6 common types of ransomware you need to know about
Hackers use ransomware programs like CryptoLocker and WannaCry to hold computer systems hostage until they get paid. Learn about the most common types of ransomware and how to help protect yourself with safe browsing habits and security software like Norton 360 Deluxe.

Ransomware is a form of malware that can lock and encrypt your computer or data. In some cases, it can even wipe the computer completely, permanently deleting important, irreplaceable files. With so much power in their hands, cybercriminals can then ask the owner to pay an exorbitant fee to restore access.
Cybercriminals use several techniques to install ransomware strains on their targets’ devices. Some of these include:
- Manipulating remote desktop protocols (RDP)
- Creating malicious URLs, aka fake websites
- Placing malware-infested ads on legitimate websites
- Tricking device users with drive-by downloads
- Sending targets infected email attachments
New ransomware variants are constantly emerging, making it more important than ever to understand the dangers of these malicious programs.
Here are the top ransomware types hackers currently use.
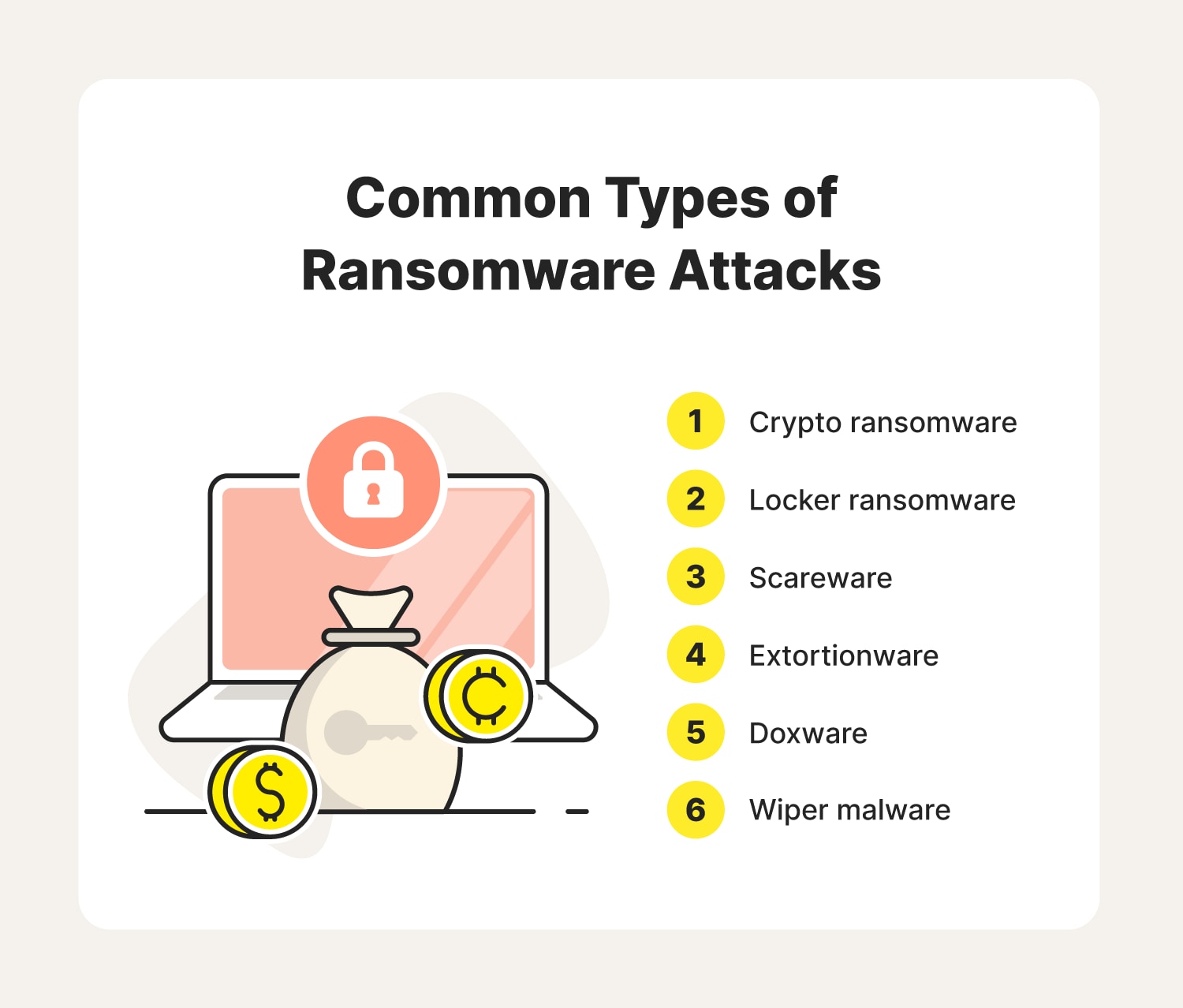
1. Crypto-ransomware
- Systems affected: Microsoft Windows
- Software used: Hive, REvil, Ryuk
Crypto-ransomware is a type of malware that restricts access to a computer until the owner pays the hacker a ransom. Usually, hackers carry out these attacks by emailing infected attachments to their target. Once opened, the malware encrypts the target's files.
