What is a data leak and how can you protect yourself?
If your personal information is compromised in a data leak, cybercriminals could sell your details on the dark web, putting you at risk of identity theft. Get tips on safeguarding your data and see how Dark Web Monitoring, a built-in feature of Norton 360 Deluxe, can help alert you if your personal information is exposed.

A data leak is when sensitive information is exposed by mistake. Unlike data breaches, which are typically caused by cyberattacks, leaks tend to stem from human error or misconfigured systems rather than malicious intent.
A data leak is like a jewelry store employee accidentally leaving the safe unlocked: there are no harmful intentions, but the oversight leaves valuable assets exposed to anyone who happens to pass by.
Data leaks, sometimes called data spills, are one example of sensitive data exposure, and the consequences can be serious. One small oversight can put millions of people’s personal or financial information at risk of fraud, identity theft, and other cybercrimes.
Data leaks in the news
A search and analytics company, Elasticsearch, unintentionally leaked over 100 million records tied to Swedish individuals and companies due to an unsecured server. Compromised data points included full names, dates of birth, address histories, personal identity numbers, debt records, income tax data, and more.
Data leak vs. data breach
Whereas data leaks are accidental, data breaches are intentional and usually malicious. Data breaches usually occur when cybercriminals break into a system, like a database or server, to steal the data from it, for example. Alternatively, a data breach might involve an insider deliberately revealing sensitive information for personal gain.
In other words:
- A data leak is like leaving your phone on the bus and having it end up in a stranger’s hands.
- A data breach is like having your phone stolen from you forcefully in a targeted mugging.
But, whether your information is exposed in a leak or a breach, it can fall into the wrong hands and put your identity at risk.
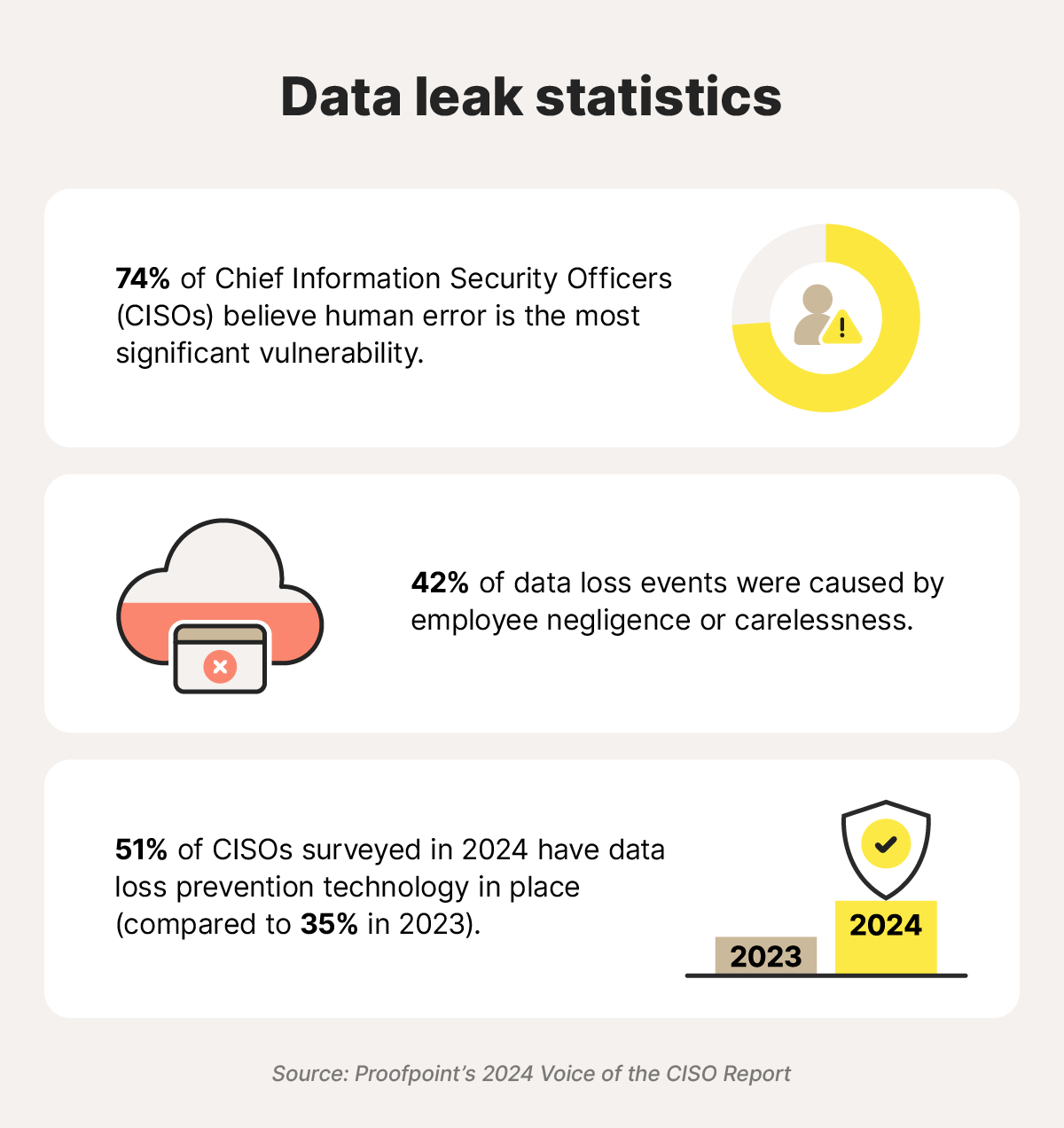

How do data leaks happen?
Data leaks usually stem from internal issues within an organization, such as weak security policies, misconfigured systems, or employees who lack proper training on data protection.
Here’s a more detailed look at how data leaks can happen:
- Human error: Simple mistakes, like copying information into the wrong system or leaving printed documents lying around, can lead to unintentional data exposure.
- Accidentally sharing files: A distracted employee could attach the wrong file to an email, share a link with “anyone can view” permissions, or send documents to the wrong recipient.
