Identity theft: What is it, how it works, and common warning signs
Identity theft is a serious crime that can wreak havoc on your finances, credit score, and reputation. In this article, we'll break down how identity theft works, the different ways criminals steal your information, and common warning signs. Then, get Norton™ 360 with LifeLock™ Select to help protect against identity fraud and other online threats.

What is identity theft?
Identity theft is when someone steals your personally identifiable information and uses it without your permission to commit fraud. Criminals do this for a variety of reasons but it’s usually for economic gain, like opening a bank account or applying for credit.
Personally identifiable information includes your:
- Full name
- Home address
- Email address
- Online login and passwords
- Driver’s license number
- Passport number
- Social Security number
- Bank account details
Once thieves have enough of this information, they may impersonate you to open accounts in your name, steal from your existing bank accounts, or purchase goods or services using your details.
How identity theft works
Identity theft starts when an identity thief chooses their target. They then go about stealing their target’s personal information. When they steal enough, they can use it to open accounts, commit fraud, or impersonate their victim in other ways for financial gain.
ID theft can take place in any number of ways, but here’s a sample journey:
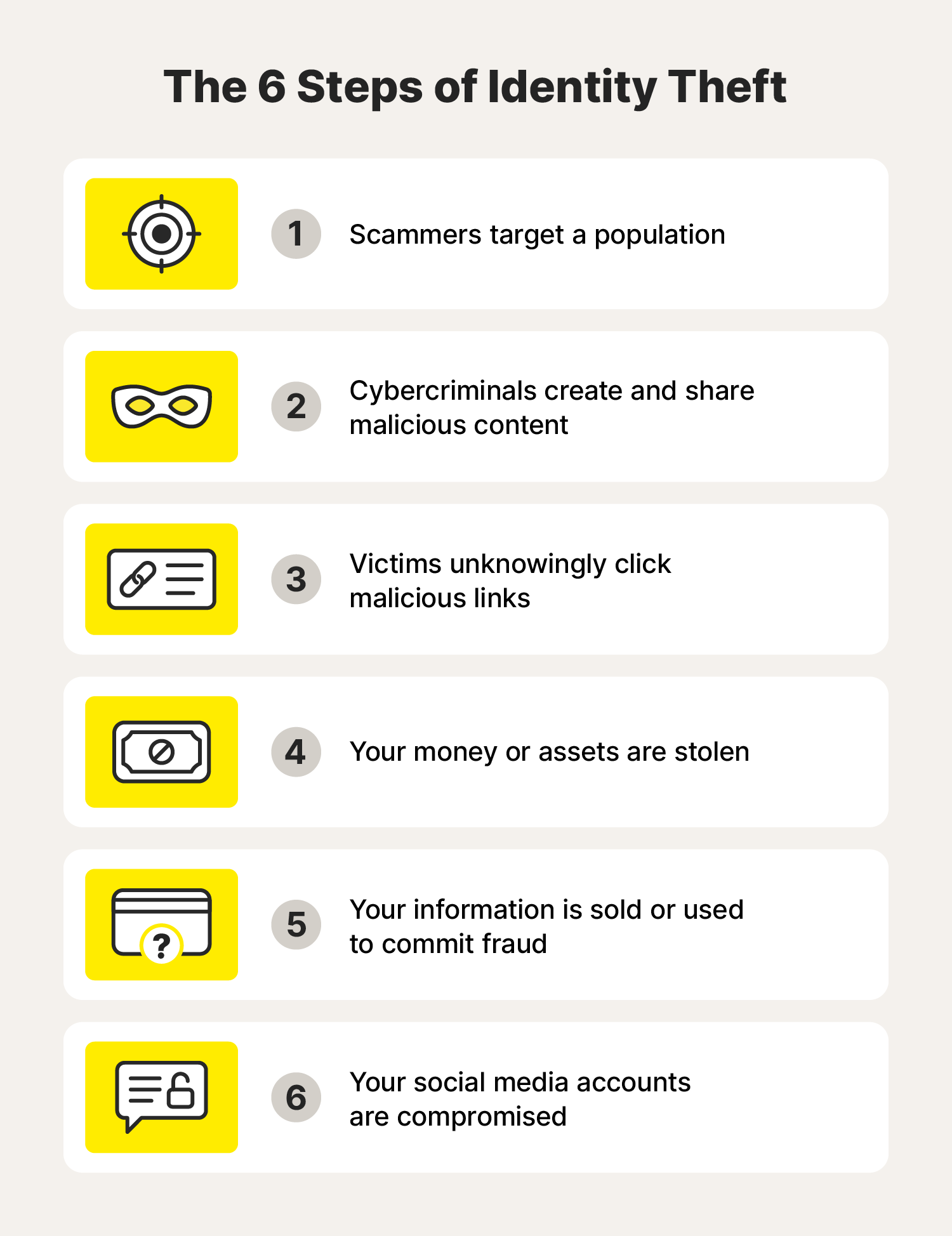
These steps can happen in a different order and some might vary. For example, you don’t have to click a link to have your identity stolen—perhaps you’re targeted with a vishing phone call or your social media account is hacked first.
