What is vishing? Tips to spot and avoid voice phishing scams
Vishing is a phone-based phishing tactic, and scammers have made it even more convincing due to AI voice tricks. Get more details on what vishing is and how to spot these calls before you share any information. To help avoid getting on the phone with a scammer in the first place, Norton 360 with LifeLock Select can automatically block or label scam calls before they reach you.

Voice phishing (vishing) scams are becoming more widespread and persuasive. According to a recent CrowdStrike report, vishing attacks surged by 442% in 2024, driven by scammers using polished scripts, real-time pressure, and even AI-generated voices to sound legitimate. And these sophisticated tactics are increasingly being deployed against everyday consumers.
Callers aim to sound believable enough to get you to share personal information, send money, or take action without double-checking. Learn about vishing so you can recognize these calls early and avoid getting caught up in the story.
What is vishing, and how does it work?
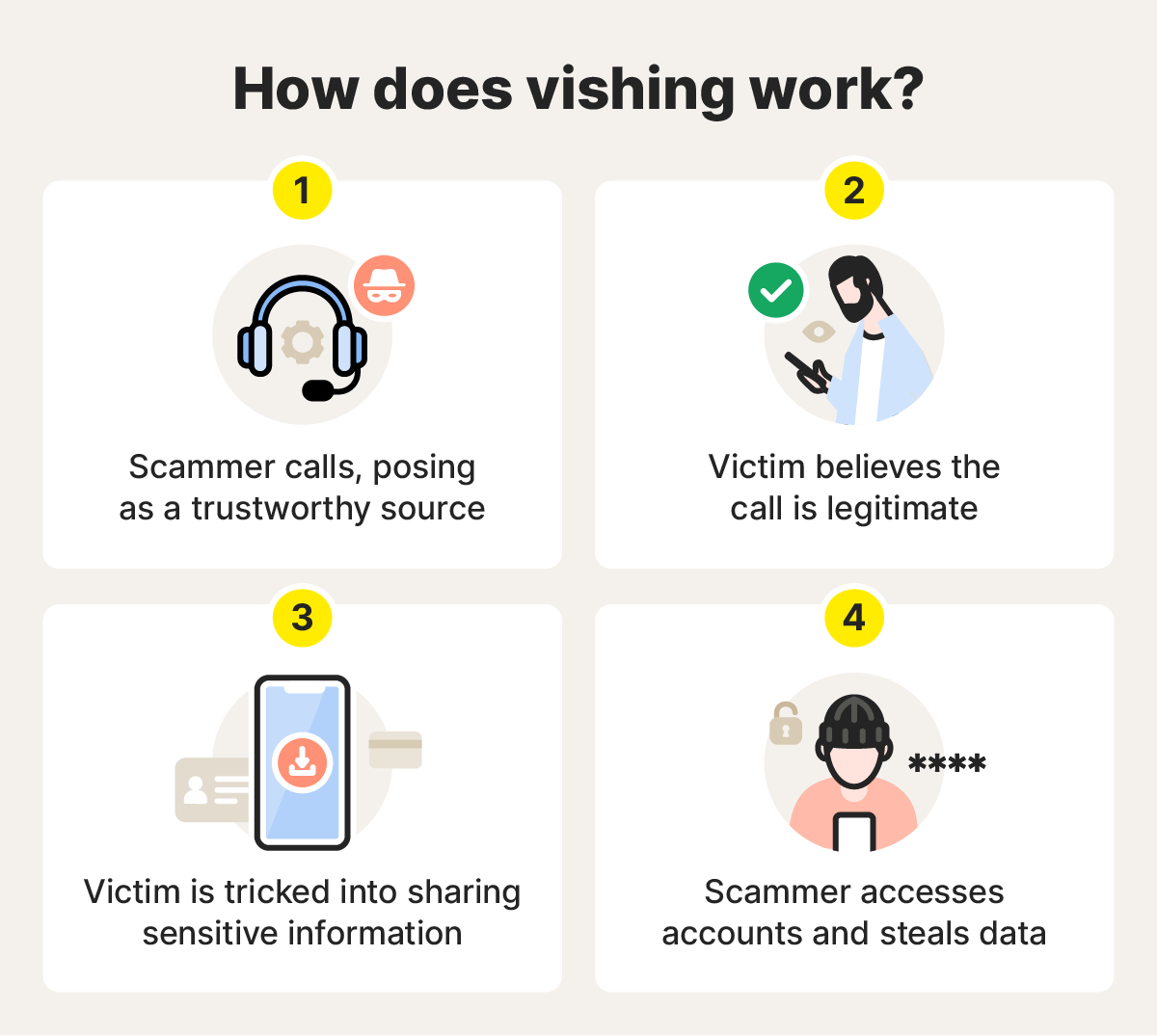
Vishing, short for “voice phishing,” is a phone-based cyberattack where cybercriminals exploit the phone as a tool for their schemes. During a vishing phone call, a scammer may try to get you to share personal information and financial details, such as bank account numbers and passwords.