In crypto-ransomware:
- The hacker often asks the target to pay them with cryptocurrency like Bitcoin to make the transaction more difficult to trace.
- Once paid, the hacker provides instructions on accessing the decryption key, enabling the owner to recover their files.
However, it’s important to remember that there’s no guarantee that they will share the correct key or that they won’t reinfect your device in the future if you do choose to pay. That’s why the U.S. government says not to cave into the hacker’s demands.
Instead, explore your recovery options with local law enforcement or the FBI to access your data without paying for the decryption key.
2. Locker ransomware
- Systems affected: Microsoft Windows
- Software used: CryptoLocker and Locky
Locker ransomware kicks the owner out of their device completely rather than just encrypting files. Typically, cybercriminals gain access to the owner’s system by convincing them to download malware using social engineering tactics.
In locker ransomware:
- The hacker typically disables all computer functions aside from the mouse and keyboard. By allowing their target to continue using those tools, they ensure they can adequately use their keyboard to send the requested payment.
In these attacks, the most important thing you can do is disconnect the device from your Wi-Fi network. This can help prevent the ransomware from infecting other connected devices.
3. Scareware
- Systems affected: Android, macOS, and Microsoft Windows
- Software used: Mac Defender and WinFixer
The primary purpose of scareware is to trick the device’s owner into hurriedly downloading a product or service to resolve the issue. This is what actually gives cybercriminals access to your device.
In scareware attacks:
- Unsuspecting internet users sometimes unknowingly open a spoofed website, which can automatically trigger a scare tactic, usually with alarming language via deceptive website pop-ups or device security scan results.
In most cases, the pop-up itself doesn’t hurt your computer or enable a hacker to steal information. If a pop-up shows up on your display, chances are you can simply click the “X,” clear your browser history, and restart your computer. However, if you’re still worried that you might have malware on your device, you can run a security scan for some peace of mind.
4. Extortionware
- Systems affected: Linux, macOS, Microsoft Windows, and some IoT devices
- Software used: EvilQuest and REvil
Extortionware is a type of ransomware where the attacker locks down their target’s device but also threatens to leak private information unless they pay the ransom. Once the extortionware is on the device, they can leverage any information stored against you.
In extortionware attacks:
- Hackers generally raid the devices they infiltrate to find company secrets and private data about individuals they can use as leverage to extort money from their target.
Try not to panic when facing the threat of doxxing or a data leak. Instead, slow down and report the incident to law enforcement to get more information about your options.
5. Doxware
- Systems affected: Android, cloud services, iOS, IoT devices, Linux, macOS, and Microsoft Windows
- Software used: DoppelPaymer and REvil
Slightly more serious than your run-of-the-mill ransomware, doxxing malware doesn’t just encrypt files, documents, and applications. Hackers using doxware also threaten to release proprietary data or personal identifying information about their targets, exposing them to identity theft and sometimes physical harm.
In doxware attacks:
- Hackers may threaten businesses or individuals.
- Repercussions are often more extreme than standard doxxing because hackers can also leverage the confidential information they find on your device.
If your device is overrun with doxware, turn it off and talk to an IT professional for advice on removing it.