There are many ways criminals can steal your information. Someone could physically steal something from you, like your bag with important documents and your wallet inside. But using our example above, here’s one way it could look, including some common practices used by ID thieves.
1. Scammers target an individual or group of people
An identity thief might gather a pool of potential victims. They could cast a wide net through large-scale data breaches or phishing emails.
Scammers can also take a more targeted approach. They might use information from social media profiles or public records to tailor their attacks to a specific individual. The process could even begin by chance if a thief steals or finds a wallet full of personal information and bank cards.
2. Cybercriminals create and share malicious content
Once they have a target set, cybercriminals could create and share malicious content to steal more personal information. This could involve creating fake websites that look like real login pages for banks or social media platforms. They could then send phishing emails linking to these malicious websites.
3. Victims unknowingly click malicious links
If victims click malicious links and enter their personal details, the identity thief can now impersonate them. Clicking these links could also download malware onto victims’ devices. Cybercriminals can design malware to steal passwords, browsing history, or personal information stored on a device.
4. Your money or assets are stolen
When cyberthieves steal information, they have various options for how to then steal money or other financial assets. They might use your credit card details to make unauthorized purchases. Financial assets like your bank account could be their goal, too.
5. Your information is sold or used to commit more fraud
Even after the original ID thief has got what they wanted they might sell your data to other criminals. The new ID thief could go on to file fraudulent tax returns, obtain medical services in your name, and so on. The consequences can be far-reaching, damaging your credit score, leading to debt collection issues, and causing a bureaucratic nightmare untangling the fraudulent activity.
6. Your social media accounts are compromised
Once the scammers can’t get anything else from you, they could move on to your contacts if they have access to your social media accounts. They could use your compromised account to launch social media scams by pretending to be you to your friends and family. And so the process begins again for the new targets.
Types of identity theft
Criminals have different objectives when it comes to ID theft, although the motive is normally financial. Here are some common types of identity theft:
Financial identity theft
Financial identity theft is when someone steals your credit card information, bank account numbers, or other financial data to make unauthorized purchases or open new accounts in your name. This can have a devastating impact on your credit score and financial well-being.
Example: You receive a bill for a credit card you never opened.
Not only are you responsible for disputing the charges, but you must also take steps to close the fraudulent account and avoid future issues.
Social Security number identity theft
An identity thief could use your Social Security number to get government benefits, medical care, open fraudulent accounts, or even apply for a job while posing as you. This can cause significant delays and problems down the line.
Example: You receive a phone bill for an account you didn’t open.
If a criminal has your Social Security number along with other crucial personal information, they could do a lot of damage.
Medical identity theft
This is when cybercriminals use your name and insurance information to receive medical services. This can lead to inaccurate medical records and difficulty getting the necessary care. Incorrect medical history also can lead to misdiagnosis or even improper treatment.