Scammers usually pose as a trustworthy or authoritative source during a phone call. They may spoof the caller ID to appear legitimate or even use Voice over Internet Protocol (VoIP) technology to place hundreds of calls at a time for more widespread attacks.

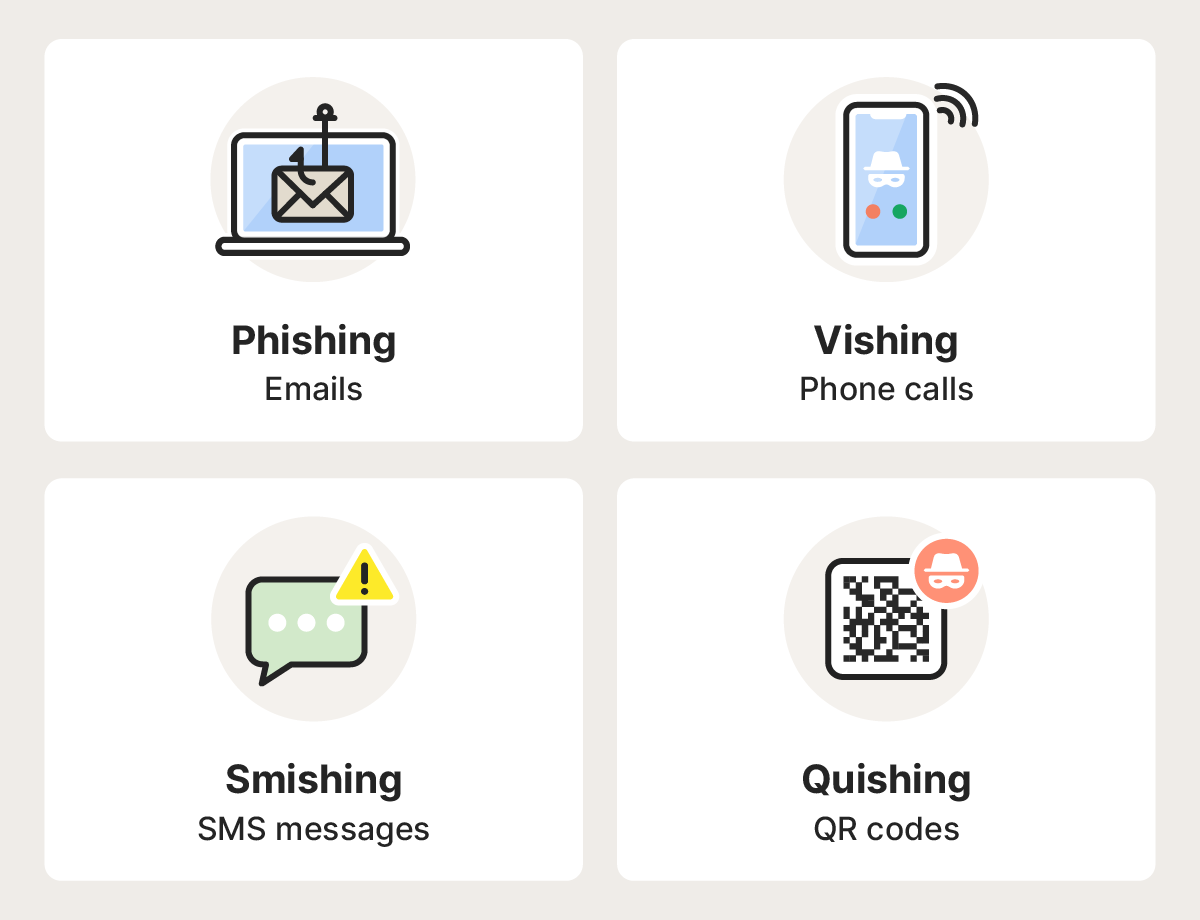
What’s the difference between phishing, vishing, and smishing?