6. Wiper malware
- Systems affected: Cloud services, Linux, Microsoft Windows, and macOS
- Software used: Jigsaw, NotPetya, and KillDisk
Wiper malware doesn’t just restrict the user’s access. It threatens to destroy any files it infects. Often leveraged against businesses, this type of attack can potentially stop business operations in their tracks.
- Wiper malware inflicts the greatest amount of damage, and many perpetrators never even demand a ransom. However, if they do, it’s generally run using time-based triggers.
After a wiper malware attack, check to see if you have a recent data backup to restore the infected files.
Ransomware viruses that have enabled cyberattacks in the past
Understanding the history of ransomware attacks and their impact on cybersecurity is the first step in defending against future threats. Within each ransomware category are unique strains that hackers have used to carry out attacks that crippled individuals and businesses.
Here are the most common ransomware strains, their operational statuses, and their impact on the cybersecurity landscape.
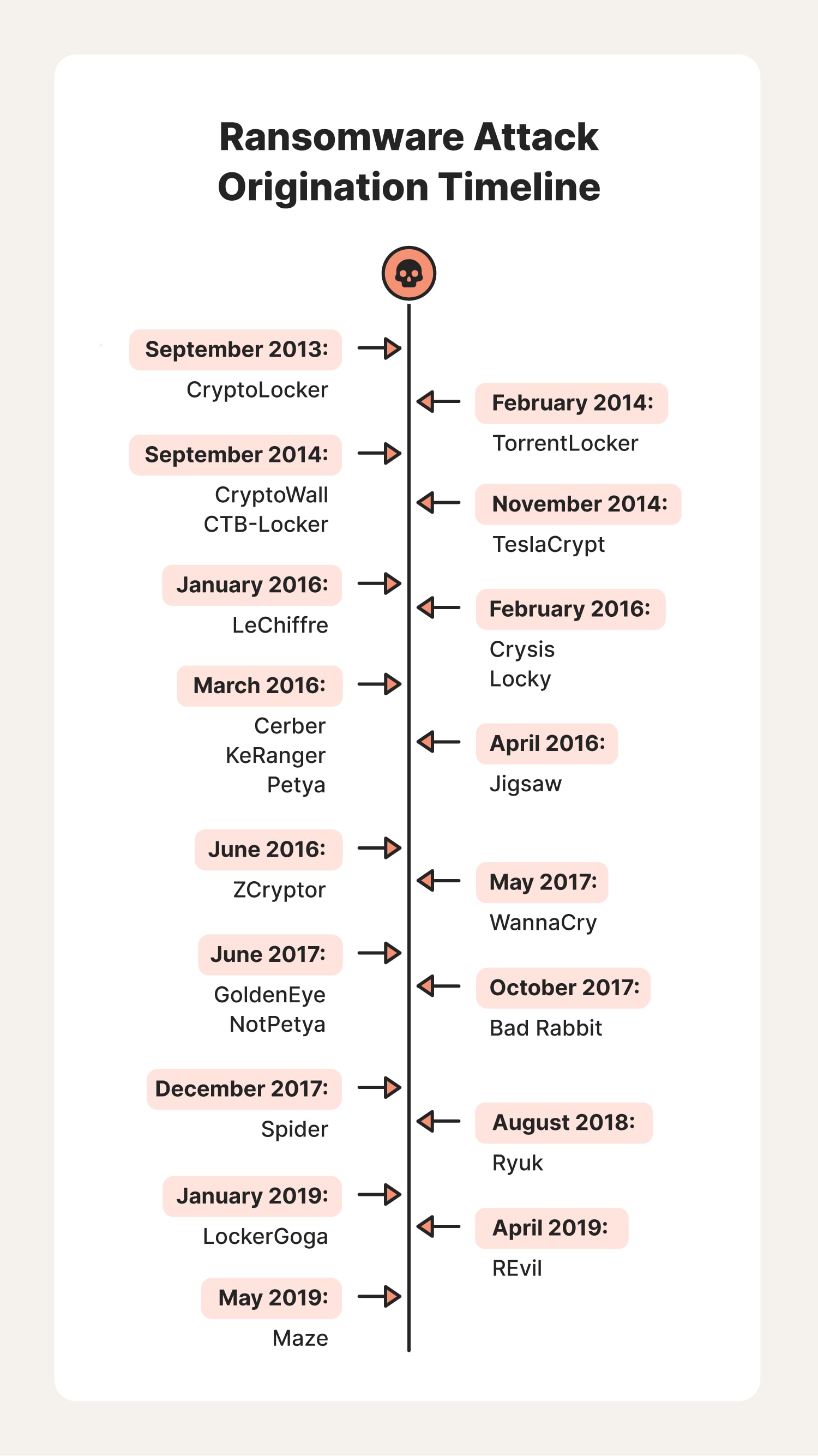
CryptoLocker
One of the early, infamous ransomware strains, CryptoLocker first became active around 2013. Hackers used the Gameover Zeus botnet to distribute CryptoLocker ransomware to encrypt files on their target’s device and demand payment in Bitcoin. The initial attack against Windows computers continued for a year before law agencies from the U.S. and other countries targeted it during Operation Tovar.