Example: You receive a bill for a medical procedure you never had.
Medical identity theft can be serious, especially if you require regular healthcare appointments.
Synthetic identity theft
Synthetic identity theft happens when someone combines real and fake information to create a completely new identity as the basis of their fraudulent activity. By blending this info, the criminal can use the new fake identity to take loans out or commit other fraud.
Example: You discover a loan application in your name with a different birthdate and other details that don’t match.
Synthetic identities are hard to detect since they blend real and fake data.
Causes of ID theft
There are a variety of ways an identity thief can steal your identity. There are physical methods like stealing your wallet or documents with personal info from your trash.
There are also cyber methods, like data breaches, phishing, skimming, Wi-Fi hacking, phone scams, and malware attacks.
You probably have a good understanding of how to keep your physical wallet safe and not to leave it lying around. The same goes for your mail and how to dispose of it safely.
But, online threats can be trickier to detect and stay on top of. By understanding how cybercriminals operate, you can take steps to help safeguard your online information and be alert for potential events that could lead to identity theft.
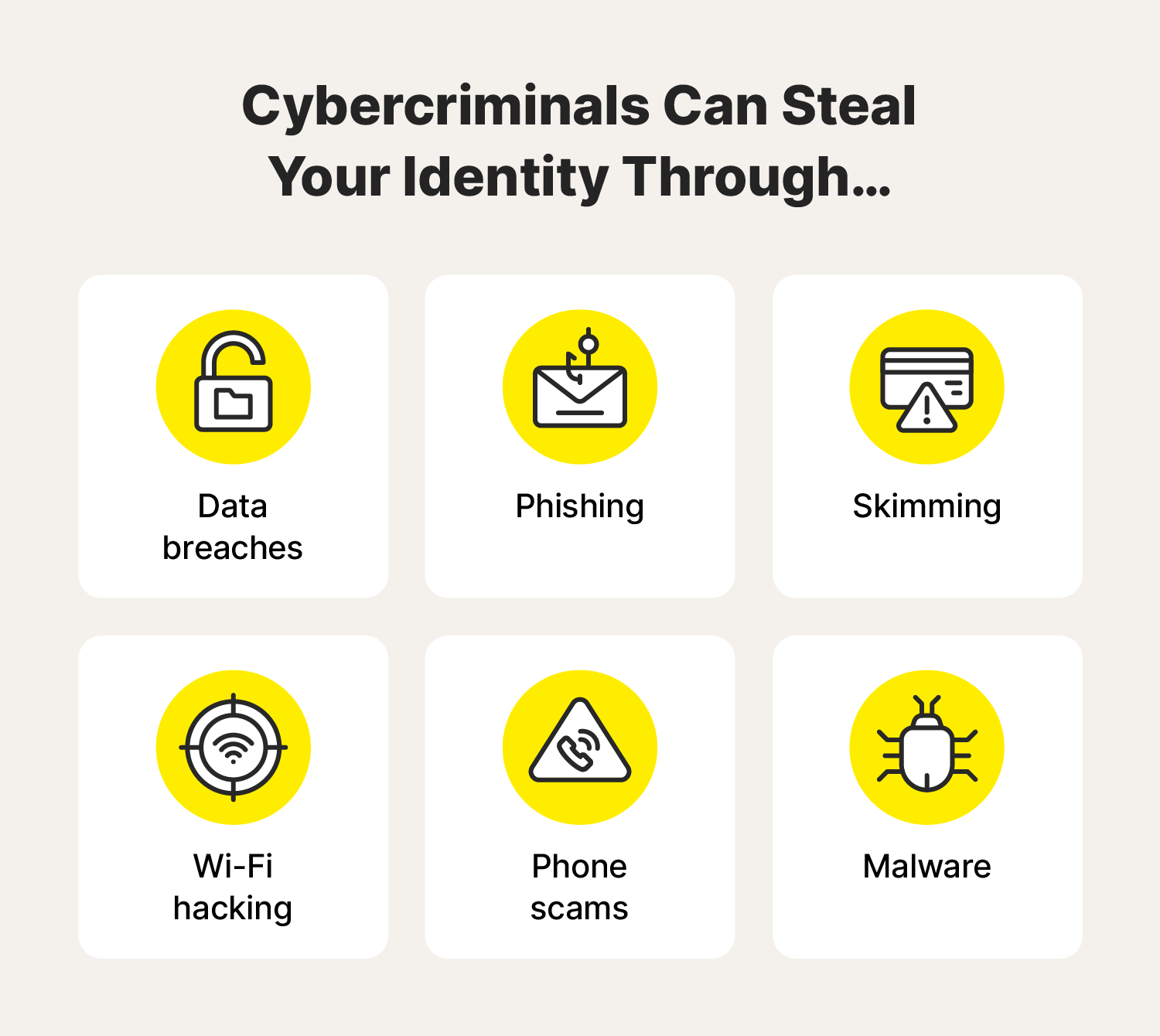
Data breaches
A data breach is a security incident where a criminal gains unauthorized access to sensitive information. If you find out that your info is caught up in a data breach, secure the account it was linked to by changing your password, then consider any knock-on effects that stolen info could have and take action.
Phishing
Phishing is when cybercriminals send fraudulent emails that look legitimate. They may include links that point to a fake website or malware download to get your data. Or the aim might be for you to respond to the message with personal details. Cybercriminals could use this information to commit identity theft or sell it on the dark web for others to use.
Avoid opening suspicious-looking emails or clicking unexpected links or attachments. And never hand over personal information, since any legitimate company won’t ever request this by email.
Skimming
Credit card or ATM card skimming happens when criminals replace card readers with counterfeit devices at point-of-sale systems in grocery stores, coffee shops, gas stations, and so on, or at ATMs.
These devices capture data stored on the magnetic strip of credit and debit cards. The information captured about the cardholder and account can be used for fraud.
