IP spoofing: What is it and how does it work?
Cybercriminals can cover up their crimes using IP spoofing — an advanced technique that lets hackers remain undetected while they infiltrate systems and steal sensitive data. In this guide, we’ll break down what IP spoofing is, how it works, and how Norton 360 can help protect you from stealthy cyber threats.

Hackers use IP spoofing to disguise the true source of internet data, allowing malicious traffic to bypass security measures and deceive systems into trusting fraudulent connections. This tactic is commonly used in a range of dangerous cyber attacks, and it was even used in 2024 to compromise the ultra-secure Tor network.
Understanding IP spoofing and how it works is crucial to recognizing potential threats and proactively safeguarding your devices and data.
What is IP spoofing?
IP spoofing is a technique used to fake the source IP address of data packets, masking their true origin. By manipulating this information, hackers can impersonate trusted devices, evade security measures, and execute malicious activities, such as network breaches, data theft, or sophisticated Denial of Service (DoS) attacks.
When data is transmitted over the internet using TCP/IP protocols, data packets include source and destination IP addresses, enabling devices to recognize and respond to legitimate requests. In an IP spoofing attack, the source IP is falsified, making it appear that malicious requests come from a trusted source.
How does IP spoofing work?
IP spoofing works by altering the source IP address attached to data packets. Attackers modify the packet’s IP header at the network layer, forging a trusted address. The spoofed packets are then accepted as legitimate, enabling cybercriminals to bypass network and device security, access data, or launch attacks.