- Lost or unsecured devices: Laptops, USB drives, or mobile phones containing unsecured sensitive data can be misplaced or stolen, leaving the door wide open for cybercriminals.
- Misconfigured cloud storage: When cloud services are set up incorrectly, sensitive files may be left publicly accessible. Even highly competent IT teams can accidentally grant broader access than intended, resulting in a data leak.
- Poor access controls: If too many people have access to sensitive information, the chances of accidental exposure go up. Inconsistent access policies often result in data being available to people who don’t need it.
- Outdated software settings: Old systems with poorly configured settings can expose data — even without a hacker leveraging zero-day flaws. For example, an application might log sensitive information without proper encryption.
- Careless vendors: Even if an organization has strict cybersecurity policies, third-party vendors or contractors who lack proper security training can mishandle sensitive information.
How do I know my data’s been leaked?
Often, you won’t realize your data has been leaked until it’s too late. The first signs of a data leak could include unusual account activity, hacked logins, or even identity theft.
While companies are obliged to notify you of data leaks and breaches, they may drag their heels. Dark web monitoring tools can help you find out if your data has been compromised sooner.
Norton 360 Deluxe includes a dark web monitoring feature that scours the murkiest corners of the internet for your personal information, alerting you if it’s found. The tool can monitor for a wide range of data, including phone numbers, credit card numbers, Social Security information, and even gamertags. The earlier you detect exposure, the faster you can take action to protect your accounts and identity.
What types of data are at risk in personal data leaks?
Data leaks can involve just about any information stored online, including your name, date of birth, Social Security number, health information, login credentials, or company secrets. Cybercriminals can then exploit this data for fraud or sell it on the dark web.
Here’s a closer look at the types of leaked data cybercriminals are most likely to take advantage of, and the potential consequences of this data being exposed:
Personally identifiable information
This could include your email, full name, date of birth, address, phone number, driver’s license number, Social Security number — in short, any data point, or set of data points, that could be used to identify you.