Vishing and smishing are types of phishing, but they use different communication channels. Smishing scams are delivered through SMS text messages, while vishing scams happen through phone calls or voice messages.
Here are the differences in detail:
- Phishing: A cyberattack that uses fraudulent emails, texts, calls, or online messages to steal your data, gain access to account information (including logins), and monitor online activities. Attackers typically trick victims into clicking on malicious links or visiting fake websites.
- Vishing (voice phishing): A type of phishing carried out through phone calls. These calls may come from a live person or a pre-recorded robocall, but the goal is the same: to pressure or deceive you into sharing sensitive information or taking actions that compromise your data.
- Smishing (SMS phishing): A phishing attack delivered through text messages. While both smishing and vishing target phones, smishing relies on SMS or spam texts rather than voice calls to steal confidential information.
- Quishing: A type of phishing that uses malicious QR codes. Scammers create fake QR codes that lead to malicious websites designed to steal your information.

How to spot a vishing scam
Common signs of a vishing scam include urgency or fear-based pressure, unsolicited requests for sensitive information, and poor call quality. Understanding how vishing scams work can help you recognize these red flags quickly and stay in control during unexpected calls, making it easier to protect both your money and your personal information.
Here’s a closer look at warning signs to watch out for:
Unsolicited calls
Unsolicited calls you weren’t expecting are a classic vishing tactic. If something feels off, hang up, look up the official number, and call back directly. Most “urgent” calls claiming to come from government agencies — such as the Internal Revenue Service (IRS) and the Centers for Medicare & Medicaid Services — or large companies, turn out to be scams once you verify them.
Urgency and fear tactics
To pressure you into taking immediate action, scammers will use threats to create a sense of urgency. If you get one of these phone calls, remain calm and never give them any form of payment or personal information.
Requests for personal information
Anyone who calls out of the blue and asks you to confirm your Social Security number, bank account info, or other identifying details over the phone is likely a scammer. Never share confidential info on the phone unless you can confirm the source is who they say they are.
Background noise or poor audio quality
Pay attention to odd background noise or generally poor audio quality on phone calls. Subtle glitches, awkward pauses, or audio that doesn’t match the caller’s story can all be early signs that something’s wrong. Also, listen for unnatural or robotic-sounding voices, as it could be a robocall.