Here’s a detailed look at how IP spoofing attacks work in practice:
- Packet creation: The attacker generates an IP packet using specialized software or scripting tools, or intercepts data traveling across networks using packet sniffing tools.
- IP header modification: The attacker alters the packet’s source IP address, replacing it with a trusted or random address.
- Packet transmission: The spoofed packet is sent across the network as usual.
- Packet arrival: The target system accepts the packet, falsely identifying it as being from a trusted source.
- Attack execution: The attacker uses the spoofed network access to spread malware or perform other forms of attack.
- Avoiding detection: Because the source IP is falsified, it’s difficult to track the attacker’s real location or identity.
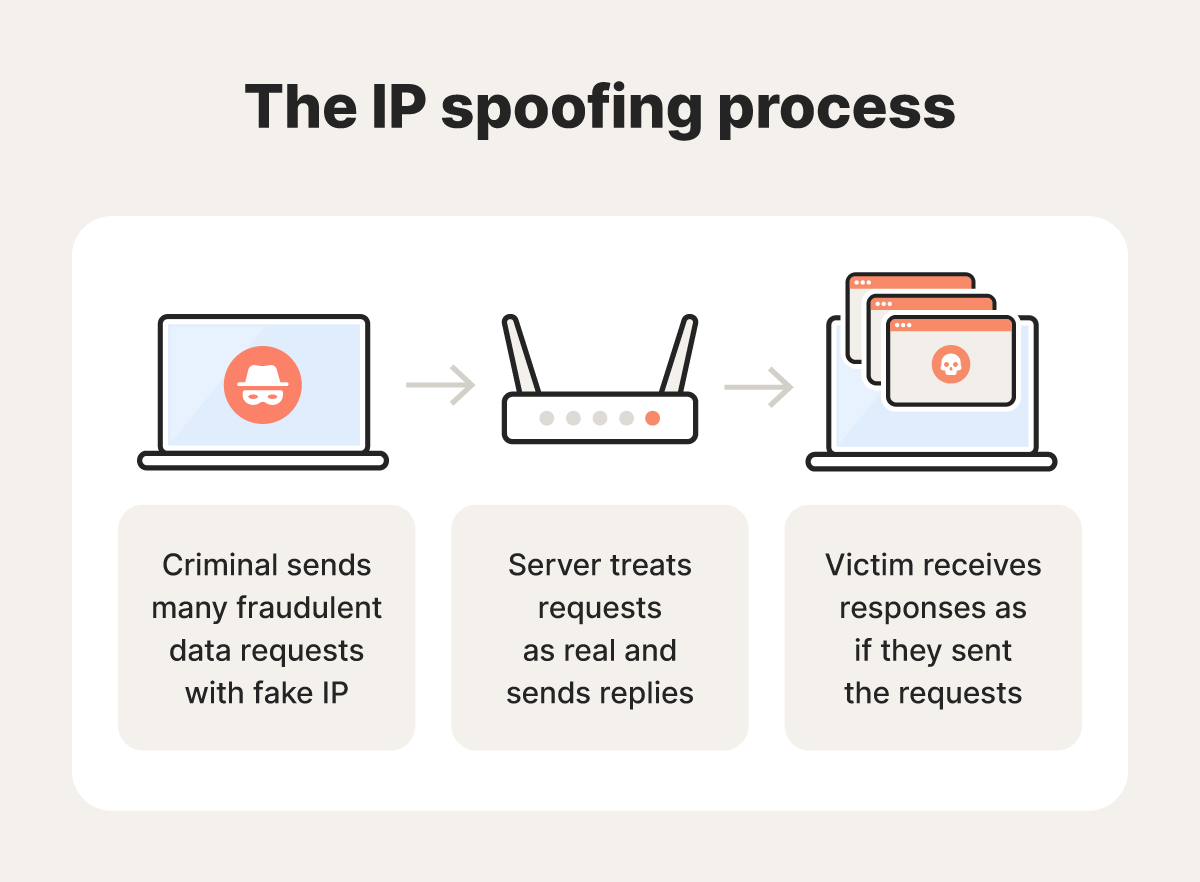

Types of IP spoofing attacks
IP spoofing attacks can facilitate a wide range of specific attacks including botnets, DDoS, man-in-the-middle, and DNS spoofing. These attacks compromise network security and can result in data breaches, service disruptions, and financial losses.
Here’s a closer look at some of the main types of IP spoofing attacks:
Botnet attacks
Botnet attacks use networks of compromised computers to launch coordinated attacks with spoofed IP address data to conceal the true source. Like a puppet master controlling multiple puppets, attackers remotely command these botnets to flood websites, distribute spam, or spread malware across networks.
DDoS attacks