The first strain of CryptoLocker is no longer a threat, but several new versions of the malware strain are circulating online today.
TorrentLocker
TorrentLocker is a type of locker ransomware attack that has gained attention in recent years. It uses spam emails as its attack vector and has seen five major modifications since 2014.
These modifications have allowed TorrentLocker to adapt to many decryption techniques victims use to get their information back on their own. This adaptiveness has caused people to know this virus as an incredibly difficult ransomware to beat without paying the ransom.
CryptoWall
CryptoWall is a locker ransomware program that emerged in 2014. Since then, there have been several new iterations, making it one of the stealthier types of ransomware.
The virus uses a Trojan to hide within .zip files and other email attachments to make its way onto your devices. Many unwitting victims opened these attachments after mistaking them for safe documents like bills and invoices. Once installed, the CryptoWall virus found Java vulnerabilities to encrypt and withhold data. And just like other types of ransomware, payment is required to restore access.
CTB-Locker
Infecting computers via malicious emails and downloads since mid-2014, CTB-Locker is a type of locker ransomware strain with the ability to encrypt several different kinds of files (.doc, .pdf, .jpg, etc.). These cybercriminals require payment in Bitcoins to decrypt the data they’re withholding, allowing the transaction to remain anonymous.
TeslaCrypt
Targeting video game users specifically, TeslaCrypt first attacked in 2014, seeking to infect gaming files such as game saves, recorded plays, and user profiles. It became significantly more widespread in 2015.
This crypto-ransomware operates like most other types of ransomware strains, infecting devices and locking valued data. However, it only seeks out files less than 268 MB in size. Using stolen data, these cyberthieves could demand up to $500 or more to re-configure user access.
LeChiffre
Created in 2016 and coming from the French noun “chiffrement,” meaning encryption, LeChiffre is a type of crypto-ransomware that has wreaked havoc across the world, from the U.S. all the way to India.
Different from most types of ransomware, LeChiffre ransomware must be manually run on the targeted system. Ransomware hackers can do this by scanning a network for computers with security vulnerabilities and remotely logging in to run and install the malicious software.
Crysis
Spotted back in March of 2016, this incredibly volatile crypto-ransomware finds its way onto your device by piggybacking on files shared via email or pretending to be an installer for a video game or other legitimate software.
Just as crypto-ransomware does, once installed, Crysis looks for personal files to encrypt so that the hacker can demand a ransom payment.
Locky
Seen throughout North America, Europe, and Asia, Locky ransomware spread through malicious email attachments and macros in documents in 2016.
One of the first major attacks reported was on a Los Angeles hospital, requiring them to hand over $17,000 to return highly confidential information. A string of additional heists ensued, targeting more healthcare institutions following that incident, but have ceased in recent years. The original iteration of Locky is out of commission, but hackers are still using other iterations of the program.
Cerber
Cerber is an active ransomware virus that can mass-target victims to lock and encrypt their data. So far, no free decryptors have worked on this type of ransomware, and its encryption continues to hold steadfastly.
The Cerber developers license the ransomware to help their affiliates carry out the time-consuming process of a ransomware hack. Once the attacker receives payment for the ransom, they split the profits made with the ransomware developer to compensate them for using their program.