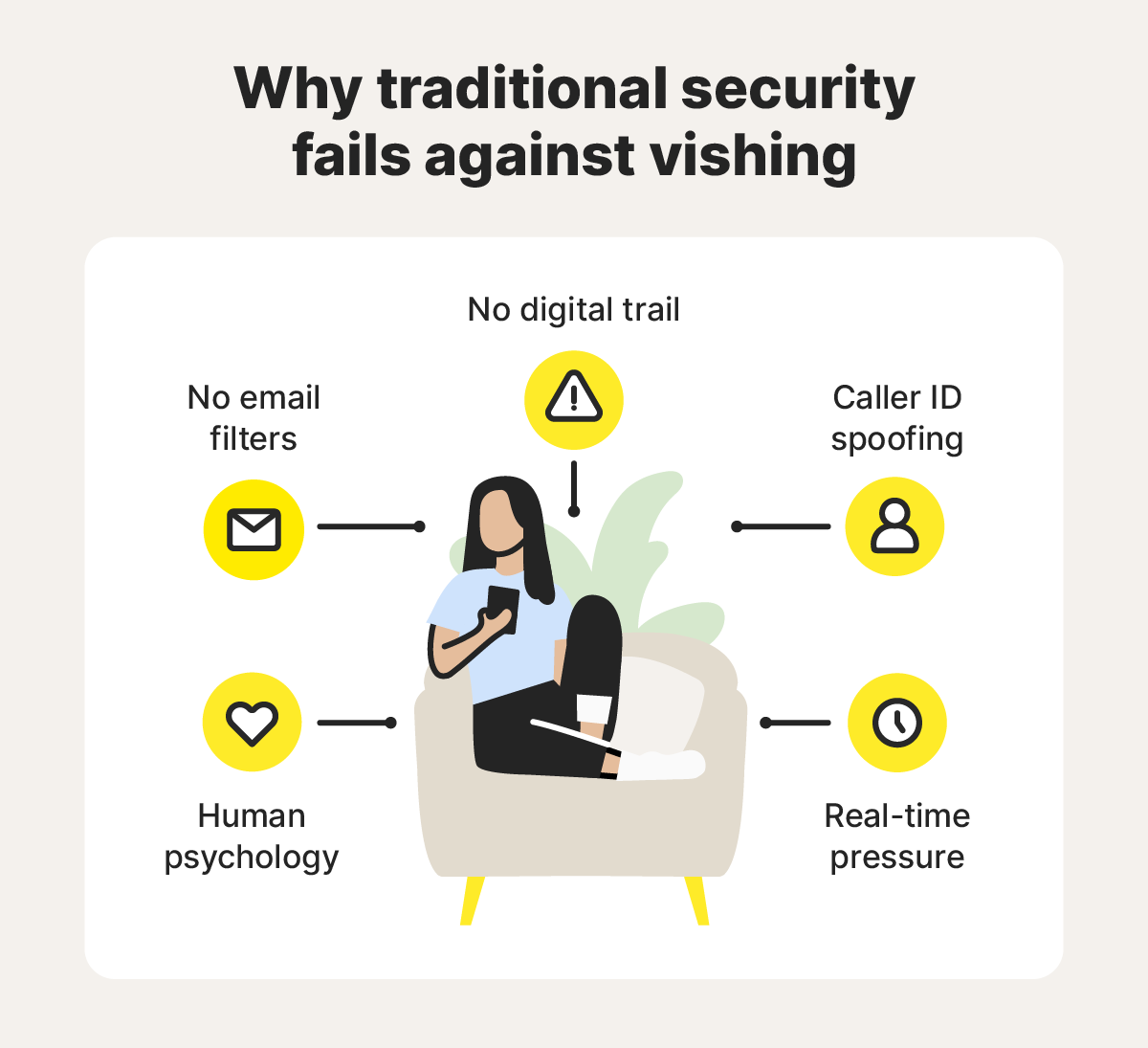
How vishing scams bypass detection
Rather than relying on a single trick, scammers combine technical tactics with psychological pressure to slip past your defenses.
Many vishing calls begin with caller ID spoofing, making the incoming call appear to come from your bank, local police, or a government agency. Automated dialing systems let scammers place thousands of calls at once, and because these interactions happen in real time, they often bypass the filters that catch suspicious emails or texts.
Once connected, vishers use natural-sounding scripts, casual small talk, or urgent warnings to put you off balance. These social engineering ploys closely mimic the tone and pacing of legitimate customer service teams, sounding credible just long enough to build trust.
By blending real company jargon with believable scenarios, vishers create calls that feel familiar and safe. Their goal is to extract enough personal information to commit identity theft or drain accounts before you realize what’s happening.
11 common examples of vishing scams
From bank impersonation to tech support fraud, vishing scams tend to take on a few common forms. Here are some vishing examples you're most likely to encounter.