Wi-Fi hacking
Some public Wi-Fi connections are unencrypted. This could allow hackers to snoop on data traveling to and from your device. Cybercriminals can also create fake Wi-Fi hotspots with names that sound like legitimate networks, in what is called an evil twin attack. Identity thieves may be able to view and exploit the information passing through the rogue network.
Always check the spelling of a network name before connecting. Plus, use a VPN to connect to public Wi-Fi.
Phone scams
In this variation of a phishing attack, fraudsters call you on the phone, claiming to be from a bank or a trusted organization. They’ll usually spoof the caller ID, so it looks convincing. If you get a call asking for personal info and you weren’t expecting it, hang up. Call the bank or organization directly to confirm whether it’s a phone scam and to warn them.
Look out for smishing scams too, where a con artist sends you a text message trying to get you to click a link or hand over personal details. Scammers may pretend it’s a delivery company contacting you, like in USPS scam texts. But there are also WhatsApp scams to look out for, which could be part of a wider romance scam. Be careful with texts you receive on any messaging platform as scammers target them all.
Malware
Criminals can sneak malware on your device using different tactics. Some types of malware allow a fraudster to access the information stored on your device, including:
- Viruses: Malicious software that replicates itself and spreads from device to device, and can steal personal info or corrupt or delete files.
- Spyware: Software that secretly monitors your computer activity and steals personal information, such as keyloggers which record every keystroke you type.
- Trojans: Programs disguised to look legitimate that trick you into installing them, often hiding malicious code that can steal information or damage your device.
Warning signs of identity theft
ID theft warning signs can include:
- Unexplained financial activity: Charges, accounts, or withdrawals on your bank statements or credit card reports that you don't recognize.
- Unexpected calls from debt collectors: Phone calls from collection agencies about debts you aren’t aware of.
- Missing mail or bills: Important documents you were expecting never arrived, especially those containing financial information.
- Errors on credit reports: Inaccuracies on your credit report, such as accounts you haven't opened, inquiries you didn't initiate, or incorrect personal information.