KeRanger
KeRanger is a crypto-ransomware variant discovered in 2016 that poses a threat to macOS users.
Some KeRanger attacks use a remote desktop protocol software to infect several personal devices. The developer had access to a Mac Developer certificate, allowing them to bypass Apple’s Gatekeeper protection, a security feature protecting Apple products from these cyberattacks.
Petya
First seen in an attack executed in 2016, Petya is a type of crypto-ransomware virus targeting Windows servers, laptops, and PCs in particular. To work, the target must first open and download an infected file, allowing the hacker to take control of the device.
Petya attacks crippled personal and corporate systems around the world, and it is seen as one of the most widely feared ransomware strains out of all the variants.
Jigsaw
Named after a horrifying character appearing in the popular horror film franchise Saw, Jigsaw is one of the first locker ransomware variants to carry out its threat to delete files until the cybercriminal receives their payment. In this case, the ransomware deleted files every 60 minutes and when the program rebooted.
The software emerged in 2016 and begins by requiring a $150 payment within the first hour of infection or the destruction of one file ensues. If the victim doesn’t pay before time runs out, the hacker resets the clock and threatens to delete an even greater number of files.
ZCryptor
ZCryptor, which gained traction in 2017, is a notable hybrid ransomware strain that blurs the lines between ransomware and crypto worms. Combining elements of both, ZCryptor is categorized as a ransomware-crypto worm hybrid.
Unlike traditional ransomware, ZCryptor utilizes the attributes of a crypto worm, allowing it to infiltrate various computer systems and propagate to interconnected devices without relying on the conventional delivery method of malware-laden phishing emails or corrupted attachments. To gain access to your system and network, ZCryptor often masquerades as a seemingly legitimate software installer, mirroring a tactic used by the infamous Crysis ransomware.
WannaCry
WannaCry is a notorious ransomware strain that made waves in 2017 after exploiting a vulnerability on Windows computers. It was a large-scale crypto-ransomware attack that compromised nearly a quarter-million machines internationally.
After exploiting the vulnerability, WannaCry’s first high-profile attack was on the Spanish telecommunications company Telefonica. In this case, WannaCry quickly encrypted critical data and held it hostage, demanding that the company pay a cryptocurrency ransom.
GoldenEye
Seen mostly in ransomware attacks carried out in Germany, GoldenEye is a locker ransomware variant first noticed in June of 2017 and spread via phishing emails like other known types of ransomware. In addition to encrypting files to hide data from the owner, it can also revoke essential computer functions to bring the user to a complete standstill.
NotPetya
As you might have guessed, NotPetya is, well, not Petya ransomware. But it was derived from it. NotPetya is different because it uses improved encryption keys, reboot styles, and displays previously used on Petya. This virus can also spread through a computer independently without the device owner opening a malicious link or attachment.
Devious hackers use this more advanced ransomware strain to bypass the enhanced security measures created following the devastating Petya cyberattacks.
Bad Rabbit
Appearing in 2017, Bad Rabbit ransomware has infected devices worldwide.
Distributed via a fake Adobe Flash update on corrupt websites; this locker ransomware virus can instantly compromise data. Once infected, the program directs users to a payment window demanding Bitcoin as ransom. This payment method allows the identity of the cybercriminal to remain anonymous.
Spider
Spider ransomware was first discovered by Netskope in 2017 and distributed by hackers using phishing campaigns. As a crypto-ransomware, it gives victims a 96-hour window to submit a Bitcoin payment set by the attacker. An added layer of security equipped Spider with security measures that will destroy files if the victim tries to retrieve them on their own. Failure to pay could destroy your data or computer operating system.
Ryuk
This ransomware targeted enterprises and was often deployed after an initial TrickBot (Trojan) infection. Ryuk is one of the most financially detrimental crypto-ransomware strains. It first appeared in late 2018 and is estimated to have defrauded victims of more than $150 million after extorting local governments and large organizations.
Created by a group called CryptoTech, this variant can encrypt and delete original documents and store shadow copies saved onto the computer system’s hard drive.
LockerGoga
This locker ransomware virus was first detected after an attack on Norsk Hydro, a Norwegian renewable energy company, in 2019, and it infected thousands of computers internationally. It works just as other ransomware strains do, using phishing emails to corrupt personal and corporate devices and demanding a ransom to make a profit.