1. Bank impersonation
A common vishing scam is when attackers pose as representatives from banks or financial institutions. Whether it’s a real person on the phone impersonating the bank or a prerecorded message, a scammer will often tell you there’s an issue with your account or a recent payment you made.
Using convincing scripts, they’ll trick you into sharing account details or PINs. They may even have you transfer funds to another account to fix the “problem.”
In one high-tech bank scam, scammers spoofed a journalist's bank phone number and called asking him to transfer money for security purposes. By the time he realized, his life savings ($30,000) were gone for good.
2. Tech support scams
This type of vishing scam frequently targets older adults (age 60+), as they are 398% more likely to fall victim to tech support scams than younger people, according to the Federal Trade Commission.
Scammers may pose as tech support personnel from large companies like Amazon, Microsoft, or AT&T. In this vishing scam example, the scammer could call you claiming to have detected a harmful virus on your phone or computer, or to alert you of an important software update.
From there, they’ll convince you to share your personal information or login credentials and even request remote access to your devices to solve the issue or install the update. In one Reddit post, a user described how their elderly neighbor saw a pop-up claiming their computer was locked, called the number displayed, and gave a scammer remote access to both their computer and phone.
3. Medicare or Social Security scams
Vishing scammers may pose as Medicare reps — often during Medicare open enrollment season — and try to glean financial info from you, such as your Medicare number or bank account details.
From there, the scammer will either fraudulently use your Medicare benefits or steal your money. Scammers may also claim to be from the Social Security Administration and threaten to suspend or cancel your Social Security number.
4. Government agency (IRS) impostors
Vishing attackers may impersonate government officials, issuing false warnings about unpaid taxes. The goal is to create panic, leading you to share sensitive information or make payments to resolve supposed problems.
There are many variations of this type of scam. Typically, you'll receive a prerecorded message about an issue with your tax return, and if you don't call back, they will issue a warrant for your arrest. Scammers usually pair this with a spoofed caller ID made to look like the call is coming from the IRS.
In one prosecution, a scammer was convicted for a tax-fraud scheme where hundreds of victims were targeted with impersonation calls claiming IRS debt. To avoid cases like this, be sure you know the signs of an IRS scam call versus an authentic call from the IRS.
5. Shipping or delivery scams
In shipping or delivery scams, callers pose as postal or courier service agents and claim there’s a “problem” with your package. They may cite a customs fee, an address issue, or the need to verify your identity before delivery can proceed. To sound routine, they often reference a well-known carrier such as USPS.
Once the setup is in place, they try to collect personal information or direct you to a fake payment link. These calls can feel convincing because package deliveries are so common—but legitimate couriers don’t call unexpectedly to request sensitive details.
One Reddit user described a caller who knew their name, phone number, and supposed order details (despite having made no recent purchase) and pressured them to provide payment information before the package could be “released.”
6. Investment or loan scams
In loan and investment scams, callers pitch low-interest loans, high-return investments, or “guaranteed” financial opportunities. They rely on polished scripts and high-pressure sales tactics to get you to commit quickly, often urging you to share banking details on the spot.
According to U.S. estimates, losses to online investment scams have exceeded $16.6 billion. In 2024 alone, Americans lost at least $10 billion to Southeast Asia-based operations — a 66% increase from 2023.
These numbers highlight just how widespread and convincing these schemes have become. The pressure is the giveaway. Legitimate lenders and financial advisors don’t rush decisions or demand immediate deposits. If an offer sounds like a shortcut to easy money, it’s usually a sign someone is trying to cash in on your trust.
7. Prize scams
With prize scams, the caller claims you’ve won something — a vacation, a gift card, or even a cash reward. However, to receive the prize, you’re told to verify your identity or pay a small processing or tax fee.
Scammers rely on excitement to cloud your judgment, hoping you’ll act before you think. But legitimate contests don’t require upfront payment or sensitive details. If your lucky “win” comes with strings attached, it’s almost always a setup.
In one recent case, a scammer was indicted for a phone-based lottery scheme that cost an elderly Washington victim over $800,000 through repeated “tax and fee” demands masquerading as prize collection.
