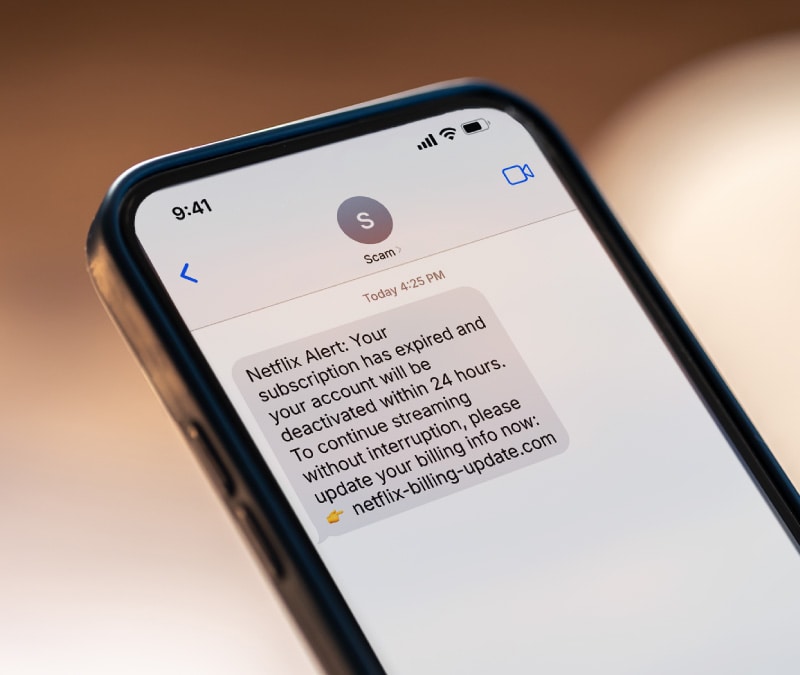
Amazon scams to look out for
The FBI is warning about a huge surge in account takeover fraud, and many attacks target Amazon customers. Learn how to spot Amazon scams for a safer online shopping experience.
Updated December 11, 2025























































Want more?
Follow us for all the latest news, tips, and updates.