What is a data breach and why should you care?
A data breach is characterized by intentional, unauthorized access to your personal data, and it can put your identity at risk almost immediately. Thankfully, protecting yourself is simpler than you might think. With smart habits and tools like Norton 360, you can stay ahead of cyberthreats that endanger your private data.

A data breach occurs when your personal information, such as emails, passwords, or financial details, is exposed without your consent. And lately, it’s been happening a lot.
According to a recent Gen Threat Report, overall data breach events rose by nearly 21% in the early months of 2025 alone. Specifically, the number of exposed email addresses due to data breaches increased by 16%, including a massive X data breach that revealed over 200 million accounts and emails.
Learn more about data breaches, including how to avoid a data breach and how to secure accounts after a data breach.
Data breach definition
A data breach is a security incident where confidential or private information, such as emails, passwords, or financial details, is accessed or exposed without authorization.
Data breaches are different than data leaks, which typically occur by accident. For example, a leak can happen when a company leaves a database unsecured online, exposing the information without malicious intent.
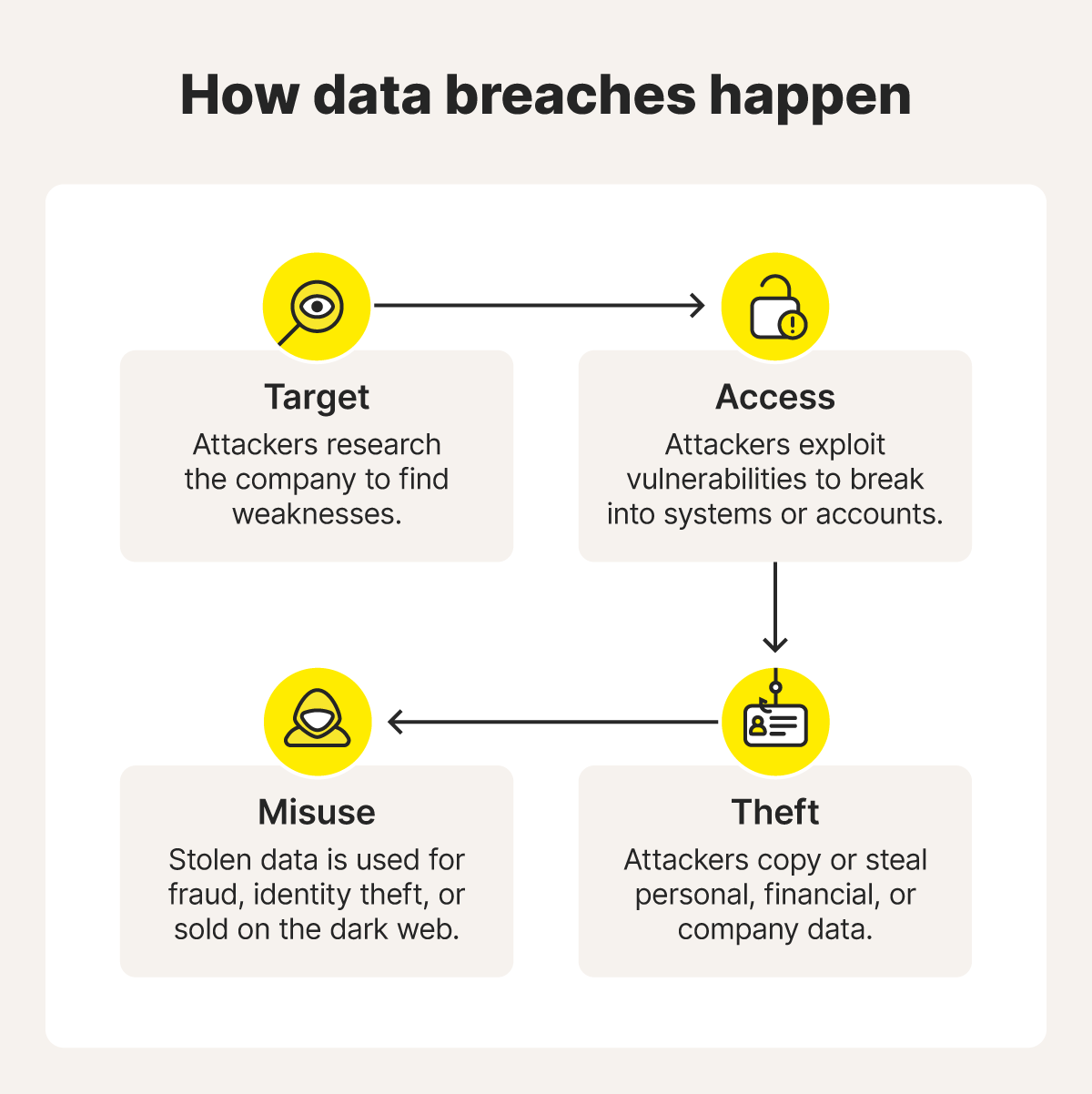
How do data breaches happen?