8. Romance vishing scams
Romance scams start with trust. The caller pretends to be someone from a dating app, social network, or even a long-lost acquaintance. Once a connection is established, they pivot to personal requests, such as asking for money for an emergency, access to an account, or private details they can misuse later.
Because these calls lean heavily on emotion, they can feel more believable than typical scams. A sudden request for financial help or sensitive information is the clearest sign that the relationship isn’t what it seems.
One Reddit user shared how a scammer not only manipulated them emotionally but also managed to deceive their father with the same fabricated story.
9. Grandparent scams
In grandparent scams, callers pretend to be a grandchild or other relative claiming they’re in trouble and need help right away. They rely on urgency and fear to override skepticism. What makes this trick even harder to catch now is the use of AI-generated voices that can mimic real family members.
With just a short audio sample, attackers can create a voice clone that sounds close enough to spark panic. If a call leaves you rattled, take a breath, hang up, and check in with the family member via a different channel before taking action.
In one recent operation, scammers stole $5 million from 400 older adults in the U.S. by impersonating distressed grandchildren and demanding immediate payment.
10. Executive impersonation
Executive impersonation scams target employees by mimicking the tone, authority, and urgency of company leaders. The caller may claim there’s an unexpected payment to process, a confidential project underway, or a sensitive document they need access to right away.
Because the request appears to come from someone in charge, you may jump to act without verification. But legitimate executives typically don’t bypass normal procedures or pressure staff into rushed decisions. A quick call or message through an official channel is all it takes to confirm whether the request is real.
One IT administrator reported that job applicants received calls and messages from scammers impersonating their company, offering fake roles, highlighting how attacker-scraped job-site data can lead to realistic leadership impersonations.
11. Voice cloning and deepfakes
Some of the most advanced vishing scams now use AI tools to recreate voices — or even faces — to make calls or videos sound and look authentic. Attackers blend social engineering with deepfake technology, creating messages that feel personal and urgent.
These tools can replicate speech patterns, accents, and emotional tone, making scams harder to spot. As the technology improves, awareness becomes your best defense. If a message feels scripted, unusually urgent, or “too perfect,” it’s worth slowing down and verifying it independently.
In one case, fraudsters impersonated the CEO of WPP using a fake WhatsApp account, a cloned voice, and a fabricated Teams meeting to try and trick an agency leader into setting up a new business venture.
Emerging tactics and technologies in vishing
Vishing continues to evolve, and attackers these days mix classic tricks with new tech to stay one step ahead. However, understanding what a vishing attack is means you can keep up and see how these tools work behind the curtain.
Emerging vishing tactics and technologies include:
- Caller-ID spoofing: Lets scammers mimic trusted numbers to make their calls look legitimate.
- VoIP services: Make it cheap and easy for scammers to launch calls from anywhere in the world.
- Robocall automation: Allows attackers to send thousands of scripted calls in just minutes.
But the biggest shift comes from AI scams. Voice-cloning tools can replicate real speech patterns with unsettling accuracy, giving scammers the ability to sound like people you know and trust. Some operations even use AI to generate dynamic call scripts that adapt in real time to your responses, making conversations feel natural and unscripted.
These evolving tactics make staying informed more important than ever. The better you recognize the patterns, the easier it is to shut down even the most convincing scam.

How to protect yourself from vishing
Staying prepared is your best defense against unpredictable or misleading calls. Use these tips to safeguard yourself and your data from a vishing scam:
- Verify caller identities: Always confirm a caller’s identity, especially if they request sensitive information. If they provide a call-back number, it may be part of the scam — so don't use it. Instead, search for the company's official phone number and call them to confirm if the call was legitimate.
- Ignore calls from unknown numbers: Although it may be tempting to answer every phone call, simply let them go to voicemail if you don’t recognize the number. Listen to your messages and decide whether to call the person back.
- Trust your instincts and hang up: The moment you suspect a vishing phone call, don't feel obliged to converse politely. Simply hang up and block the number.