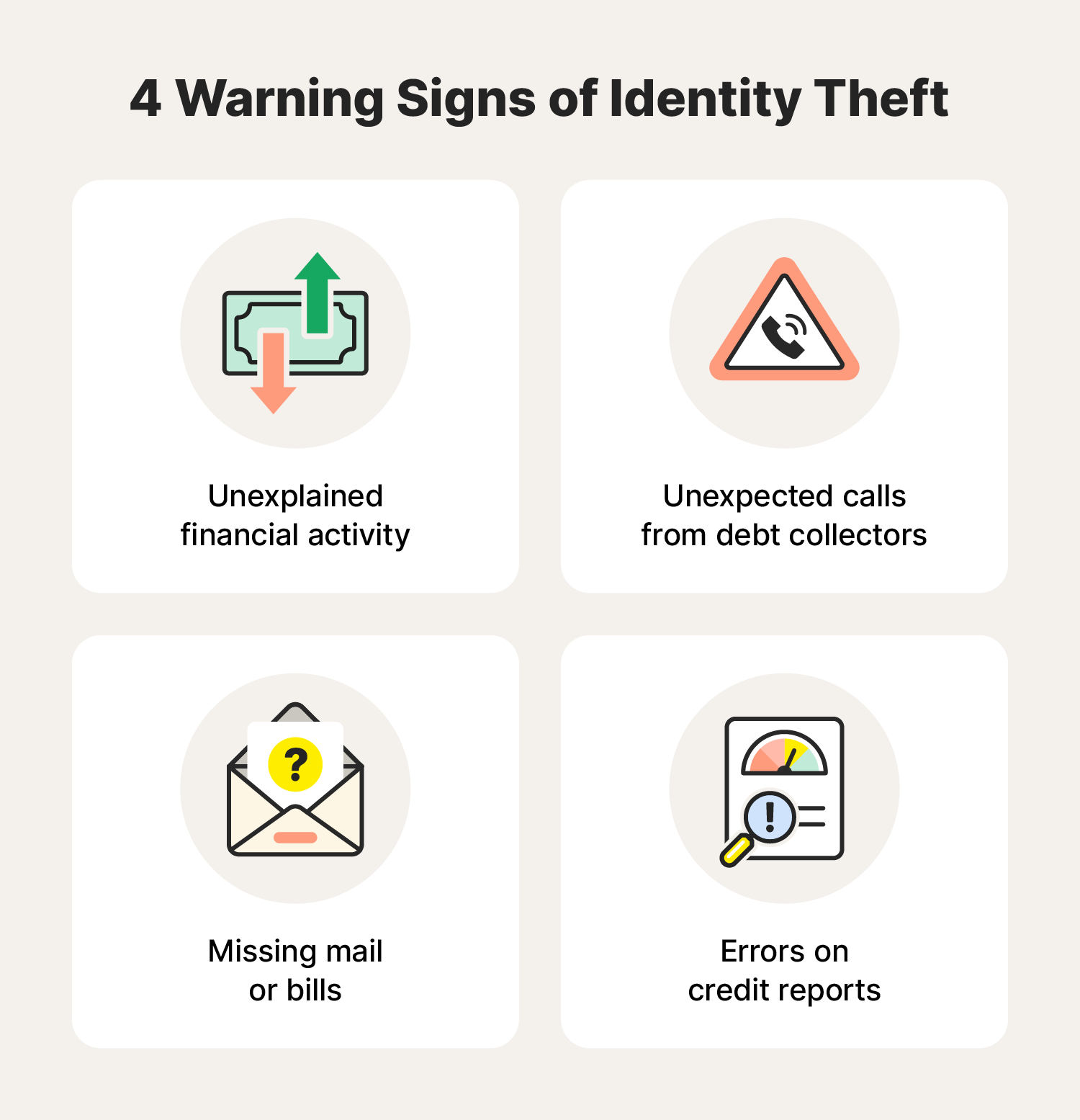
These are four common red flags of identity theft to look out for. And now that you know what identity theft may look like, here are the steps to take if you know or suspect you’re a victim.