Potential consequences: More spam, targeted phishing attacks, social engineering attacks, doxxing, swatting, or even identity theft.
Login credentials
Login credentials like usernames, passwords, and answers to security questions for online accounts are among the most commonly leaked data. SIM card PINs are a more exotic example.
Potential consequences: Account takeovers, credential stuffing attacks, or SIM swap attacks.
Financial data
Financial data exposed in leaks could include bank account numbers, credit card details, debit card PINs, and tax records. Anything that offers access to financial accounts or funds is valuable to cybercriminals.
Potential consequences: Funds stolen directly from your accounts, banking account takeovers, credit fraud, or tax fraud.
Health records
Leaked health records could include your medical history, prescriptions, insurance details, and lab results.
Potential consequences: Medical identity theft.
Work-related data
This could include client lists, trade secrets, intellectual property, confidential internal documents, and other industrial secrets.
Potential consequences: Competitive disadvantage, reputational damage, blackmail, regulatory fines, loss of customer trust, job loss.
Behavioral data
Leaked behavioral data like your browsing history, online purchases, location information, and other aspects of your digital footprint are a gold mine for cybercriminals.
Potential consequences: Targeted scams, phishing, cyberstalking, malvertising.
How to protect yourself from data leaks
You can help protect yourself from the consequences of data leaks by securing your accounts with 2FA, limiting who you share information with, and learning what to do after a data leak or breach. Here’s a more detailed breakdown of our top tips.
- Turn on two-factor authentication: Set up two-factor authentication (2FA) to help prevent account takeovers if your account credentials are leaked. With 2FA or MFA enabled, cybercriminals would need both your password and access to your phone or email account, making it much harder for them to break in.
- Don’t reuse passwords: Create strong, unique passwords instead of reusing passwords across multiple accounts. Consider a password manager to help store and create these credentials.
- Be cautious with what you share: Before signing up for an online account, consider whether you really need to provide all the requested information: a free gaming account might not need your full name. Sharing less helps reduce your exposure.
- Delete old accounts: Check old accounts you don’t use anymore, and see if you can request that your personal information be removed. Learn how to delete your accounts on popular social media platforms like X, Facebook, and Instagram.
- Keep systems up to date: Updating your software and devices can patch security vulnerabilities to defend against exposed connections, which could result in a leak. Enable automatic updates where possible.
- Monitor your accounts and credit: Set up notifications for your bank accounts and use credit monitoring services to get alerts about unusual activity. This helps you take quick action should a data breach or leak occur.
- Set up dark web monitoring: Get Norton 360 Deluxe so you can see if somebody ends up selling your data on the dark web. Knowing when this occurs will help you take action to defend yourself.
Defend against the fallout of data leaks
Data leaks may result from accidents, but that doesn’t make them any less dangerous. Their potential repercussions could range from more spam to account takeovers and even identity theft. The sooner you’re alerted to sensitive data exposure, the faster you can take action to protect your digital identity.
Stay on top of the risks posed by data leaks with powerful dark web monitoring from Norton 360 Deluxe. You’ll also get a password manager, a secure VPN, and award-winning malware protection for 360-degree protection of your digital life.
FAQs
Can I sue a company for leaking my data?
You may be able to sue a company if your data was exposed due to their negligence. Legal outcomes depend on factors like the type of data leaked, the company’s security practices, and local data protection laws. Consult a legal expert to understand your rights and potential next steps.
How serious are data leaks?
Data leaks can be extremely serious. They can lead to identity theft, fraud, or further security breaches. Even seemingly harmless details can be pieced together by cybercriminals for malicious purposes.
What is an iPhone data leak?
An iPhone data leak refers to the unintended exposure of personal information from an iPhone. This could be caused by software vulnerabilities, misconfigured settings, or app permissions. Keeping your iPhone updated and reviewing privacy settings can help reduce the risk.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.









Want more?
Follow us for all the latest news, tips, and updates.