- Join the National Do Not Call Registry: Adding your home or mobile phone number to the Do Not Call Registry is free and tells telemarketers you don't want their phone calls. It won't stop people from illegally calling your number, so it’s important to remain vigilant against suspicious calls.
- Use call-blocking features: Enable call-blocking features on your phone to filter out potential vishing scams. Most smartphones offer this function to help you avoid fraudulent calls.
- Use two-factor authentication: Add an extra layer of security to your mobile device and accounts by enabling two-factor authentication.
The tips above can help you identify and avoid vishing attempts while improving your overall cybersecurity.
Common vishing targets
Some people are targeted more often because scammers see an opening — access to money, weaker verification habits, or situations where pressure is likely to work. Knowing where you fit makes it easier to recognize vishing attempts and shut them down quickly.
Common vishing targets include:
- Elderly adults: Phone scams targeting seniors often assume greater trust or less familiarity with rapidly evolving technology.
- Young adults and students: Targeted with fake loans, scholarships, or job offers while juggling tight budgets and busy schedules.
- Remote workers: Approached through fraudulent IT calls or “urgent” company updates, exploiting reliance on phone and digital communication.
- New customers or recent account holders: Scammers take advantage of the confusion that can come with setting up new services, hoping details are confirmed without scrutiny.
- Finance and HR staff: Targeted for access to payroll, invoices, and sensitive employee data.
- Small business owners: Busy schedules and direct access to business accounts make them appealing targets for fake vendor or payment requests.
- Healthcare workers: Pressured with fabricated patient issues or urgent access requests in fast-paced work environments.
- Parents: Manipulated with false emergencies involving their children, often amplified by voice cloning or urgent narratives.
- Hiring managers: Scammers pose as candidates or vendors to gain access to internal systems or collect sensitive information.
What to do if you’ve been vished
When a vishing call slips through, quick action makes all the difference. Here’s what to do when you realize something isn’t right:
- End the call: Hang up immediately and jot down what they asked for, the number displayed, and anything that felt unusual. This helps you stay grounded and gives authorities helpful details.
- Secure your accounts: Update your login details, create a secure password, and review recent activity. If you shared banking or payment information, contact your financial institution so they can protect your accounts quickly.
- Report the incident: File a report with the FTC and your local law enforcement agency (if you lost a substantial amount of money), and report any scam website involved. Reporting helps authorities track patterns and prevents similar scams from reaching others.
Keep you and your phone safe from scammers
Vishing attacks are designed to catch you off guard, but knowing the warning signs helps you stop scams before personal information slips out. Staying informed puts you one step ahead of cybercriminals who rely on urgency and deception over the phone.
For added protection, Norton 360 with LifeLock Select goes further, with a Safe Call feature that helps block scam calls, and a full suite of advanced AI scam protection tools that can help detect scam texts, sites, and deepfake videos. Take the guesswork out of spotting scams — let Norton handle the heavy lifting.
Vishing FAQs
How can I tell if a call is vishing?
You can often spot a vishing call by signs like undue urgency, pressure to act quickly, unexpected requests for personal information, or a caller ID that doesn’t match the pretext. Any call that feels rushed, inconsistent, or off is worth treating with caution.
What should I do if I get a suspicious call?
If you get a suspicious call, hang up immediately. Ending the call prevents the scammer from cloning your voice, steering the conversation, or pressuring you into quick decisions. Then contact the company or agency directly using the phone number listed on its official website to confirm whether the call was legitimate.
What’s the best response to a vishing call?
The safest response to a vishing call is to disconnect right away, block the number, and avoid saying anything that could be recorded or reused later.
What is voice spoofing?
Voice spoofing is when scammers disguise their phone number or imitate someone’s voice to make a call appear trustworthy. The goal is to lower your guard so you’ll share information or follow instructions, making it a common tactic in vishing and other phishing attacks.
What is smishing and vishing?
Smishing (SMS phishing) uses text messages to trick you into sharing information, while vishing relies on phone calls. Both are phone-based scams designed to steal personal or financial details.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.









Want more?
Follow us for all the latest news, tips, and updates.