In DDoS (Distributed Denial-of-Service) attacks, cybercriminals use IP spoofing to generate and disguise massive amounts of fake traffic, overwhelming a target server or network. By forging source IP addresses, attackers make it difficult to filter out malicious traffic from legitimate requests or trace the attack’s origin.
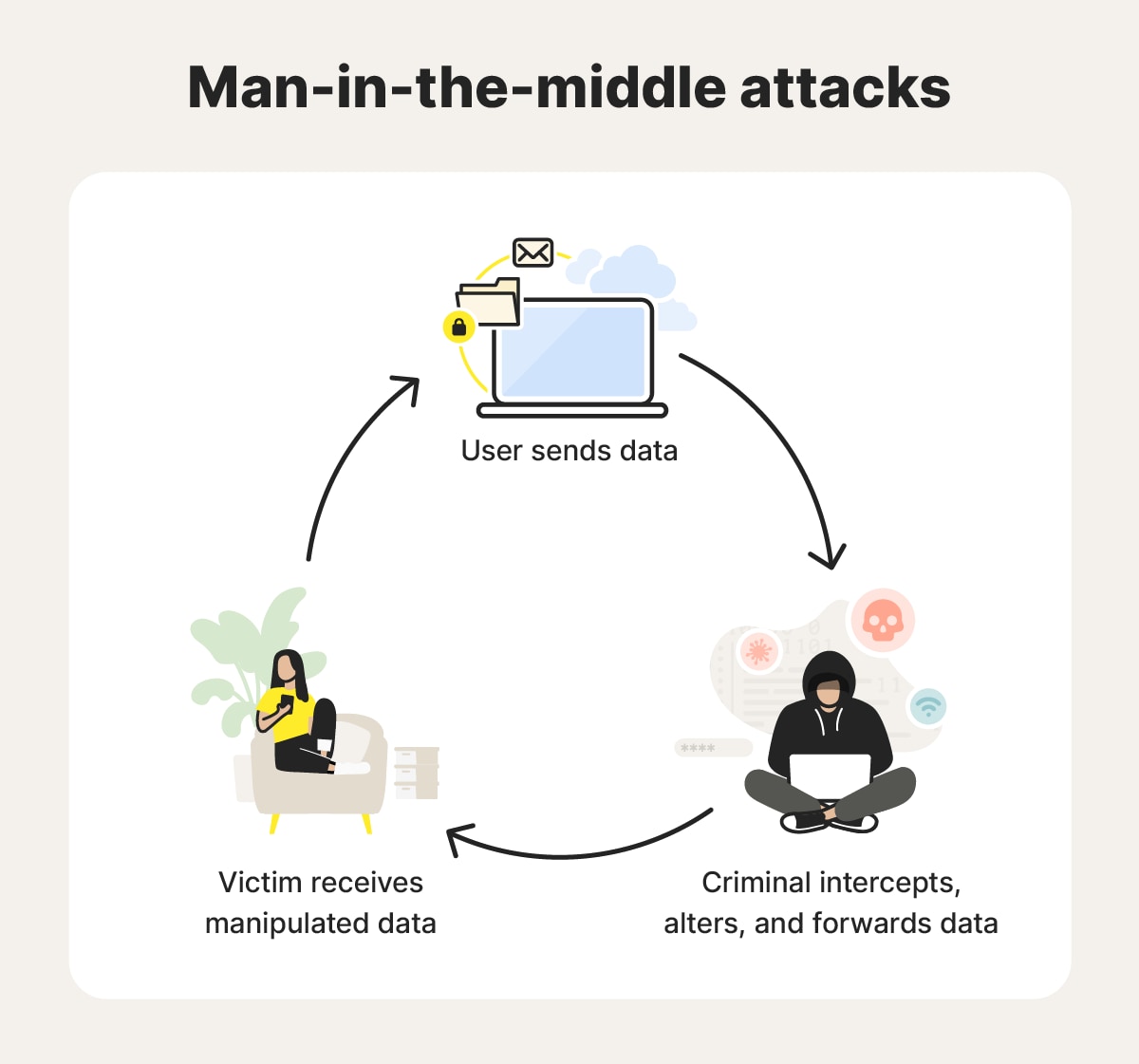
Man-in-the-middle attacks
Man-in-the-middle attacks allow hackers to intercept and alter network communications between two parties. By forging source IP addresses, attackers can redirect traffic, inject malicious content, manipulate transactions, and steal sensitive data that could lead to identity theft.

DNS spoofing attacks
In DNS spoofing attacks, IP spoofing is used to forge secure DNS responses, redirecting users to malicious websites instead of legitimate ones. Attackers alter packet headers to impersonate trusted DNS servers, tricking victims into entering sensitive information on fake sites. This tactic is commonly used to spread viruses and launch phishing attacks.
Real-world examples of IP spoofing
IP spoofing can affect anyone, from large organizations to individuals, and is often deployed as part of other attacks designed to steal information, crash systems, or create backdoors.
Here are a few real-world examples of IP spoofing:
- GitHub (2018): GitHub was hit by one of the largest recorded DDoS attacks up to that point, which was executed by spoofing GitHub’s IP address and sending data to several servers. It sent up to 126.9 million packets per second, crashing GitHub’s site for 20 minutes.
- Various banks (2019): Bank of America, JPMorgan Chase, and SunTrust were targeted by attackers who made it appear as if the banks’ IPs were malicious by sending large volumes of spoofed traffic.