REvil
Known by some as Sodinokibi, REvil gained notoriety for attacking high-profile targets and demanding substantial ransoms. Primarily an extortion ransomware-as-a-service (RaaS), it would threaten to release private information about targets on their “Happy Blog” unless they paid.
The original Russian ransomware program was active from 2019 until 2022, when its members were arrested. However, there have been reports that REvil is back.
Maze
Maze is a complex crypto-ransomware, targeting companies and organizations across the globe since May 2019. Previously identified as ChaCha ransomware, hackers demand a cryptocurrency payment for them to return stolen files.
If a cybercriminal doesn’t receive a payment, they will leak confidential documents and files on the web for the public to see.
Ransomware prevention tips
Having a fear of your computer and devices falling victim to a ransomware attack is a legitimate concern. Here are some things you can do to protect yourself and your data:
1. Back up your data regularly so you can restore your system in the event of an attack without paying the ransom.
2. Install reliable antivirus with ransomware protection software to alert you when software updates are available and when it detects suspicious websites or files.
3. Only approve downloads from secure websites to avoid triggering a ransomware download.
4. Keep your operating system and security software software up to date to patch system vulnerabilities and strengthen your device’s defenses against hackers.
5. Never click on suspicious email attachments or links to avoid downloading ransomware.
6. Interact with pop-ups cautiously to close them without clicking and installing ransomware on your device.
7. Use public Wi-Fi networks sparingly to limit the time you expose your device to easy-to-intercept networks.
8. Utilize a VPN to encrypt your internet connection and prevent cybercriminals from attacking you on unsecured networks.
9. Never use data storage devices from unknown sources to reduce the chances your data will be corrupted.
10. Monitor your network to identify unauthorized devices and suspicious activity before your devices are infected.
As new types of ransomware arise almost every day, it’s important to know how to protect your data, privacy, and networks from these dangerous cyberattacks. Use what you’ve learned here to create a cyber-safe environment for yourself and your loved ones.
Tips for recovering from a ransomware attack
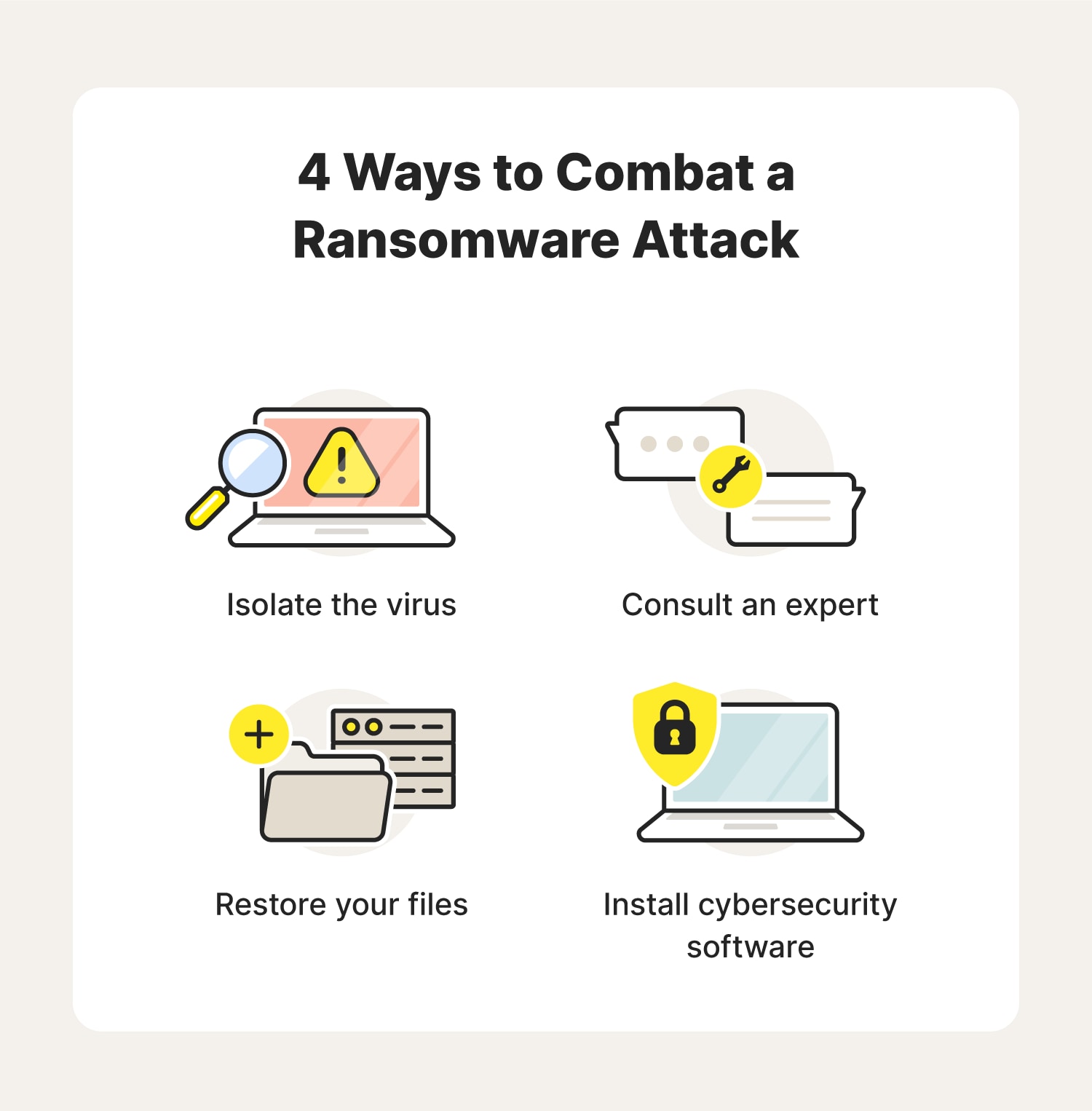
Recovering from a ransomware attack can be complex and challenging. Here are some tips to help you successfully navigate the recovery process:
- Isolate the virus: As soon as you realize your device got infected, disconnect it from your Wi-Fi network to prevent it from spreading to other connected devices.