Data breaches happen when attackers forcibly gain access to sensitive information — often through stolen passwords, malware, or other cyberattacks. Sometimes, mistakes like weak passwords or falling for phishing scams can open the door for cybercriminals, turning simple errors into full-blown breaches.
Let’s take a look at some of the main ways data breaches occur.
Cyberattacks
Cyberattacks are direct attempts by criminals to break into systems and steal data. These often rely on exploiting weaknesses in people or technology. Some common examples include:
- Malware: Malicious software that sneaks into your device and steals or corrupts data. Some malware can run quietly in the background for months.
- Phishing: Includes fake texts, emails, or messages designed to trick you into handing over logins or credit card numbers.
- Social engineering: Cybercriminals often use social engineering to manipulate your trust — say, pretending to be IT support — to get sensitive info.
- Ransomware: A nasty type of malware that locks you out of your files and demands payment for their release. And there are many types of ransomware, too.
- Brute-force attack: A trial-and-error method in which attackers keep guessing passwords until they crack one. The sheer “force” of repeated attempts gives it the name brute-force attack.
- Credential stuffing: Attackers use stolen usernames and passwords from one breach to break into other accounts. This is called credential stuffing.
- Watering hole attack: In a watering hole attack, hackers infect a website frequented by a target group, making it easy to spread malware to many people’s devices at once.
Stolen or lost devices
If your lost or stolen devices aren’t protected with a password, biometrics, or encryption, whoever finds them may be able to gain access to your banking app, private messages, emails, and other personal information. And once your data is in the wrong hands, it’s tough to control where it goes next.
You might use your device as a digital extension of your wallet, like many who use a digital wallet on their phone instead of a physical one. If you don’t lock your devices and they fall into the wrong hands, you’re essentially handing over the keys to your personal accounts. That’s why mobile features like remote wipe and device tracking are more than just nice-to-haves.
Insider threats
Not all data breach threats come from outside. Sometimes, breaches happen because of people on the inside. These can be employees, contractors, or partners who have access to sensitive systems.
This could be intentional, like an employee selling company data, or through negligence, like using weak passwords that let criminals break in. Because insiders are already trusted, their actions don’t always raise alarms right away, making insider threats especially tricky to catch.

Examples of real-life data breaches
Hacker groups don’t play favorites, and even the biggest organizations can slip up. Here are some real-world data breaches that show why staying informed and proactive with your online privacy matters.
23andMe
In late 2023, thousands of users’ accounts, including ancestry, health data, family-tree details, and even some genetic information, were exposed when attackers exploited reused passwords in a credential-stuffing attack.
In the end, the breach directly affected 14,000 user accounts, but led to nearly 7 million indirect exposures due to shared data that was part of the 23andMe’s DNA Relatives sharing feature. Regulators fined 23andMe £2.3 million for weak security. The company later settled a class-action lawsuit in the U.S. for $30 million, while offering identity monitoring and stronger authentication going forward.
Pennsylvania State Education Association (PSEA)
In July 2024, cybercriminals breached the workers and teachers’ union network and exposed sensitive personal, financial, and health data of over 500,000 educators and staff.
News of the incident didn't come out until months later, triggering a wave of concern and multiple lawsuits accusing the union of negligence and delayed notifications.
