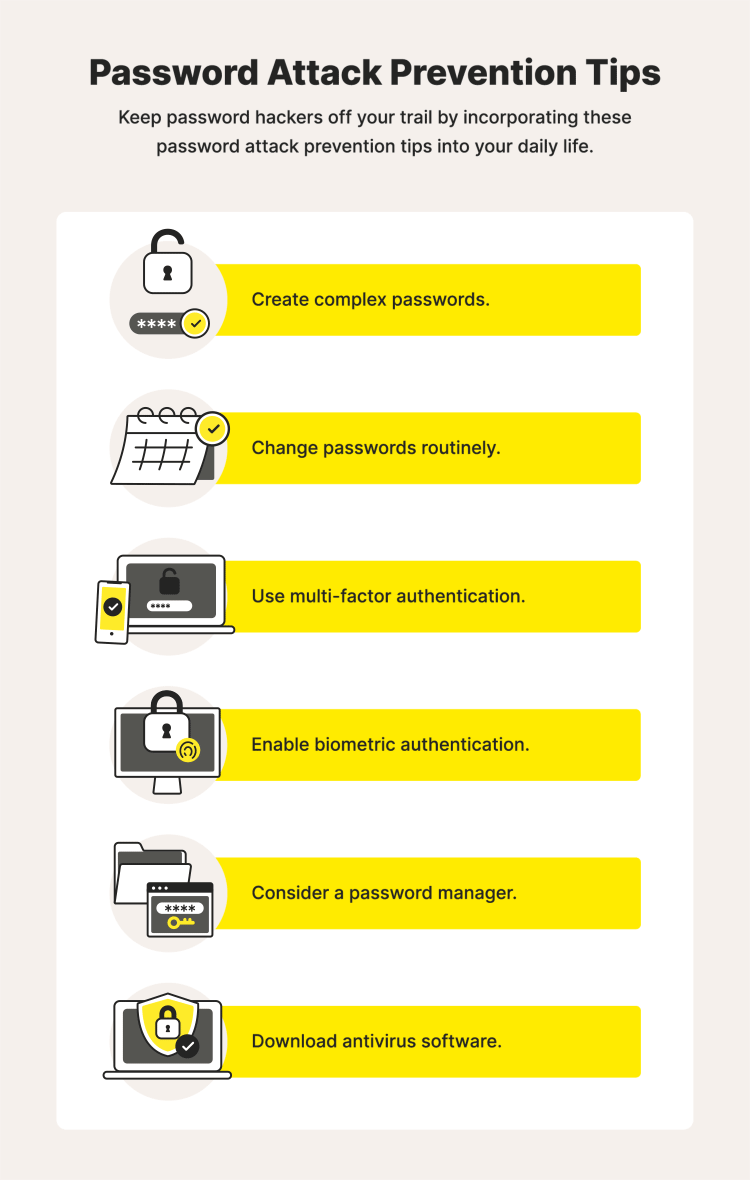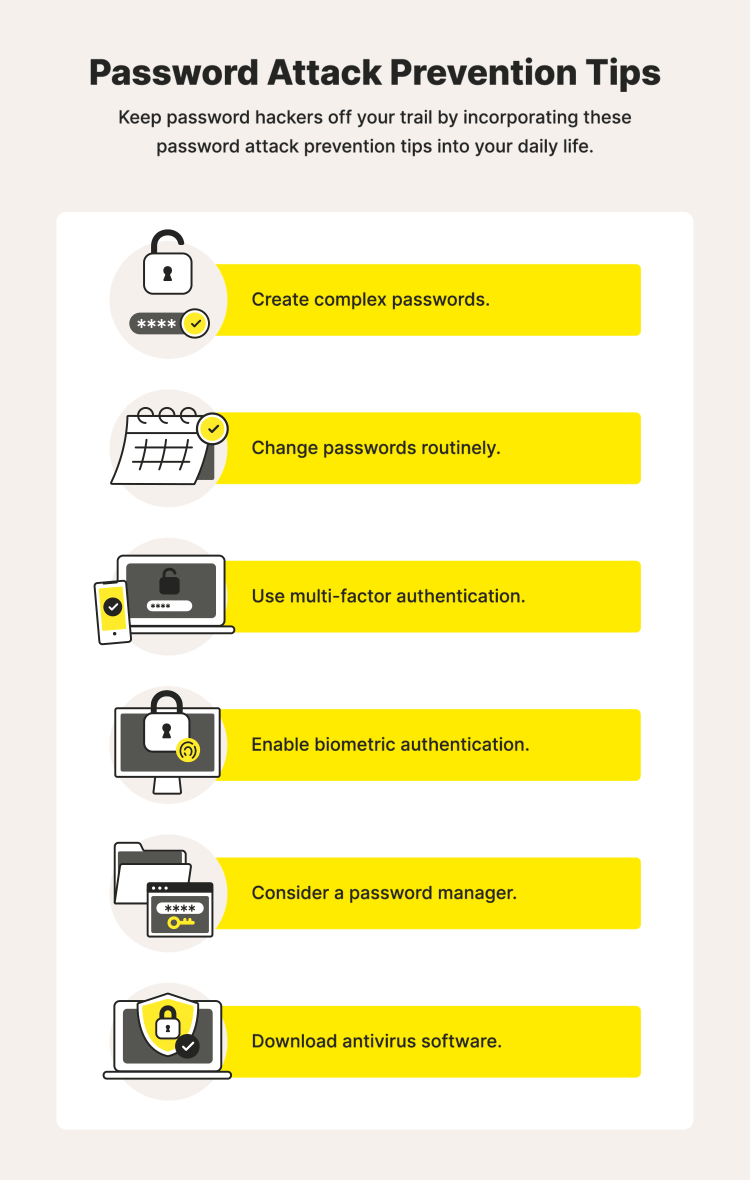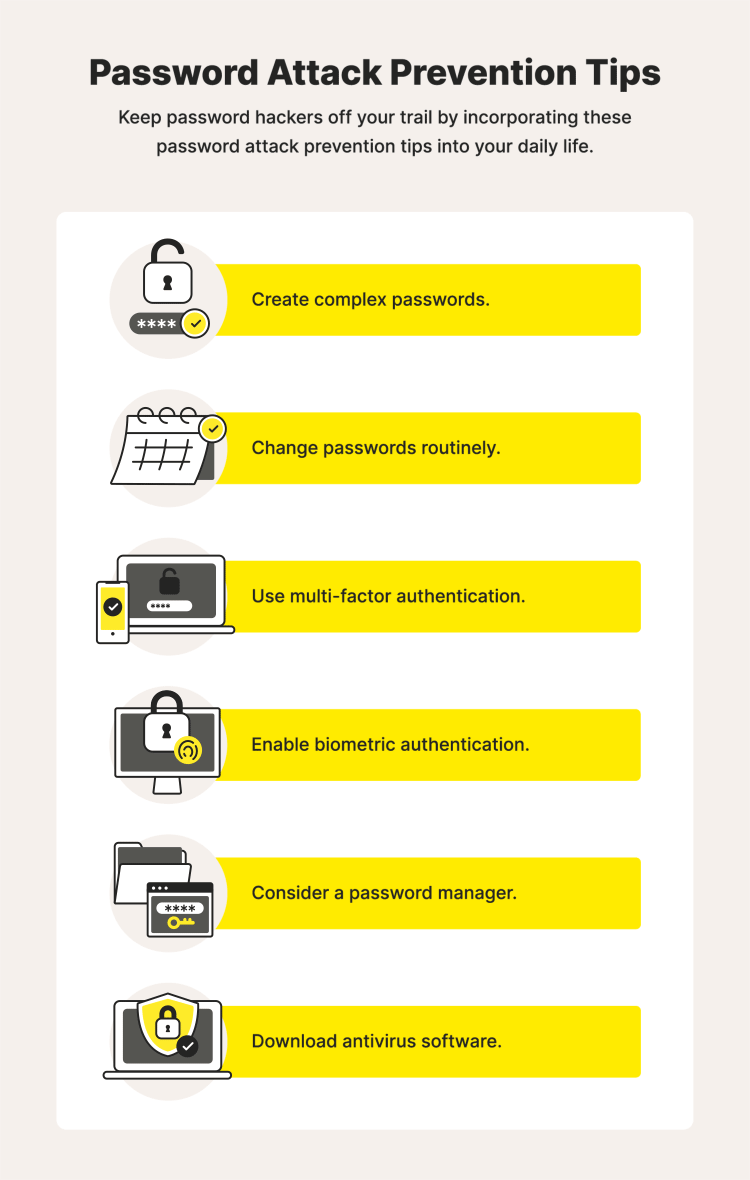
How to prevent password attacks
When it comes to hackers and their password attacks, you have a lot more power than you think. Take a look at all the things you can do to keep password attacks and the potential dangers they present at bay.
Create complex passwords
This may seem obvious, but creating strong, reliable passwords is essential to protect your data. Reusing passwords or creating basic phrases could make you susceptible to cyberattacks, such as password spraying, credential stuffing, and more.
Change passwords routinely
Making a routine of changing your passwords can help keep password crackers guessing. For accounts holding medical and/or financial details, try switching things up every two or three months. Other than that, six months to a year is a good timetable. Even if a cybercriminal is able to get close to cracking your password, they’ll have to start over once you change it.
Use multi-factor authentication
Multi-factor authentication, aka two-factor authentication, presents the opportunity to add another layer of protection to help keep your data safe. It can range from a unique code sent via email or text to predetermined security questions that only you know the answer to.
Enable biometric authentication
Biometric security features are an excellent tool for those looking to protect themselves from cybercriminals. As another form of multi-factor authentication, facial recognition and fingerprint technology help ensure that only you will see the account information in need of protection.
Consider a password manager
Password managers are great for people looking to add a little organization to their Cyber Safety. Aside from being able to save all the passwords you create, it can also give password recommendations if you are creating a new account.
Download antivirus software
Antivirus software can help if a password hacker ever tries to install malicious spyware or keyloggers onto your device. If the security software detects a threat, it can diagnose and attempt to remove the virus.
Now that you know the types of password attacks and how to avoid them, the next step in your cybersecurity journey may be learning how to create a hack-proof password on your own. Regardless, with these skills at your disposal, your passwords could potentially help protect against any password attack that comes your way.

Cyber threats have evolved, and so have we.
Norton 360™ with LifeLock™, all-in-one, comprehensive protection against viruses, malware, identity theft, online tracking and much, much more.
Try Norton 360 with Lifelock.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.





Want more?
Follow us for all the latest news, tips, and updates.