- Consult an expert: Take your device to an IT expert to determine the extent of the damage and get more information about your options. You should also report the crime to local law enforcement. They may have someone on staff who can help you.
- Restore your files: Ideally, your computer will have clean backups of important files. Check to see if there’s anything you can recover.
- Install cybersecurity software: Next, you should look at installing cybersecurity software like Norton 360 Deluxe to help identify and prevent future attacks. Tools like this include a firewall, a built-in VPN, suspicious activity monitoring, and cloud backup that can help you keep your private information safe.
The steps you take to return from a stressful situation like this may vary depending on your circumstances. Just try your best not to panic and wait until you have more information before deciding, as giving in to a hacker’s demands is generally ill-advised.
Cybersecurity software that evolves as fast as threats do
With ransomware and other types of cyberattacks a persistent scourge, it’s more important than ever to keep your private information locked down and to practice safe browsing. With tools that help keep your online activity private, prevent account takeovers, and provide real-time threat alerts, Norton 360 Deluxe can help protect you from viruses, ransomware, and other online threats.
FAQs about ransomware
Still have some questions about ransomware? Read along for answers to the most commonly asked questions on the subject.
What is RaaS?
In cybersecurity, RaaS stands for Ransomware as a Service. It’s a subscription-based business model for selling ransomware malware to an affiliate (cybercriminal), enabling them to attack their target.
Should I pay the ransom?
You should avoid paying ransoms because there’s no guarantee that the hackers will keep their promises and it could encourage them to target others.
Instead, consult the FBI’s Internet Crime Complaint Center, an IT expert, or a lawyer to talk about your options. They may have an alternative solution that enables you to get your information back without sending money. And even if there is no alternative, police may be able to trace the offender based on their instructions for payment.
How can a hacker install ransomware on my device without me knowing?
A hacker can install ransomware on your device without you knowing through email phishing or exploiting vulnerabilities in your operating system or software. Other times, they simply take advantage of human error or a lapse in regular security updates.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.







Want more?
Follow us for all the latest news, tips, and updates.