Meta
Going back to 2018, a massive breach exploited a vulnerability in Facebook’s “View As” feature, exposing nearly 30 million accounts globally. Regulators hit Meta with a hefty €251 million ($263 million) fine for failing to safeguard user data under GDPR standards.
The breach highlighted the importance of strong security measures and prompted Meta to overhaul its privacy and monitoring practices to better protect users going forward.
What are companies doing about data breaches?
Businesses are investing in smarter defenses — like multi-factor authentication, encryption, and VPNs — and stronger training policies to keep personal and financial details out of the wrong hands.
Here are more details about the key steps companies are taking to prevent data breaches and build trust with customers:
- Multi-factor authentication (MFA): MFA adds extra verification steps (like a one-time password sent to your phone) so hackers can’t access your device even if they have your password. Just taking this one step and enabling MFA on your accounts can help prevent hackers from accessing your accounts 99.9% of the time.
- Encryption: Encryption scrambles sensitive data so even if hackers get in, the information looks like gibberish.
- Employee training: Effective training helps staff spot phishing emails and other scams, helping to reduce human error.
- Monitoring tools: Security Information and Event Management (SIEM) platforms or Intrusion Detection Systems (IDS) help detect unusual behavior early, catching suspicious activity before it becomes a full breach.
- Third-party security testing: Companies often bring in cybersecurity experts to stress-test systems and patch vulnerabilities before attackers can exploit them.
- Virtual private networks (VPNs): VPNs offer secure connections between employees and company systems, especially for remote work, to keep in-transit data private.
How to protect your identity in the event of a data breach
After a data breach, your personal details can sometimes end up on the dark web, where criminals buy and sell data like email addresses, Social Security numbers, and banking info.
Hackers may try to open accounts in your name, steal money, or launch targeted scams once they get your details. That’s why it’s important to know how to prevent a data breach from causing lasting damage.
Here are some tips to strengthen your overall data breach prevention plan:
- Change your passwords: Use a secure password that’s unique for each account, and ensure each password is 15 characters or longer. A password manager can help suggest new passwords and keep track so you don’t have to remember them all yourself.
- Enable MFA: Add an extra layer of security with two-factor authentication, or more with MFA, so even if your password leaks, attackers can’t log in without the additional steps.
- Monitor your financial accounts: Keep an eye on credit card and bank activity, and report any unusual charges as soon as you see them.
- Place a fraud alert: Place a fraud alert on your credit report. This makes it harder for cybercriminals and hackers to open new accounts in your name.
- Watch out for phishing scams: Scammers may target you with fake emails or texts. Good phishing protection means double-checking links and never sharing sensitive details with unverified senders.
- Consider identity theft protection: Services like Norton 360 with LifeLock Select can help monitor your personal info across the web, including the dark web, and alert you if your data is spotted.
Protect your data from online threats
Understanding what data breaches are and how they happen is only the first step. The real power comes from knowing how to protect yourself from potentially disastrous effects after a data breach and having the right tools to support you.
Norton 360 with LifeLock Select provides robust protection from online threats with features like Dark Web Monitoring, a VPN, and data breach notifications. You’ll also be entitled to a potential $1 million in coverage if you experience financial loss due to identity theft. Subscribe now and start protecting your personal data against misuse.
FAQs
What should I do if my Social Security number was exposed in a data breach?
If your SSN gets into the wrong hands after a data breach, place a fraud alert or credit freeze with the major credit bureaus, keep an eye on your credit reports, and report any suspicious activity right away. To help minimize this risk in the future, consider identity theft protection services like Norton 360 with LifeLock that can monitor for misuse of your SSN.
Can I sue a company for a data breach?
Yes, in some cases you can. If a company fails to safeguard your data and you suffer damages, you may be able to join a class-action lawsuit or pursue your own claim. Laws vary by region, so it’s best to check with a legal professional.
How can I secure my accounts after a data breach?
Start by changing your passwords to strong, unique ones and enabling multi-factor authentication wherever it’s supported. Then, monitor your accounts for unusual activity and watch for phishing attempts. You can also use a password manager to stay organized and secure going forward.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.









Want more?
Follow us for all the latest news, tips, and updates.