- Django (2023): Django, a popular toolkit used by companies like Mozilla, had an IP spoofing bug that allowed users to circumvent brute-force defenses on login and one-time password pages, leading to compromised accounts.
How to detect IP spoofing
Detecting IP spoofing involves monitoring network traffic for irregularities, such as unexpected or inconsistent source IP addresses. Tools like intrusion detection systems and firewalls with ingress filtering act as checkpoints, analyzing incoming data packets for anomalies in packet headers or unusual behavior.
Among an array of sophisticated Cyber Safety tools, the Norton 360 Deluxe arsenal includes a built-in firewall that works alongside the proactive Intrusion Prevention System to provide robust network-based protection that can help block malicious IP spoofing attacks before they reach your system.
How to prevent IP spoofing
While you can’t prevent IP spoofing completely, you can help thwart IP spoofing attacks and mitigate their impact by setting up a firewall on your router or other network devices, using a VPN to encrypt your internet traffic, and practicing good cyber hygiene practices.
Here’s how you can help shield yourself against IP spoofing attacks:
- Set up firewall filtering: Configure firewalls to help filter out packets with invalid or spoofed IP addresses, blocking suspicious traffic before it compromises your network.
- Use a VPN: VPNs use IPSec and other VPN protocols to encrypt your internet connection, making it practically impossible for attackers to intercept or manipulate the data you send and receive.
- Use strong security software: Install reliable antivirus security software to detect and block malicious activities in real time, and keep malware off your device.
- Update your software: Regularly update all software, including security patches, to fix vulnerabilities that attackers could exploit to launch IP spoofing or other attacks.
- Use strong passwords: Employ complex, unique passwords and enable 2FA to protect your network devices and accounts, making it harder for attackers to gain access through credential stuffing.
- Monitor your network: Review your router’s activity page or ISP app for suspicious network activity. Suspicious traffic coming out of your computers is a sign that one of them might be part of a remote botnet.
Is IP spoofing legal?
IP spoofing itself is not illegal — there’s no law against altering the IP header in data packets. But using it for malicious purposes such as launching DDoS attacks, hacking systems, or stealing data is a cybercrime.
Legitimate uses of IP spoofing include website stress testing, load balancing, network performance evaluation, and debugging. It’s also used during penetration testing to simulate attacks and identify network vulnerabilities.
The best way to quickly, easily, and (in most countries) legally change your IP address is with a VPN, which works by routing all your internet traffic through a secure, encrypted tunnel to a VPN server, assigning your internet activity a virtual IP address that masks your actual IP address.
Protect yourself against IP spoofers
Cybercriminals use IP spoofing to infiltrate networks, steal data, and spread malware. Leaving your device exposed makes it easier for them to attack — that’s where Norton 360 Deluxe comes in.
Norton 360 Deluxe provides advanced protection, helping block malicious traffic with its Smart Firewall, encrypt your connection with a powerful VPN, and shut down malware threats with advanced, real-time antivirus scanning. Secure every angle with Norton 360 Deluxe today.
FAQs
Can IP spoofing be traced?
Tracing IP spoofing is difficult, but security experts using packet analysis, network forensics, and traffic logging to detect anomalies and trace attack patterns can sometimes identify the true source of IP spoofing attacks — especially when combined with law enforcement and Internet Service Provider cooperation.
Can IP spoofing be stopped?
While IP spoofing can’t be fully eliminated or avoided, the threat can be greatly minimized by using firewalls, packet filtering, network monitoring, and intrusion detection systems to help block spoofed traffic. Using a VPN to encrypt your internet traffic also helps prevent the data you send and receive from being tampered with.
What is the difference between IP spoofing and using a VPN?
IP spoofing involves manipulating internet data with fake source IP addresses to deceive networks, systems, or devices, often for malicious purposes. A VPN, on the other hand, securely routes your traffic through an encrypted tunnel, masking your real IP for enhanced privacy and security.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.









Want more?
Follow us for all the latest news, tips, and updates.