What to do if you're a victim of identity theft
If you’re a victim of ID theft, you need to mitigate damage quickly. Here are the immediate steps you should take to report identity theft.
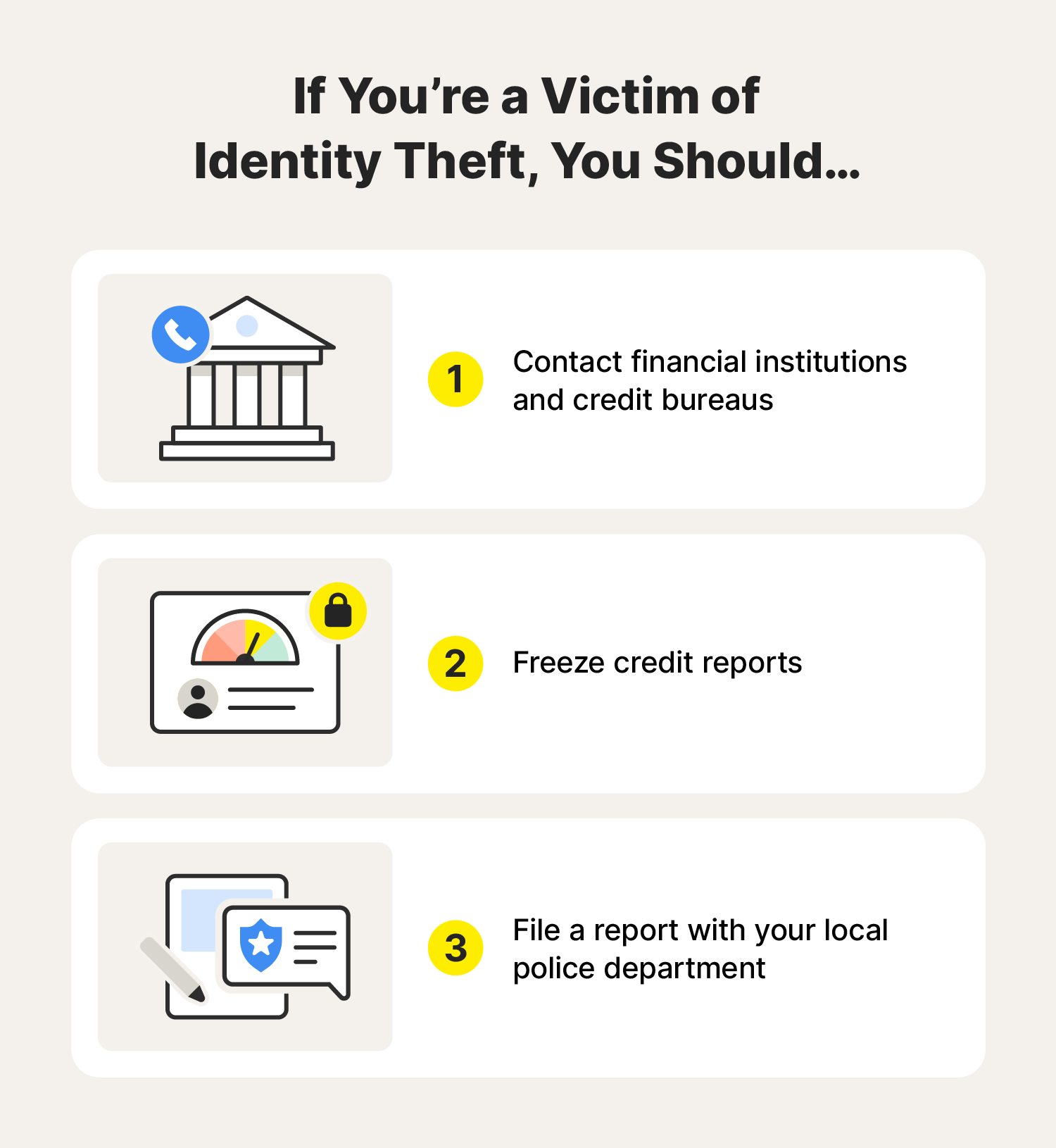
If you’re a victim of identity theft, here's what you should do immediately:
- Contact financial institutions and companies where the fraud occurred: Alert your bank, credit card companies, and other financial institutions about the identity theft. Also, contact the companies where the fraud occurred.
- Freeze credit reports: Contact the three major credit bureaus (Equifax®, Experian®, and TransUnion®) to freeze your credit report. This can help prevent criminals from opening new lines of credit in your name. You can also place a fraud alert on your report by contacting any of the major bureaus who must then alert the others.
- File a report with law enforcement: Report the identity theft to the FTC at IdentityTheft.gov to get your personal recovery plan or file a police report. You will need proof of one of these if you want to go on to place an extended fraud alert, which lasts seven years.
Ways to protect your identity
There are several ways that you can help protect your identity from would-be thieves. Here are the key strategies for safeguarding your personal information and helping protect against identity fraud occurring in the first place:
- Strengthen passwords and PINs: Use complex and unique passwords for all your online accounts. Avoid using obvious information like birthdays or pet names. Consider a password manager to help you create and manage strong passwords. Turn on two-factor authentication or multi-factor authentication wherever possible.
- Be cautious with personal information online: Don't share sensitive information like credit card details on unsecured websites or in response to unsolicited emails or messages. And think before sharing anything on social media or online, as even seemingly innocent info like your place of birth can be used by identity thieves.
- Monitor financial accounts regularly: Regularly review your bank statements and credit card reports for any unauthorized activity. Catching fraudulent charges early can minimize the damage. You can also use a service like Norton™ 360 with LifeLock™ Select to help monitor your credit.
- Shred sensitive documents: Before discarding documents containing personal information like bank statements or credit card offers, shred them thoroughly and dispose of them in separate loads. This makes it much harder for criminals to steal your information from the trash.
- Secure personal devices and networks: Use a strong password on your home network and keep your devices' software updated so they have the latest security patches. Be cautious when using public Wi-Fi networks and avoid accessing or sending sensitive information on unsecured connections.
- Be skeptical of unsolicited communications: Be wary of emails, texts, or phone calls you’re not expecting that request personal information. Don't click suspicious links or attachments, and if you’re unsure about a communication's legitimacy contact the sender directly through a verified channel.
By following these steps and staying vigilant, you can reduce your risk of identity theft and help protect your personal information.
Mitigate your risk of identity theft
Identity fraud is a serious problem. The tools and services built into Norton™ 360 with LifeLock™ Select will help protect your personal information and online privacy. Get Norton™ 360 with LifeLock™ Select today for powerful protection against identity theft and other online threats.
FAQs about identity theft
Still have questions about identity theft? We’ve got you covered.
What should I do if I suspect I'm a victim of identity theft?
If you suspect that somebody stole your identity, alert your bank and credit card companies immediately. You should also place a fraud alert or credit freeze on your credit report and notify the authorities that you think your identity has been compromised.
What do you do if someone has stolen your identity?
Contact the company where you know the fraud took place and speak to the fraud department. Ask them to freeze your account or implement their fraud procedures. Then place a fraud alert or credit freeze on your credit report and file a report at IdentityTheft.gov and with your local law enforcement office. If the theft warrants it, consider contacting the IRS as well as your insurance and medical care providers.
Can children be victims of identity theft?
Yes, child identity theft exists. If an ID thief knows your child’s Social Security number, they might use it to open new credit accounts or take out bank loans—and hurt your child’s credit score in the process.
Is identity theft punishable by law?
Absolutely, identity theft is a serious crime with significant consequences for the perpetrators. The penalties for identity theft vary depending on the severity of the crime and the state where it occurs.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.







Want more?
Follow us for all the latest news, tips, and updates.